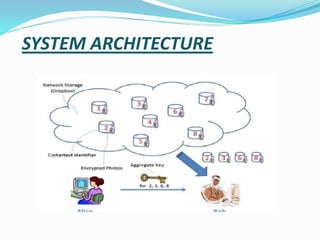
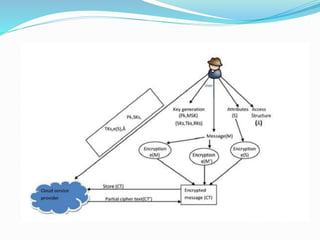
This document presents a proposed system for secure and flexible data sharing in cloud storage. It describes using new public-key cryptosystems that can aggregate any set of secret keys into a constant-size ciphertext. This allows flexible sharing of encrypted data through an aggregate key that decrypts multiple ciphertexts without increasing in size. The system architecture includes setup, encryption, key generation, and decryption phases. The proposed system aims to address limitations in existing approaches regarding key sizes and flexibility of data access delegation.