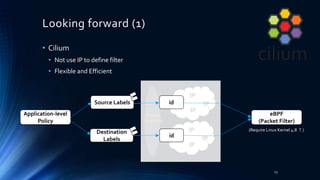
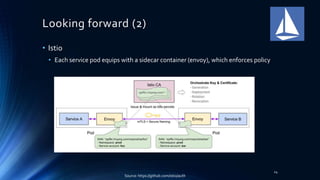
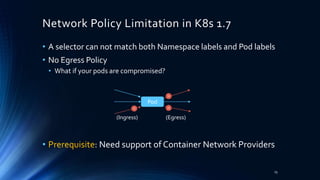
This document discusses network security and policies in Kubernetes. It provides 3 use cases of applying network policies to control communication between pods. It also discusses limitations of current network policy implementation and promising technologies being developed, such as Cilium, that can provide more flexible policy enforcement that is not dependent on IP addresses. The key takeaway is that while network policies can whitelist communication, the implementation has limitations and security needs to keep pace with the dynamic nature of containers and Kubernetes.





![Note:
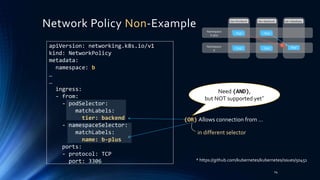
• Not standard k8s Network Policy
• Run with calicoctl, instead of kubectl
• Calico also supports Egress policy (not
shown here)
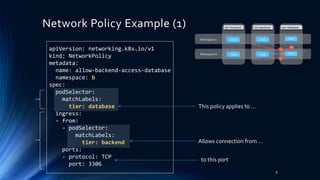
Calico’s Policy Definition
17
Pod
Pod Pod
Pod
Pod
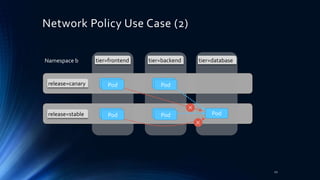
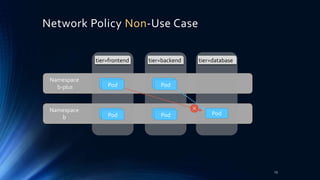
tier=frontend tier=backend tier=database
PodPod
PodPod
Namespace
b-plus
Namespace
bapiVersion: v1
kind: policy
metadata:
name: allow-b-plus-backend-access-b-database
spec:
selector: >
calico/k8s_ns == 'b' &&
tier == 'database'
ingress:
- action: allow
source:
selector: >
calico/k8s_ns == 'b-plus' &&
tier == 'backend'
protocol: tcp
destination:
ports: [3306]
# calicoctl apply -f <FILENAME>](https://image.slidesharecdn.com/networkpolicypublic-170924101255/85/Network-policy-k8s-day-17-320.jpg)