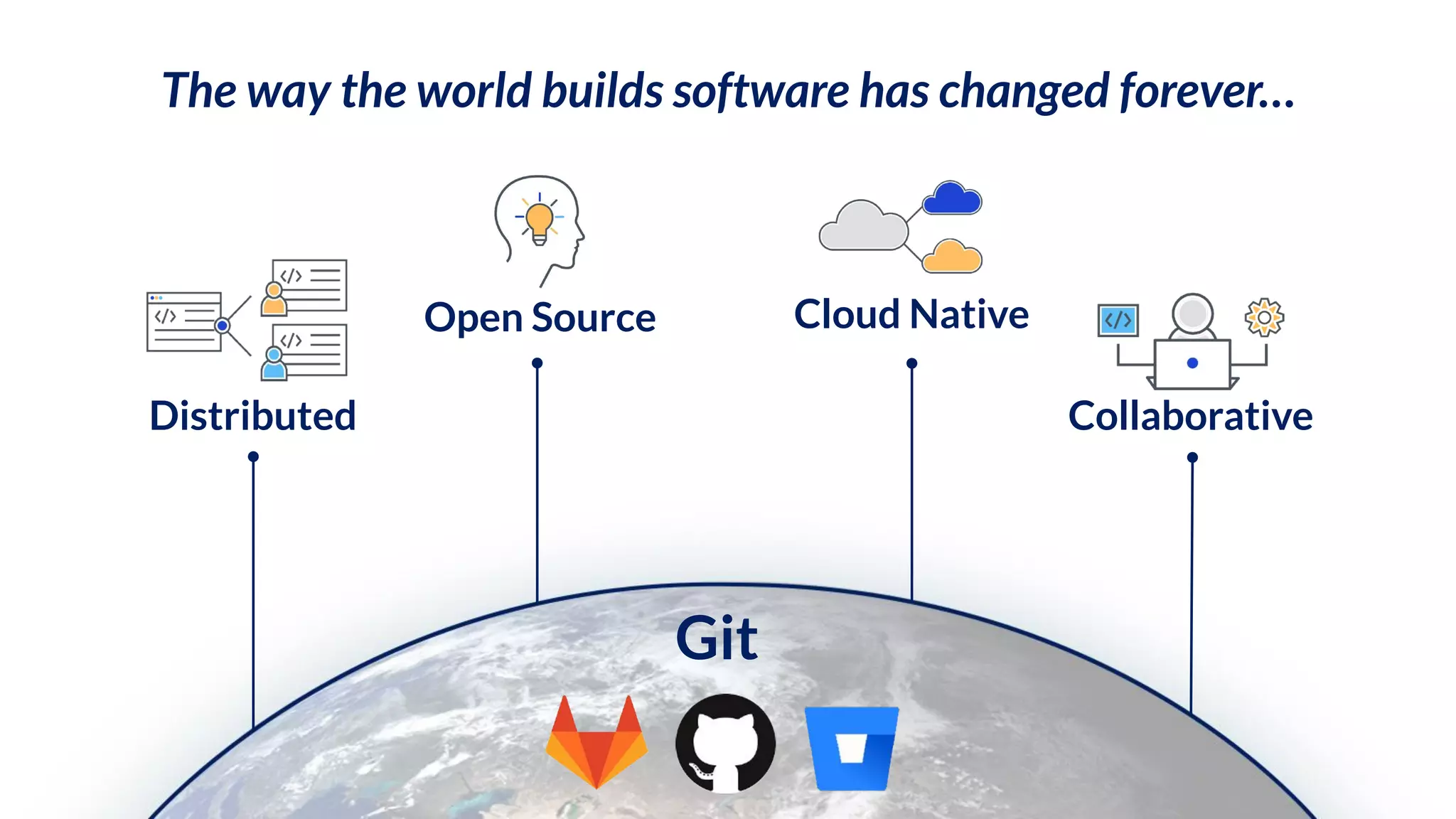
