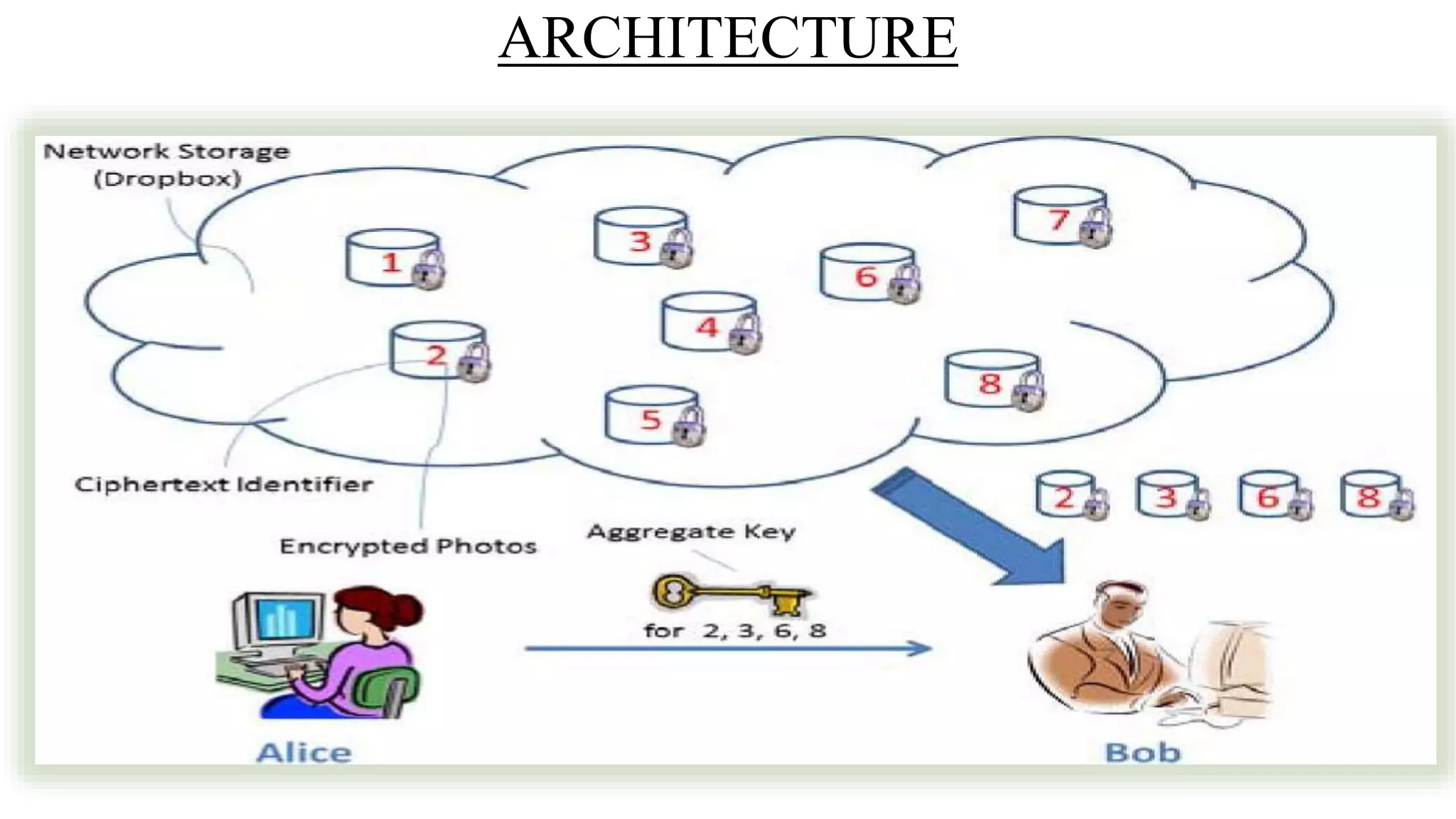
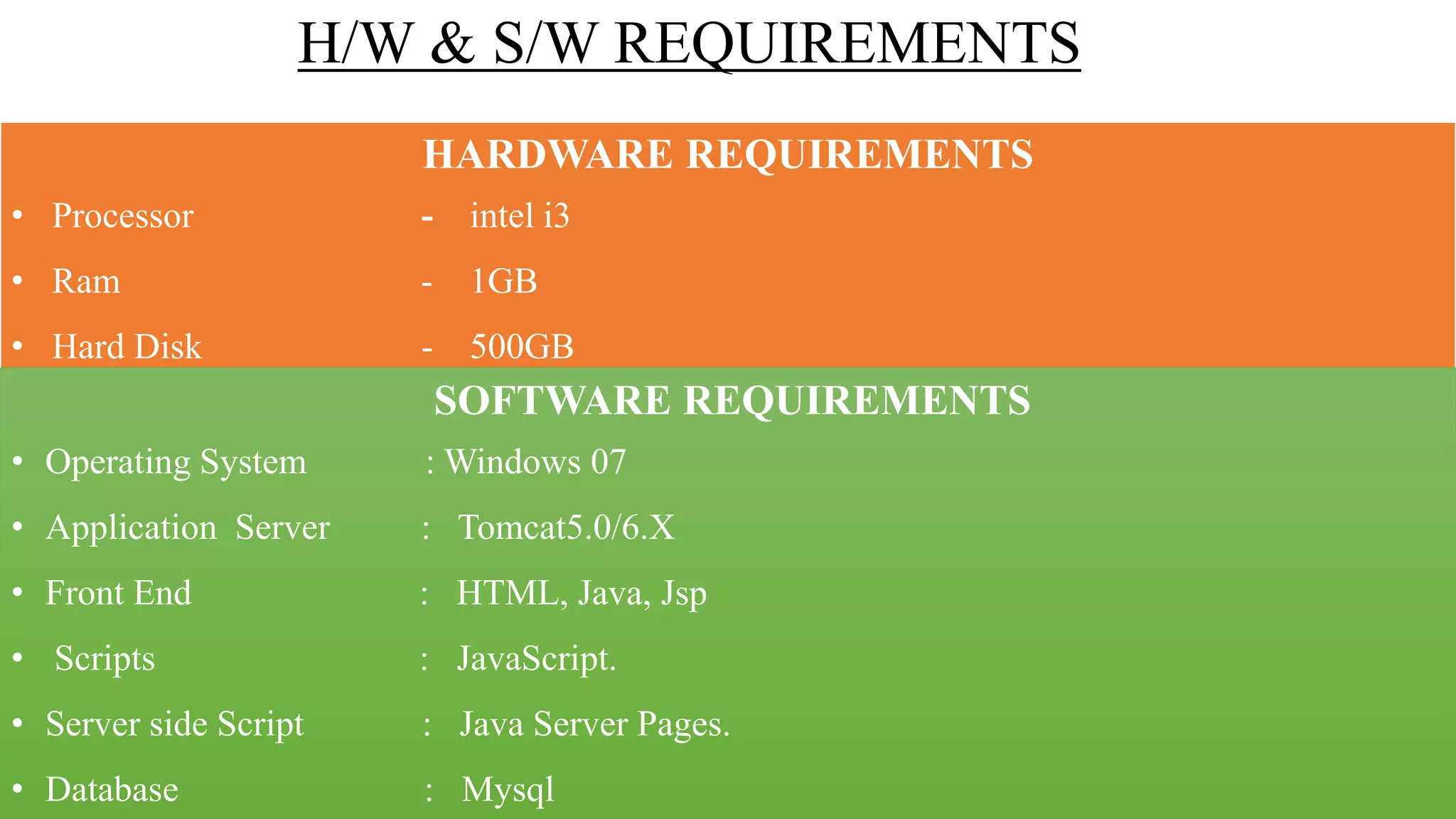
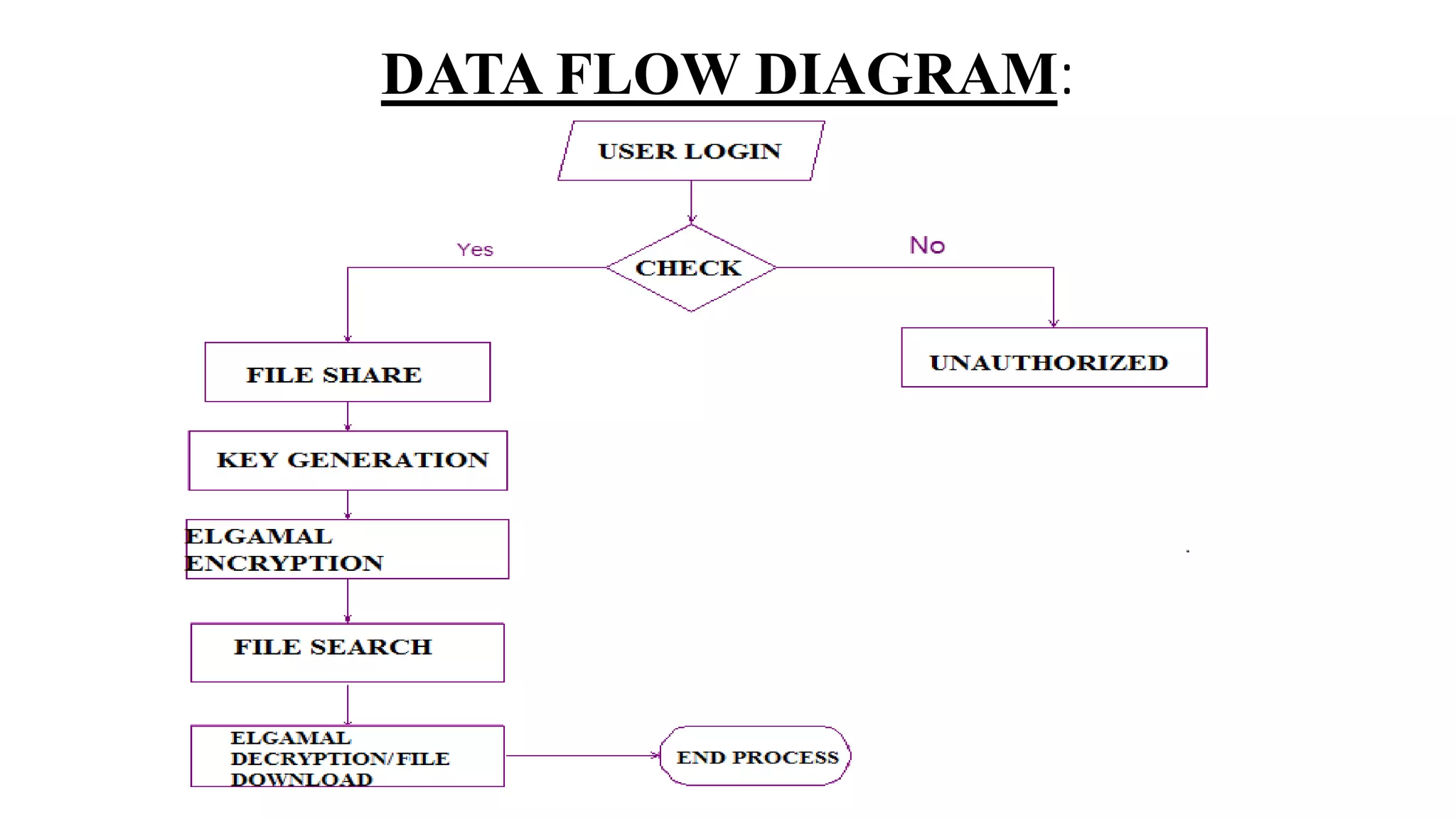
