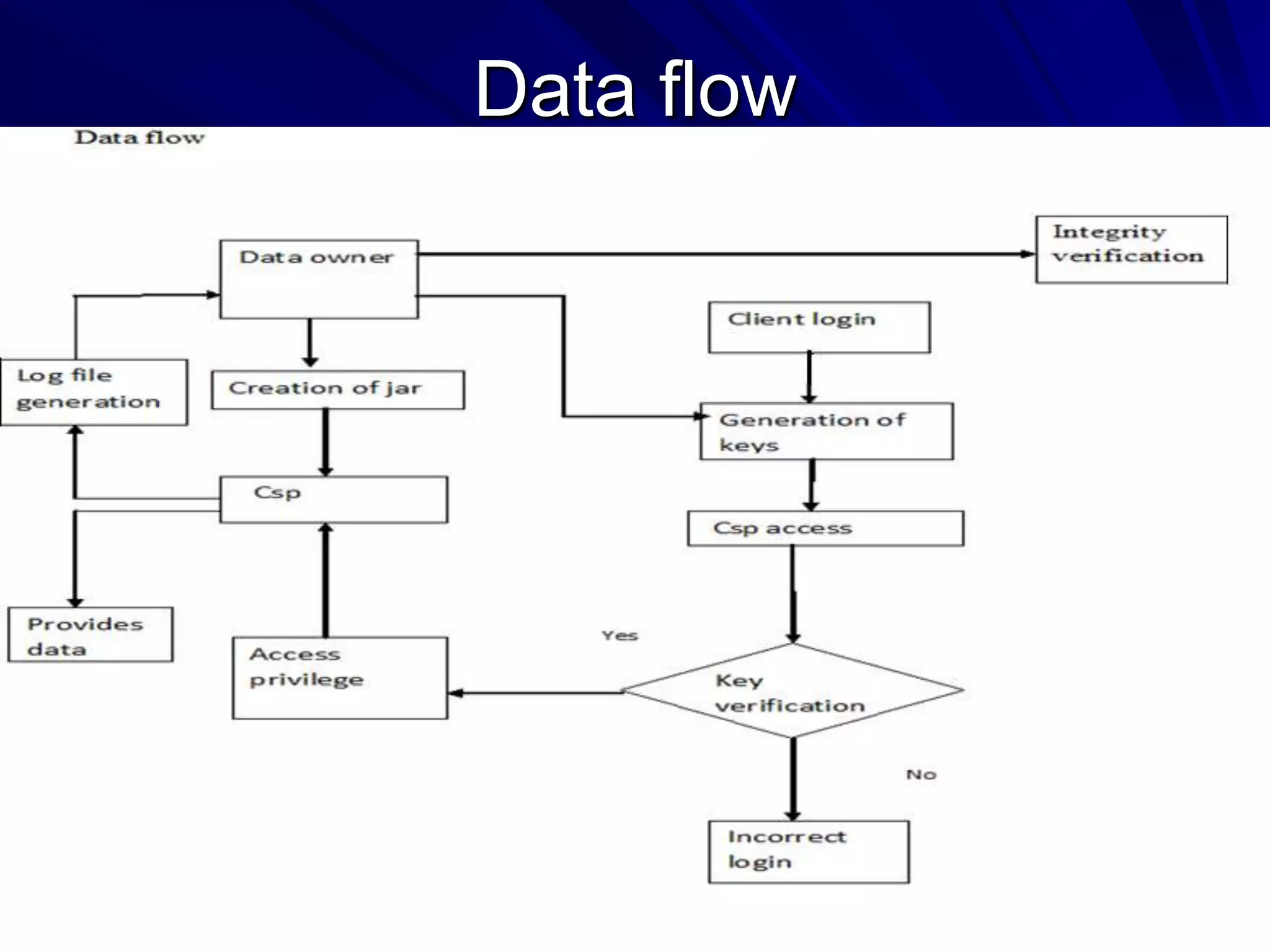
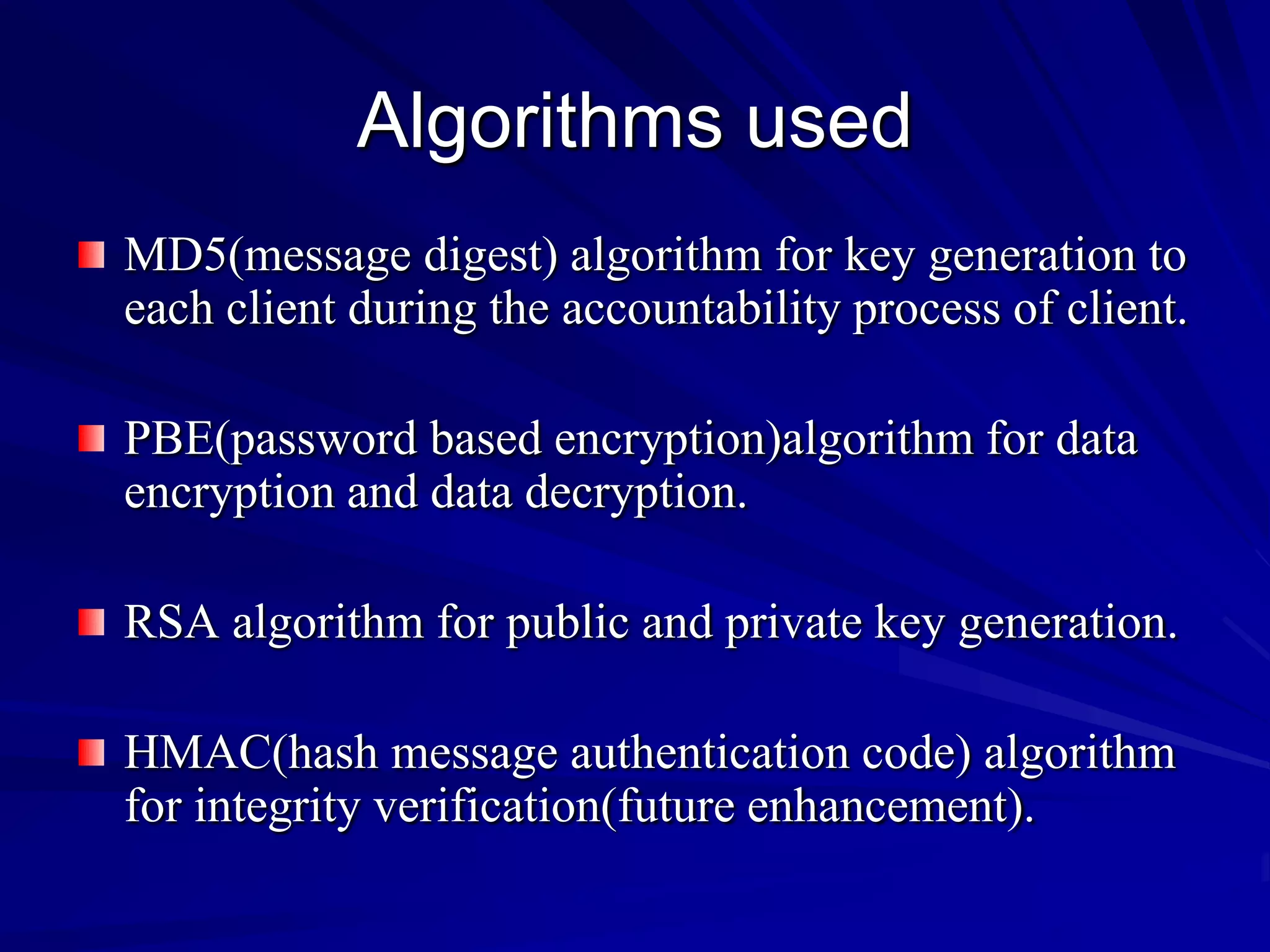
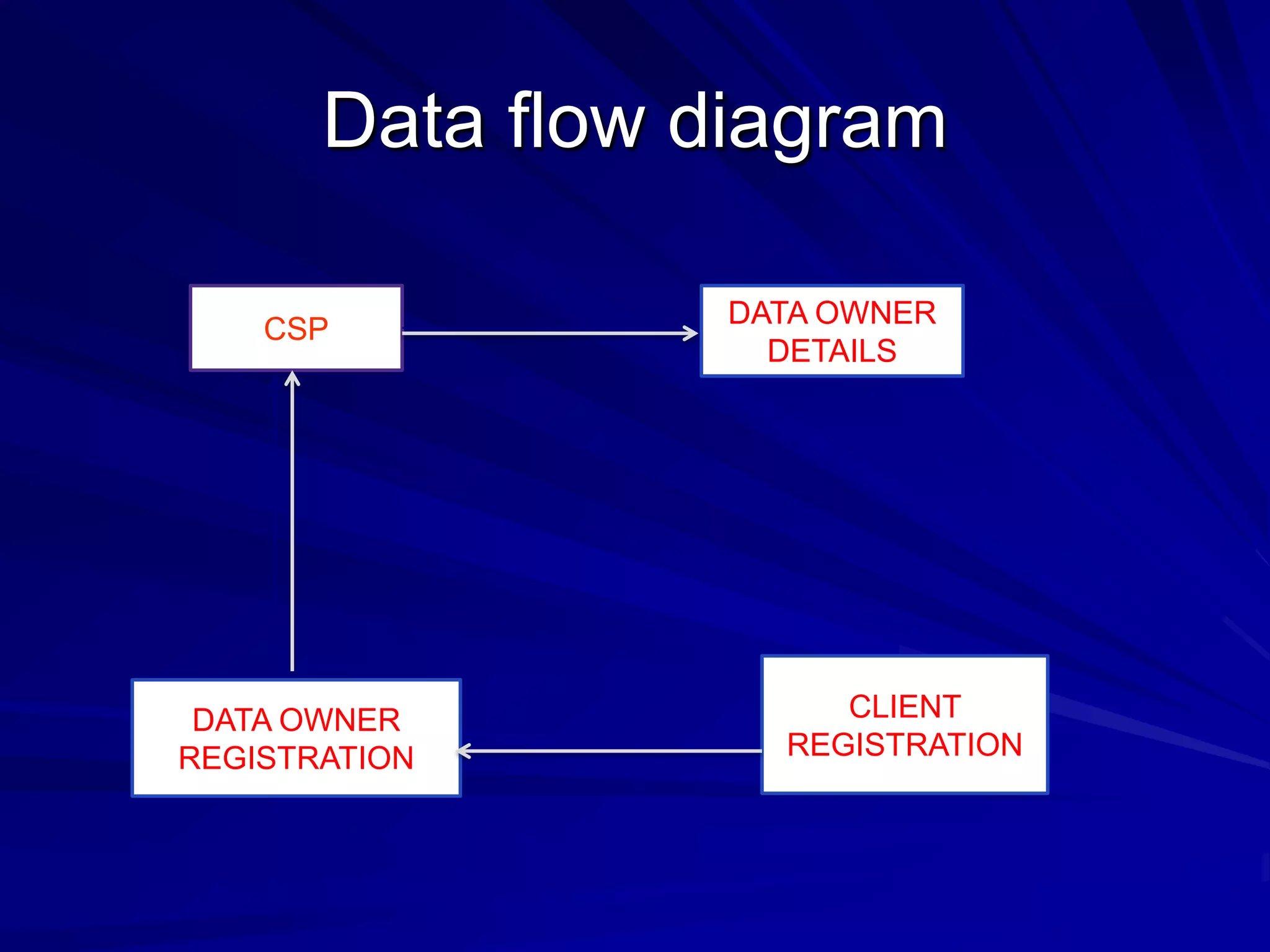