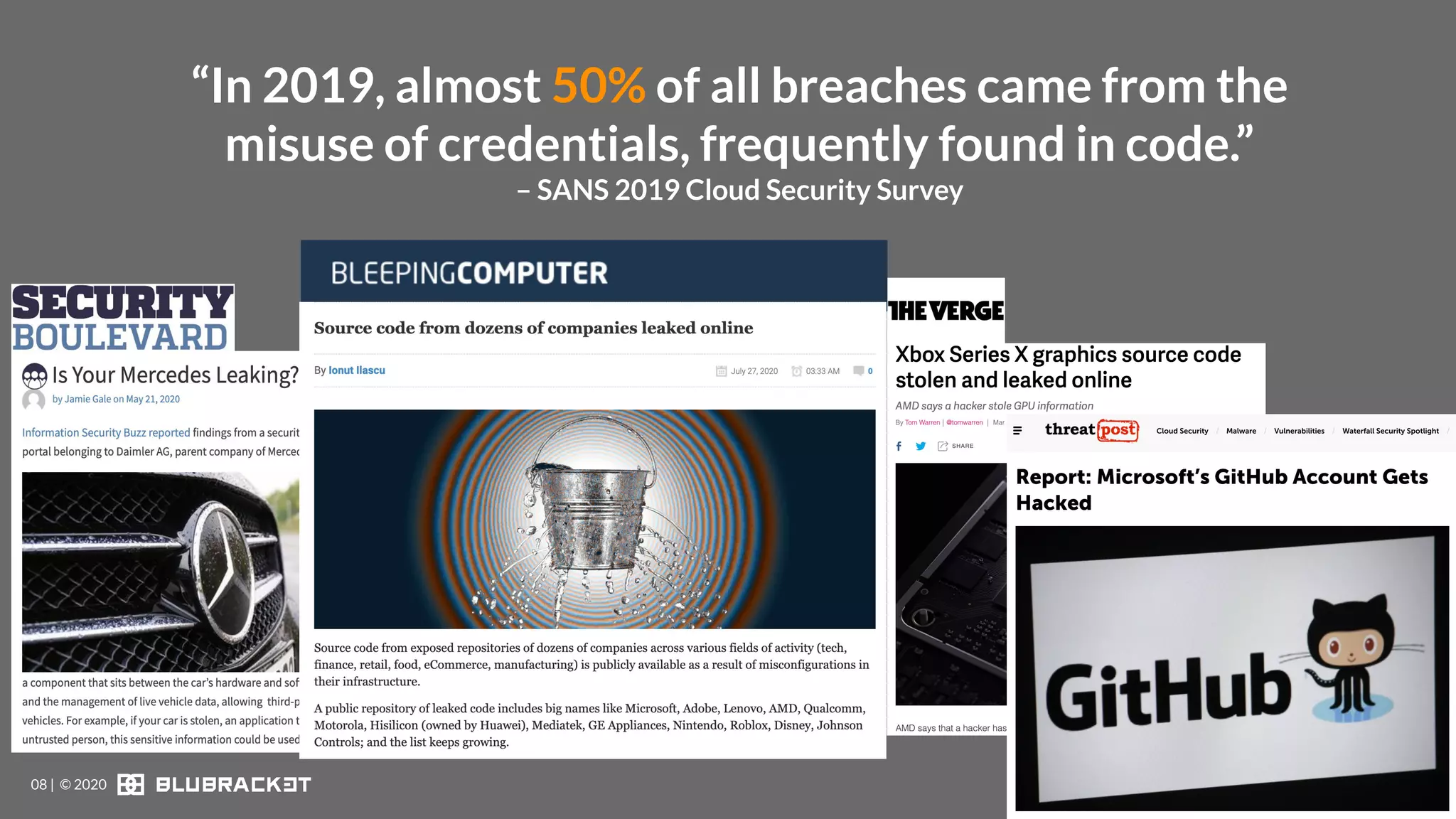
