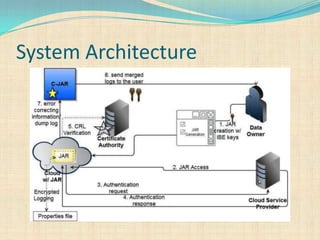
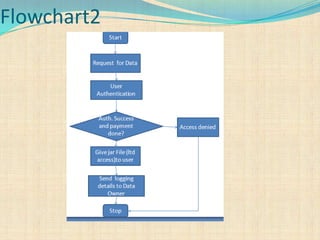
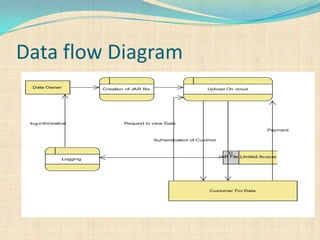
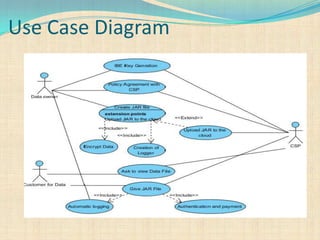
The document proposes a decentralized technique called the CAI framework to automatically log any access to data stored in the cloud. This framework uses Java archive (JAR) files to log data access and provide an auditing mechanism. It includes algorithms for identity-based encryption and authentication as well as push and pull modes for generating log records. The system architecture involves multiple server systems running software like Tomcat and MySQL to provide the cloud logging functionality.



![Related Work
Information Accountability[1]
Accountability mechanisms and Privacy
Manager[2]
Logic for Auditing Accountability in
Decentralized Systems[3]
Accountable Grid Computing System[4]](https://image.slidesharecdn.com/ciaframeworkforcolud-131007073210-phpapp01/85/Ensuring-Distributed-Accountability-for-Data-Sharing-in-the-Cloud-4-320.jpg)
![Cont.
Security Applications in JAVA using Self-
Depending Objects[SDO][5]
Proof-Carrying authentication (PCA)[6]
Identity-Based Encryption[7]
Current access control mechanism[8]](https://image.slidesharecdn.com/ciaframeworkforcolud-131007073210-phpapp01/85/Ensuring-Distributed-Accountability-for-Data-Sharing-in-the-Cloud-5-320.jpg)







![References
[1] “Information Accountability,” Comm.ACM, vol. 51, no.
6, pp. 82-87, 2008.
[2] “Accountability as a Way Forward for Privacy Protection in
the Cloud,” Proc. First Int’l Conf. Cloud Computing,09.
[3] Logic for Auditing Accountability in Decentralized
Systems,” Proc. IFIP TC1 WG1.7 Workshop Formal Aspects
in Security and Trust , pp. 187-201, 2005.
[4] The Design and Evaluation of Accountable Grid
Computing System,” Proc. 29thIEEE Int’l Conf. Distributed
Computing Systems (ICDCS ’09),pp. 145-154, 2009.](https://image.slidesharecdn.com/ciaframeworkforcolud-131007073210-phpapp01/85/Ensuring-Distributed-Accountability-for-Data-Sharing-in-the-Cloud-17-320.jpg)
![References
[5]“Using Self-Defending Objects to Develop Security
Aware Applications in Java,” Proc. 27th Australasian
Conf. Computer Science, vol. 26,pp. 341-349, 2004
[6] An Open Framework for Foundational Proof-
Carrying Code,” Proc. ACM SIGPLAN Int’l Workshop
Types in Languages Design and Implementation, pp.
67-78,2007.
[7]“Towards Accountable Management of Identity and
Privacy: Sticky Policies and Enforceable Tracing
Services,” Proc. Int’l Workshop Database and Expert
Systems Applications (DEXA), pp. 377-382, 2003.](https://image.slidesharecdn.com/ciaframeworkforcolud-131007073210-phpapp01/85/Ensuring-Distributed-Accountability-for-Data-Sharing-in-the-Cloud-18-320.jpg)
![References
[8]“Usage Control Enforcement: Present and Future,”
IEEE Security & Privacy, vol. 6, no. 4, pp. 44-
53, July/Aug. 2008.](https://image.slidesharecdn.com/ciaframeworkforcolud-131007073210-phpapp01/85/Ensuring-Distributed-Accountability-for-Data-Sharing-in-the-Cloud-19-320.jpg)