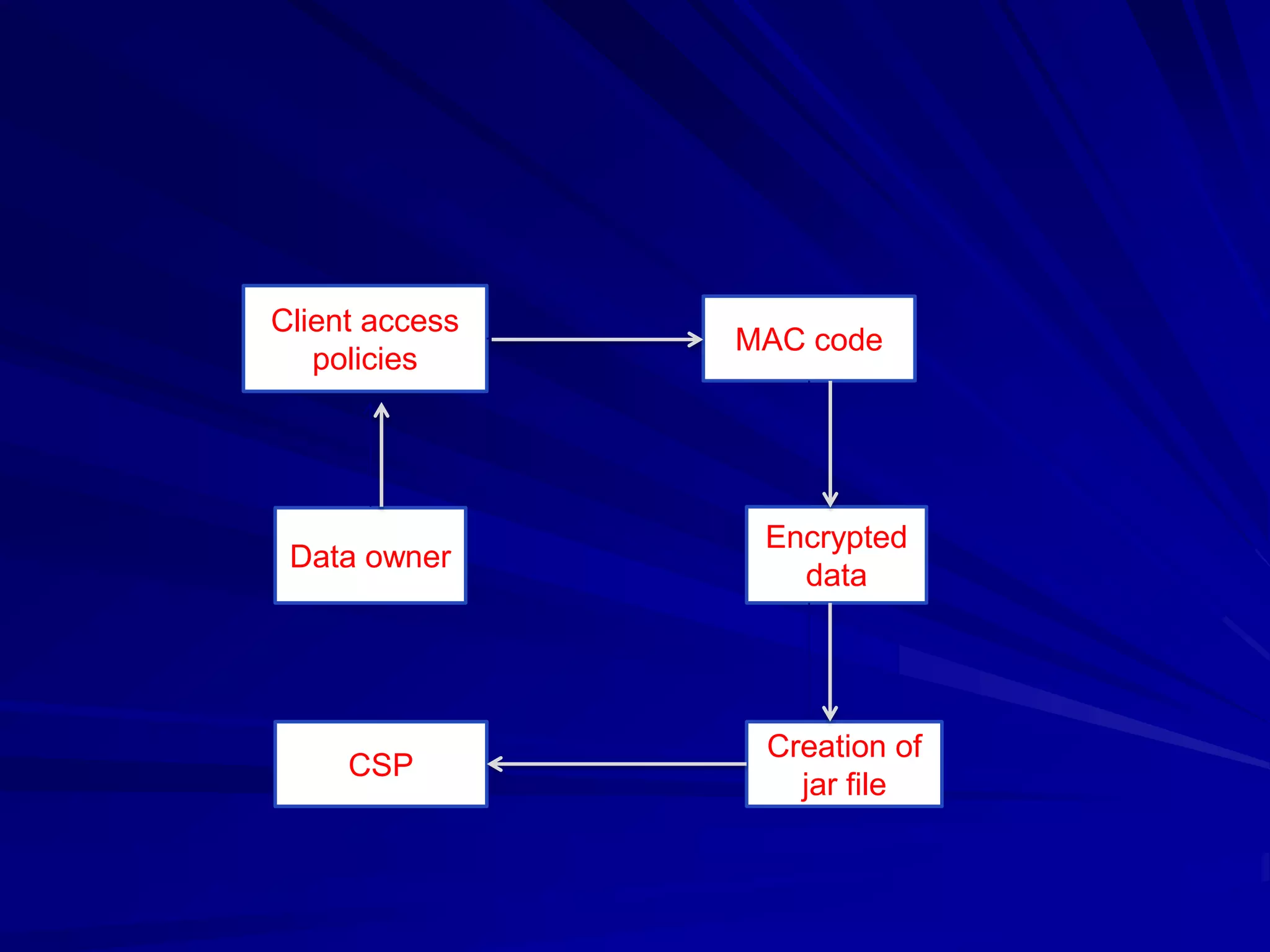
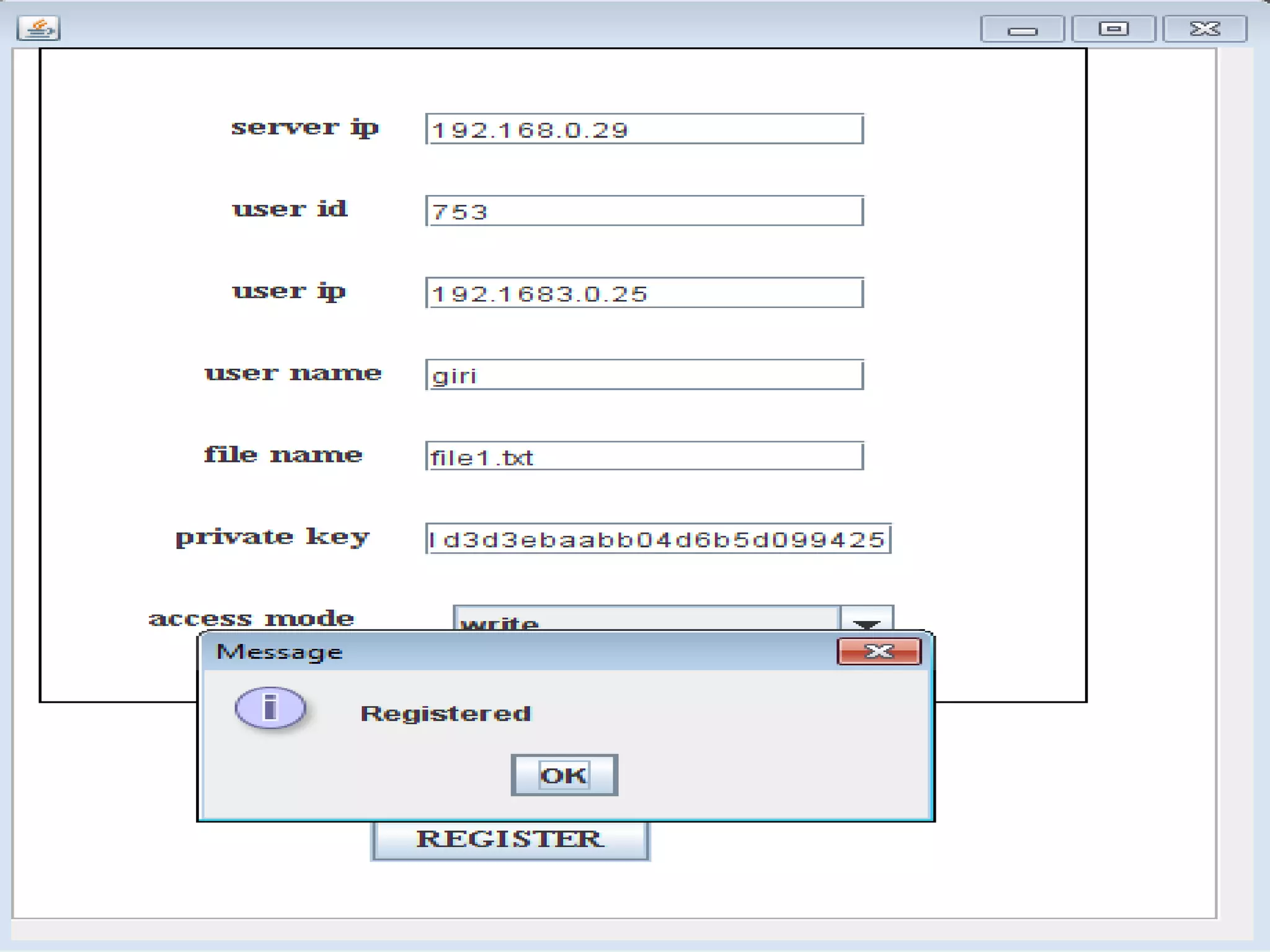
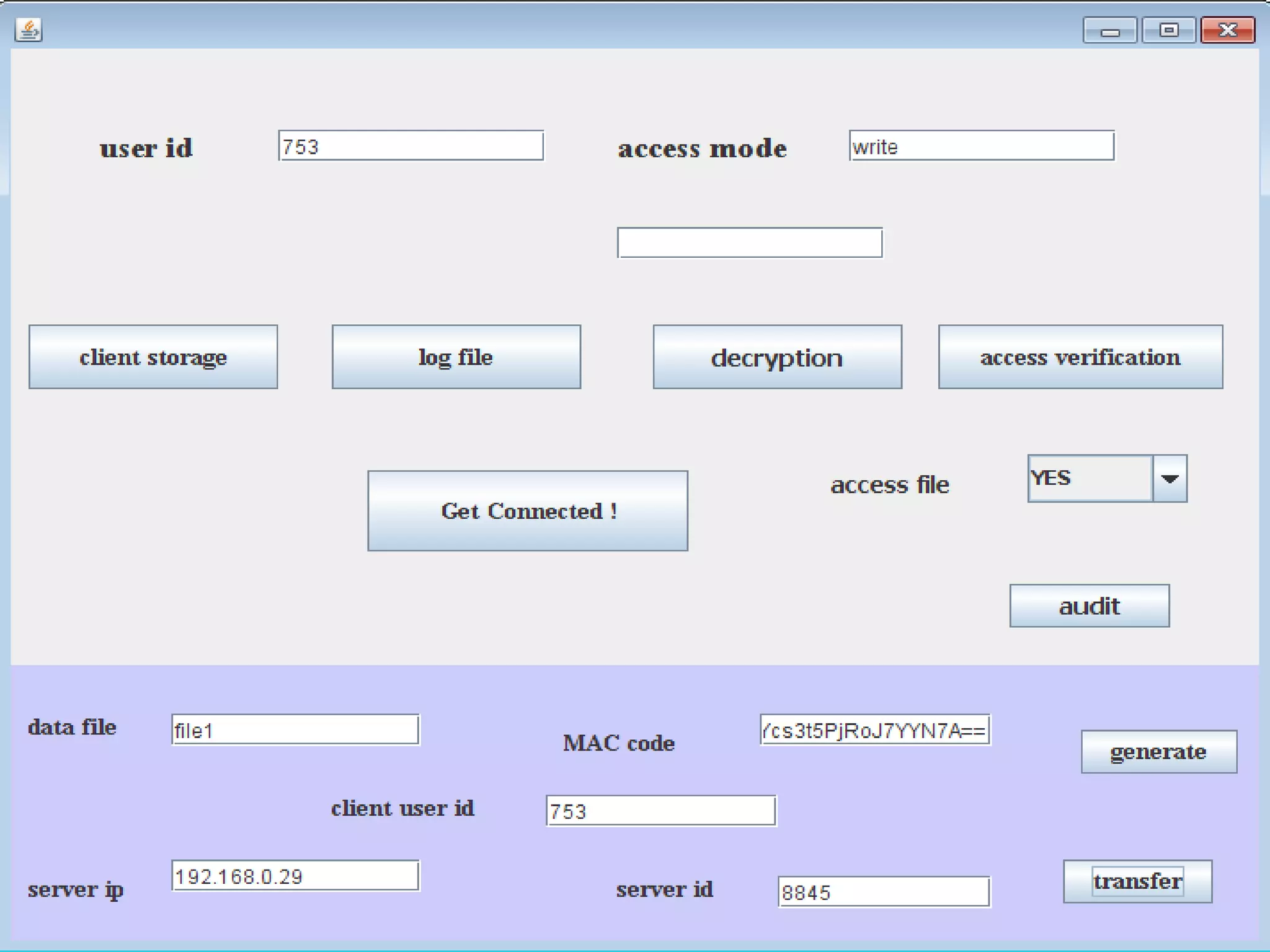