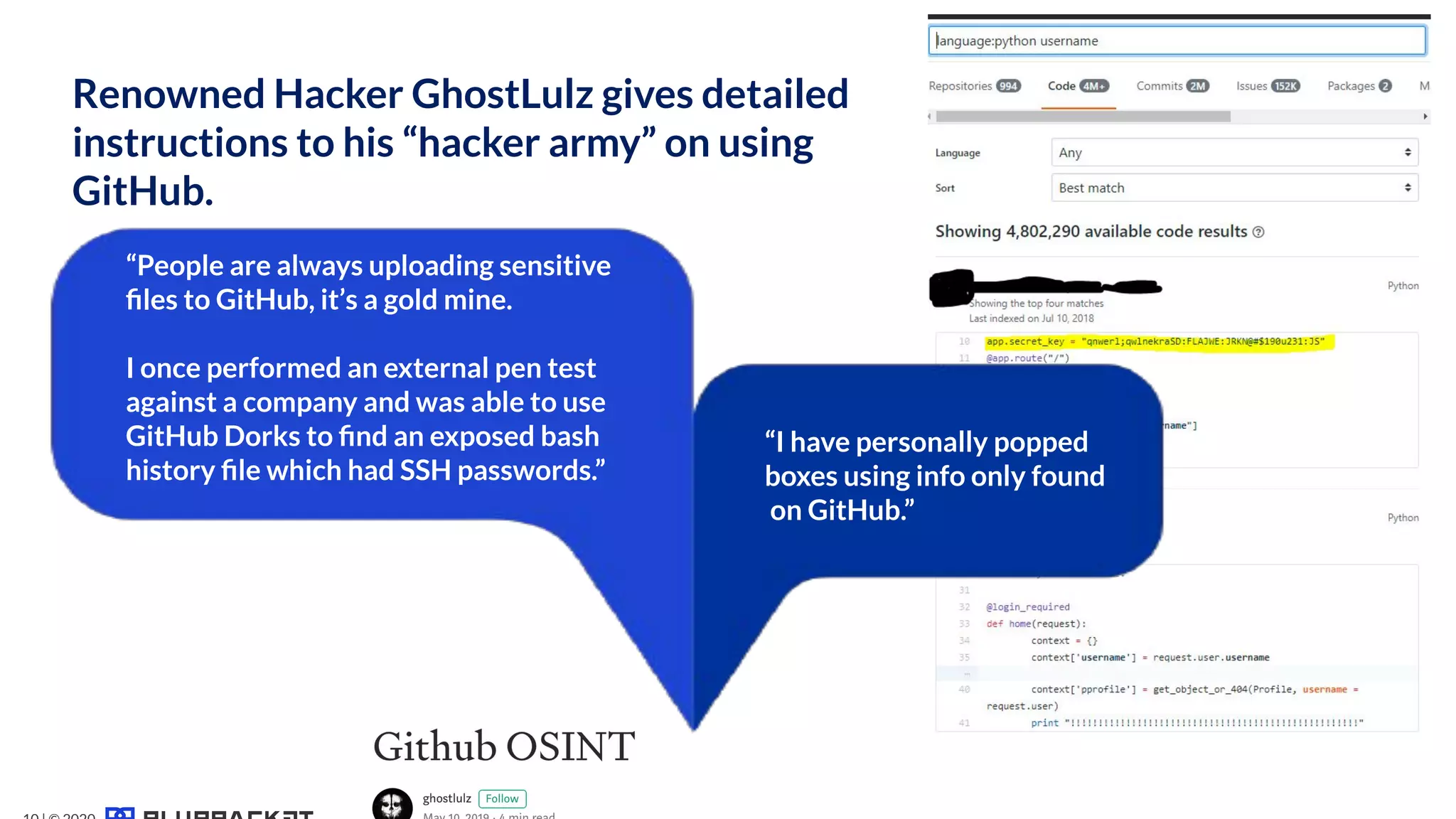