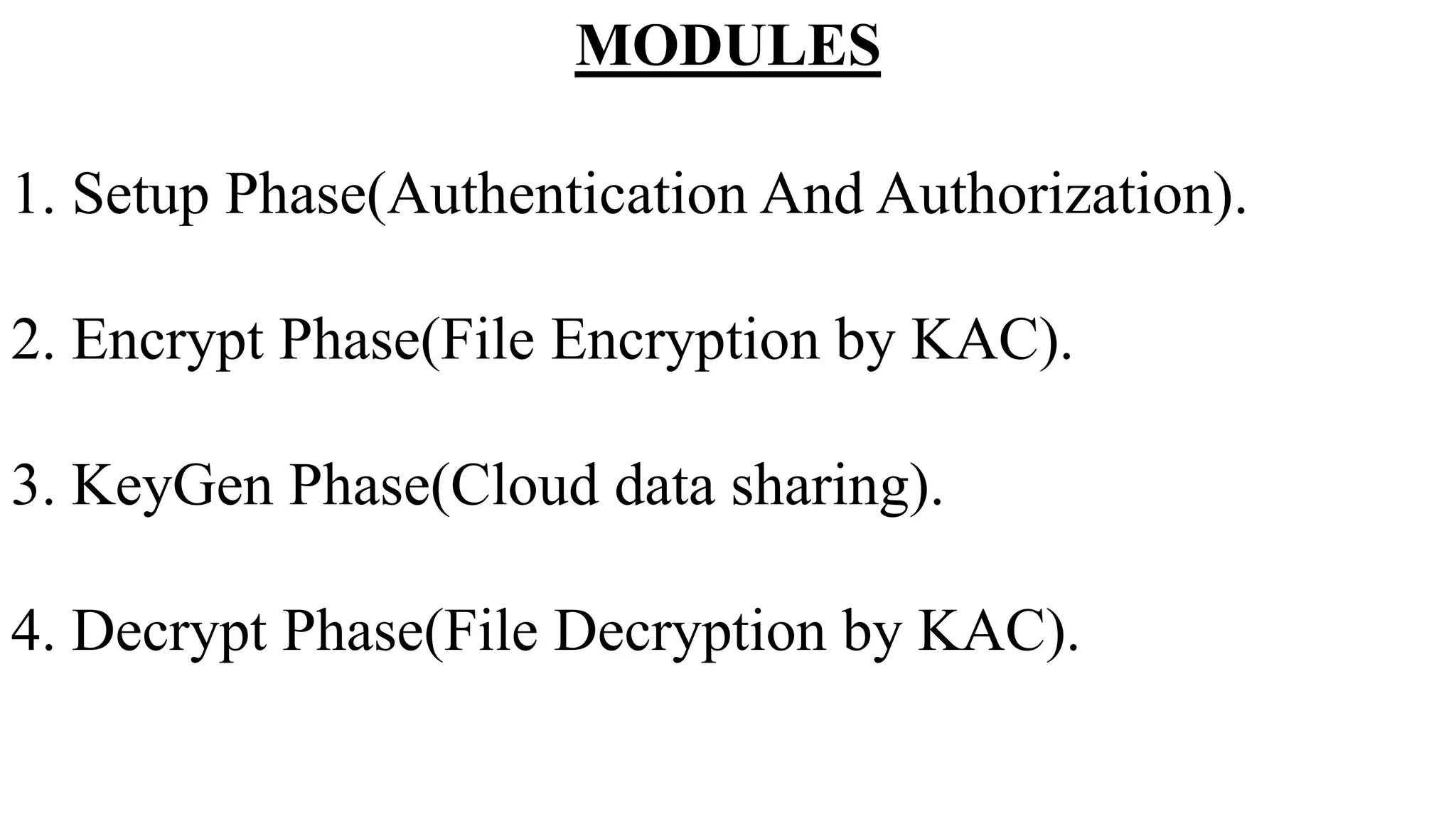
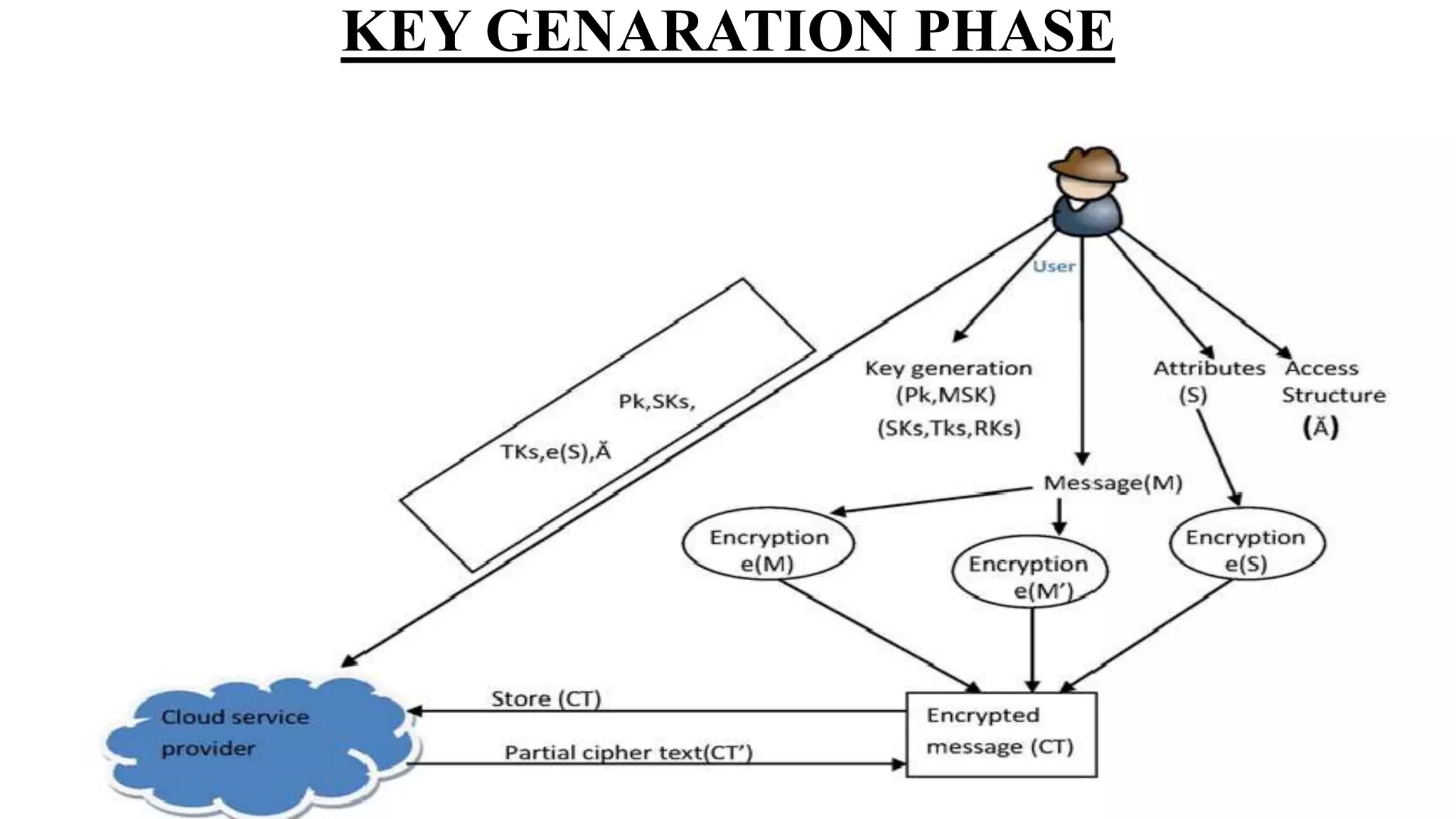
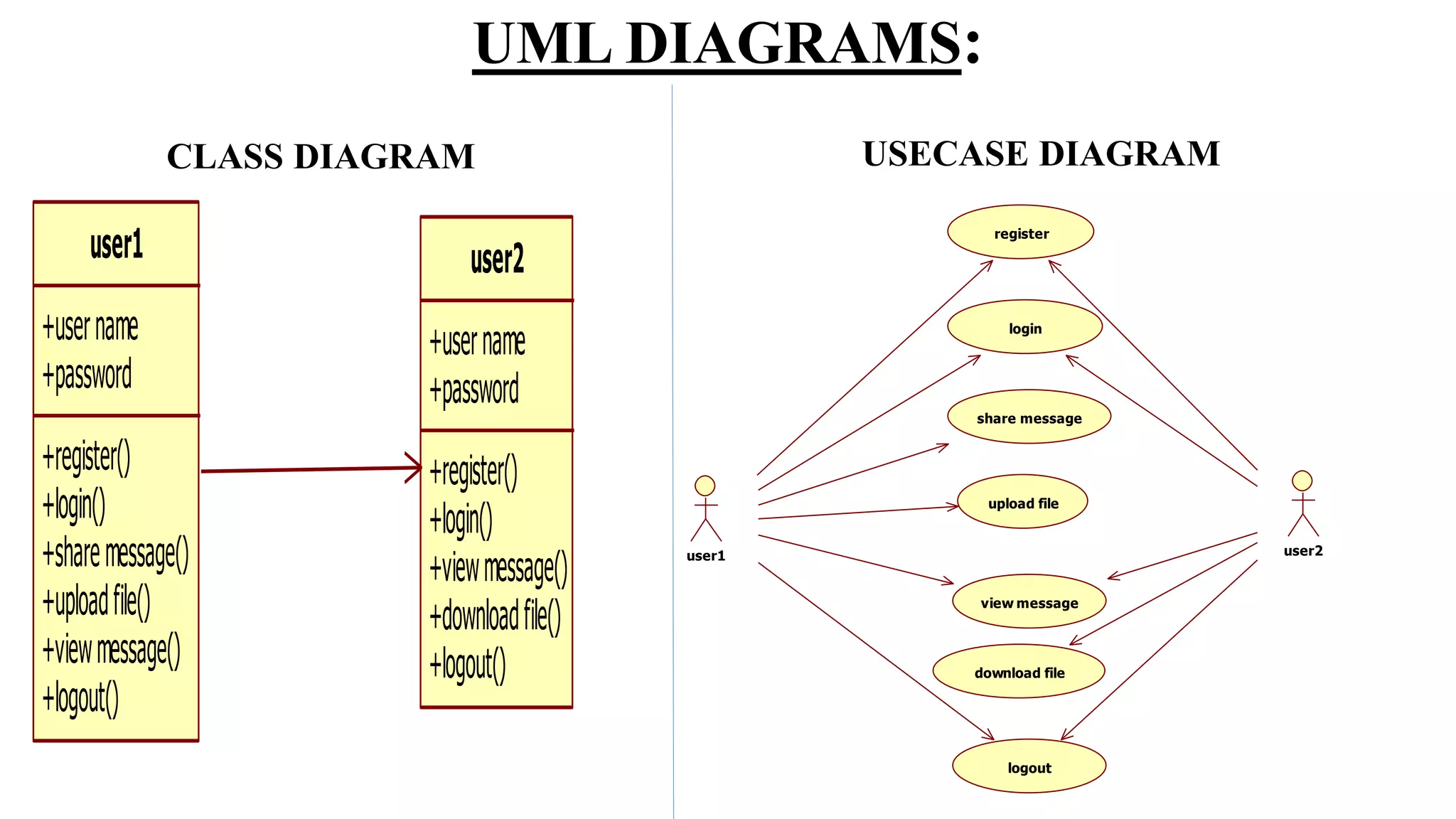