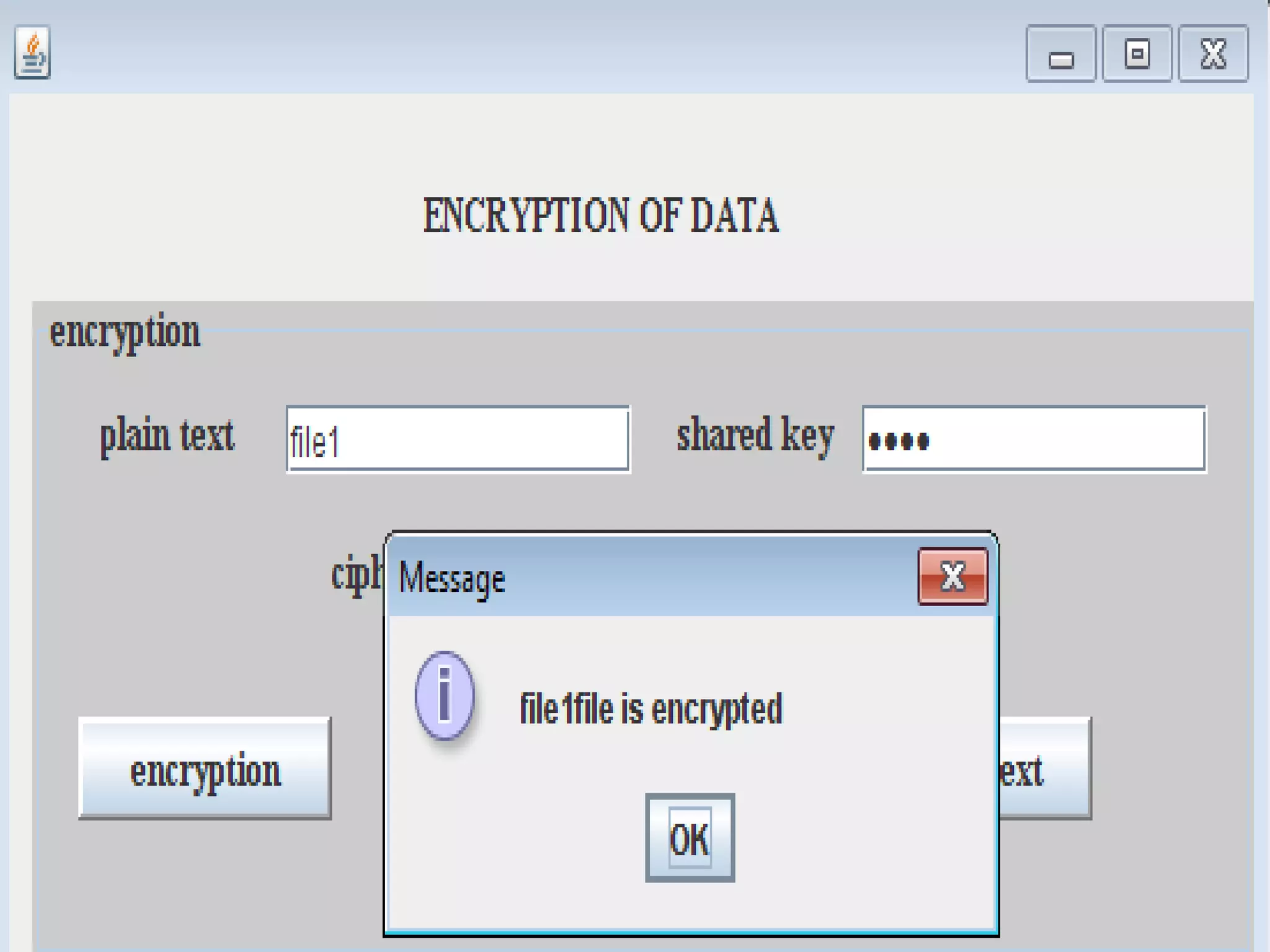
This document discusses providing accountability and access control for data shared in the cloud. It proposes a system where data owners can store encrypted data on a cloud service provider (CSP) along with access privileges for authorized clients. Clients must get permission from the data owner to retrieve encrypted data files from the CSP. The CSP generates log files of client access that are sent to the data owner for auditing purposes. The system uses algorithms like MD5, PBE and RSA for encryption, access control and integrity verification to securely share data while maintaining the data owner's control.