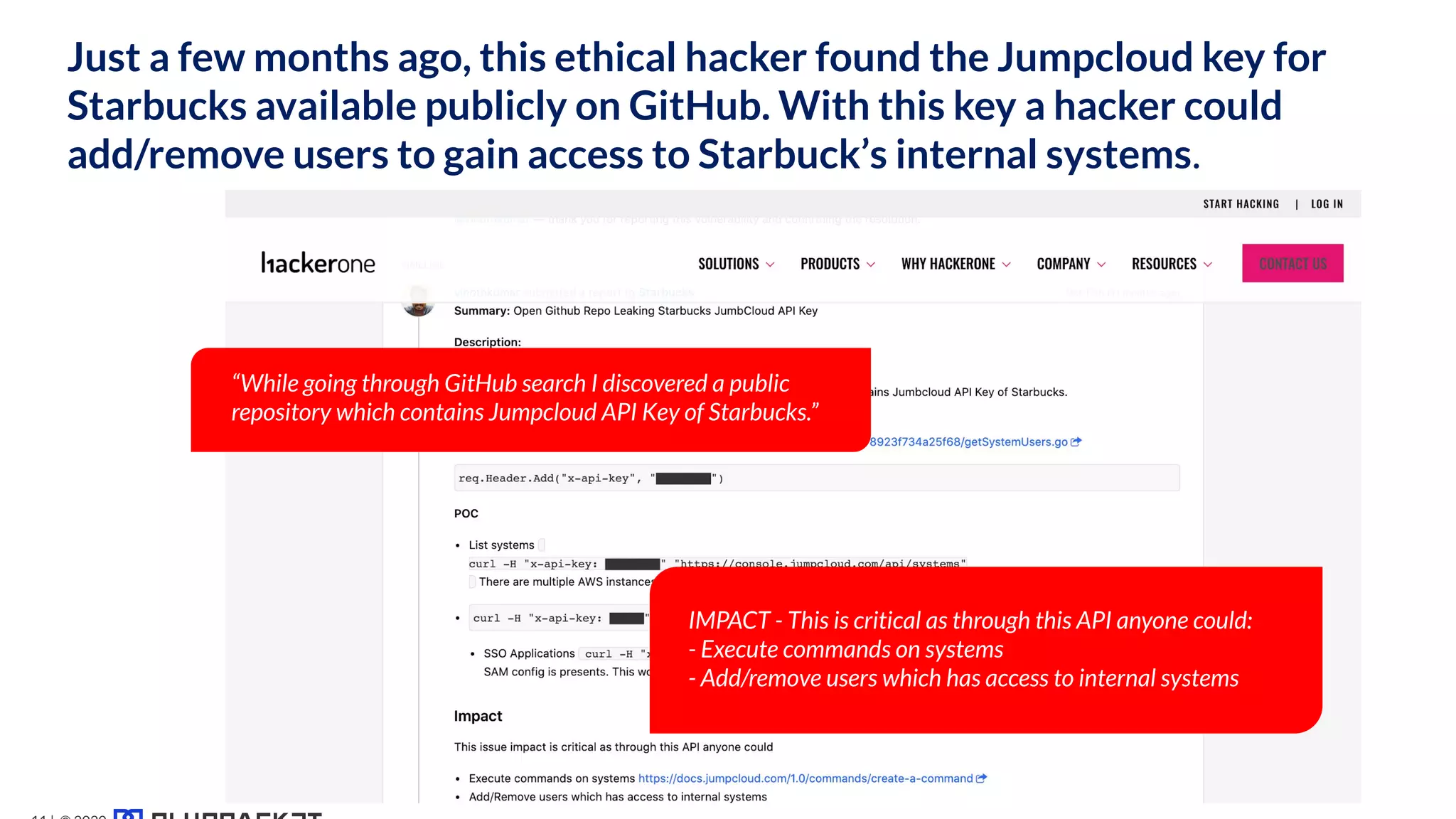