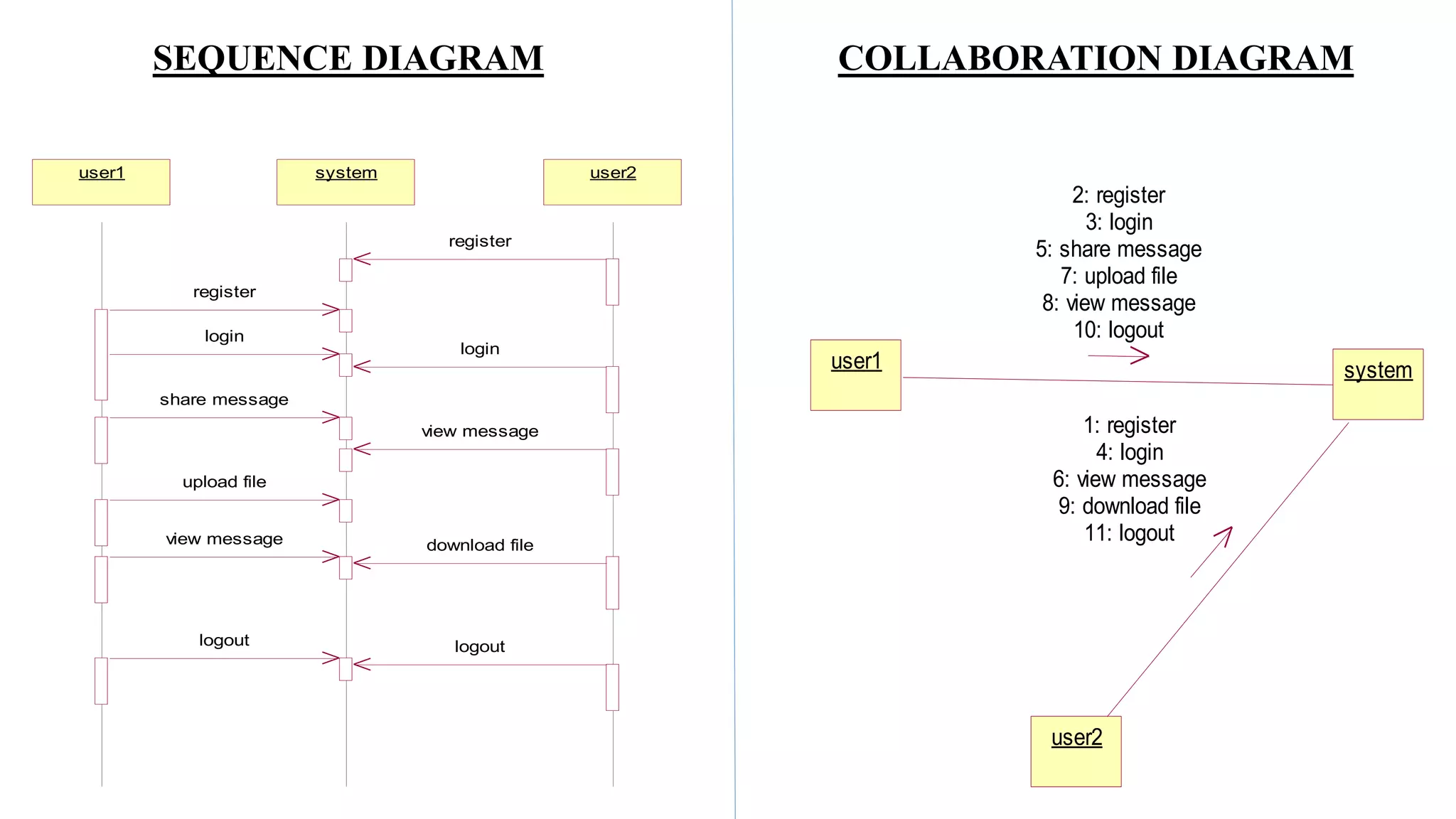
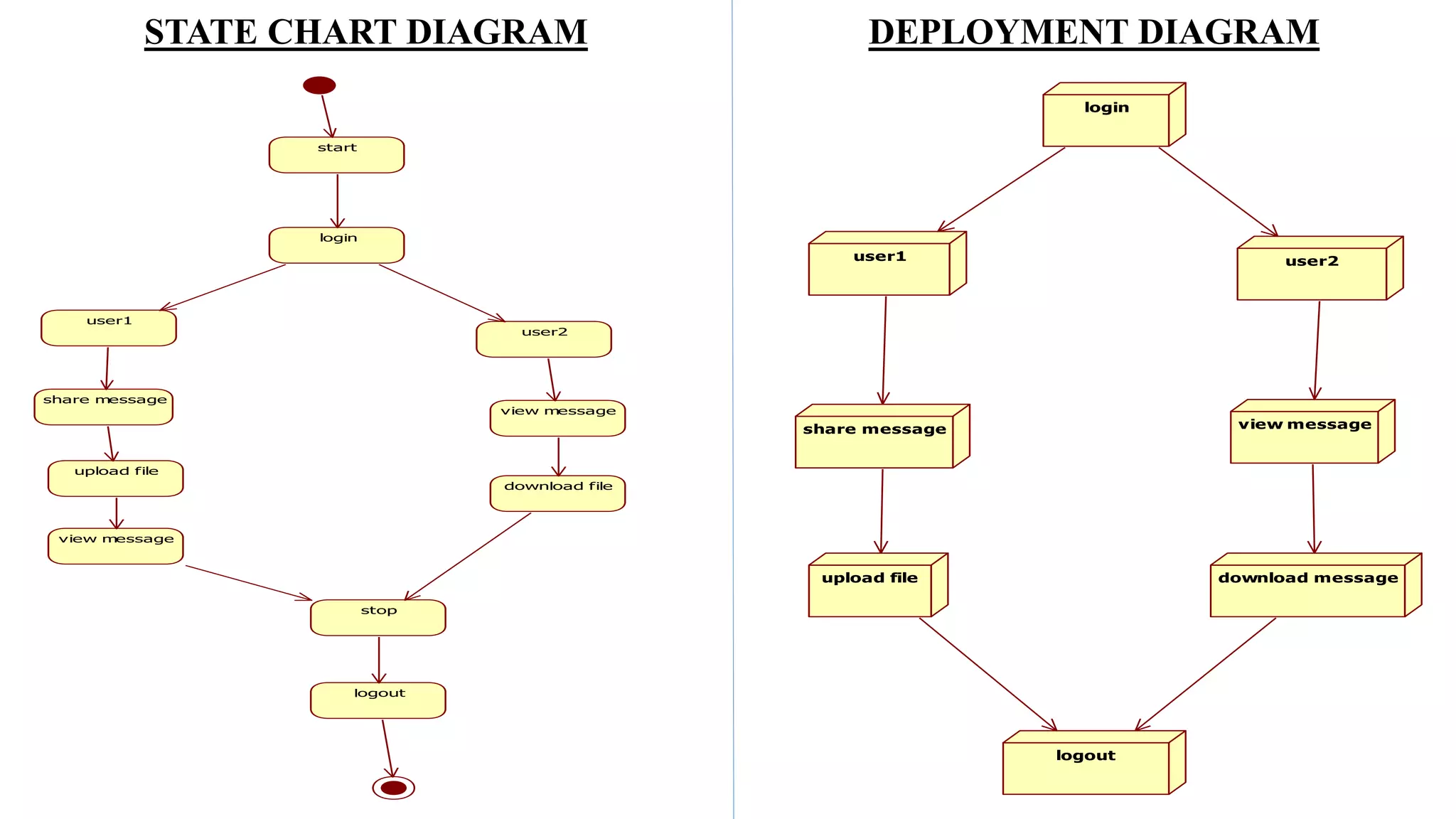
