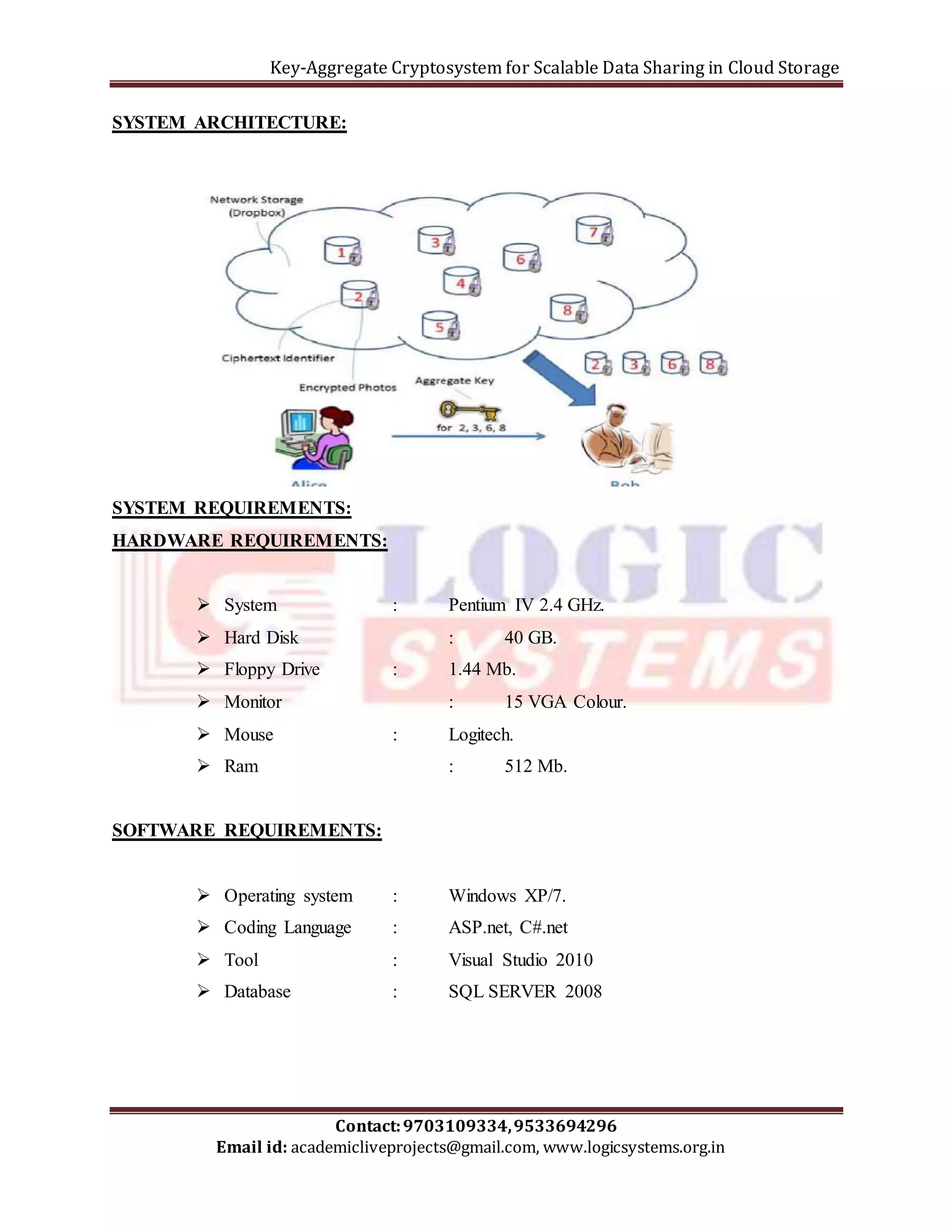
The document presents a key-aggregate cryptosystem designed for scalable data sharing in cloud storage, enabling efficient and secure delegation of decryption rights through compact, constant-size aggregate keys. It addresses the limitations of existing systems, such as increased costs and complexity with more decryption keys, by introducing a novel public-key encryption scheme that aggregates multiple keys into a single key without size increase. The paper includes formal security analysis and outlines additional applications, such as patient-controlled encryption in flexible hierarchies.