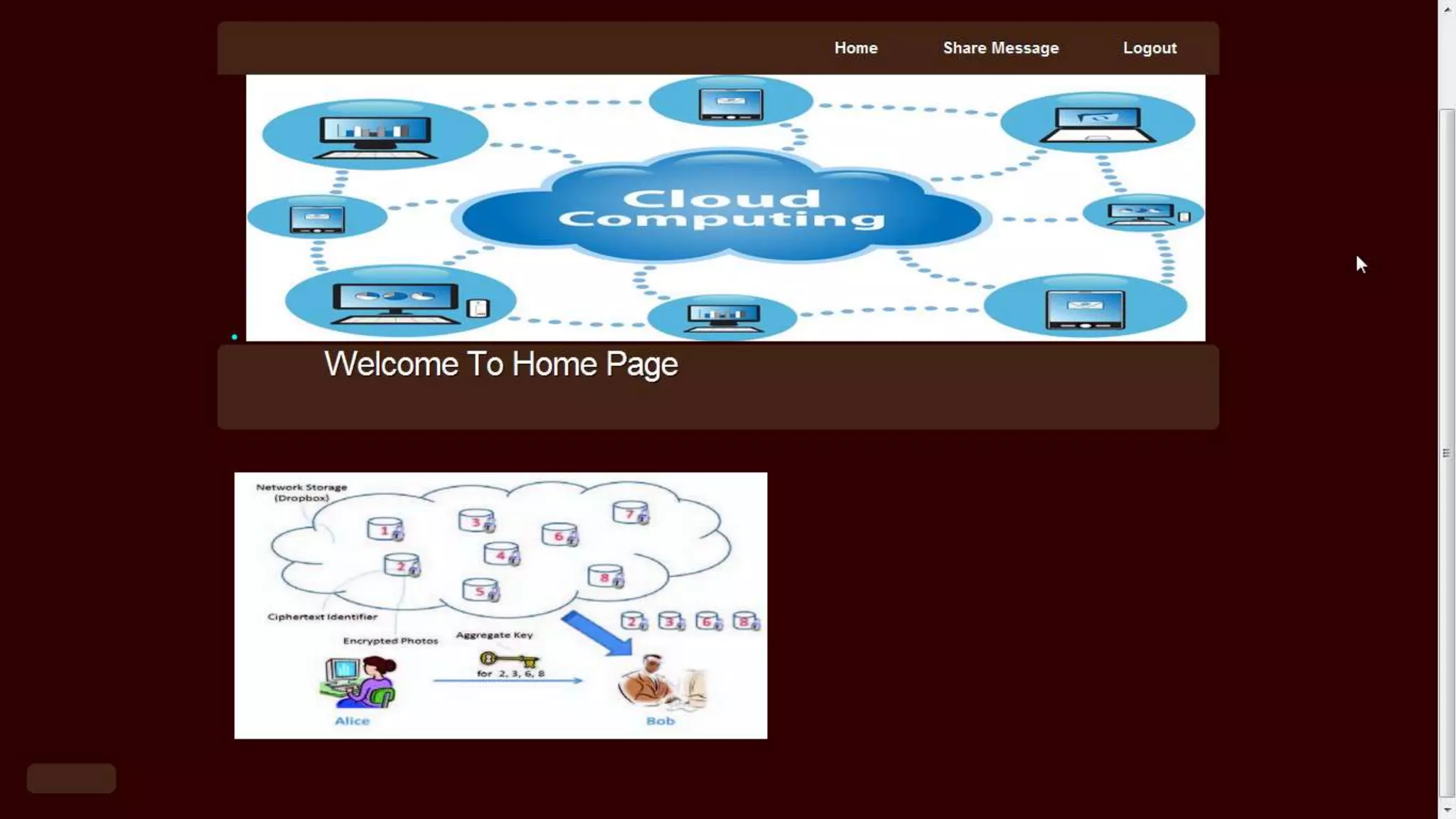
The document proposes a new key-aggregate cryptosystem (KAC) for secure and efficient data sharing in cloud storage. KAC allows encrypting data under a public key and identifier, and extracting an aggregate secret key from a master secret key. The aggregate key is compact yet provides decryption power for any subset of ciphertexts. This allows flexible delegation of decryption rights by sending a constant-sized aggregate key for sharing encrypted data on cloud storage. Formal security analysis is provided for the cryptosystem in the standard model.