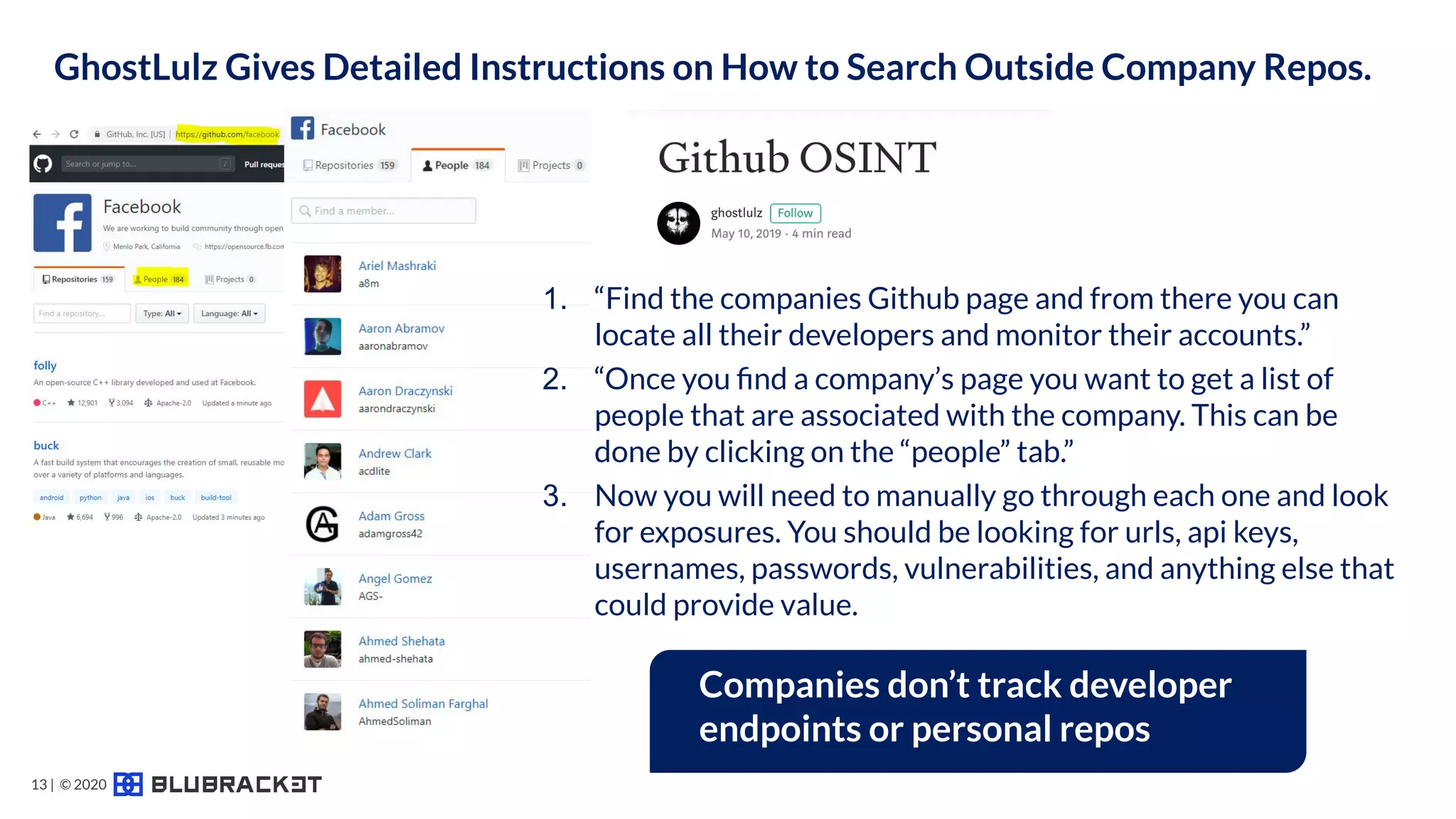
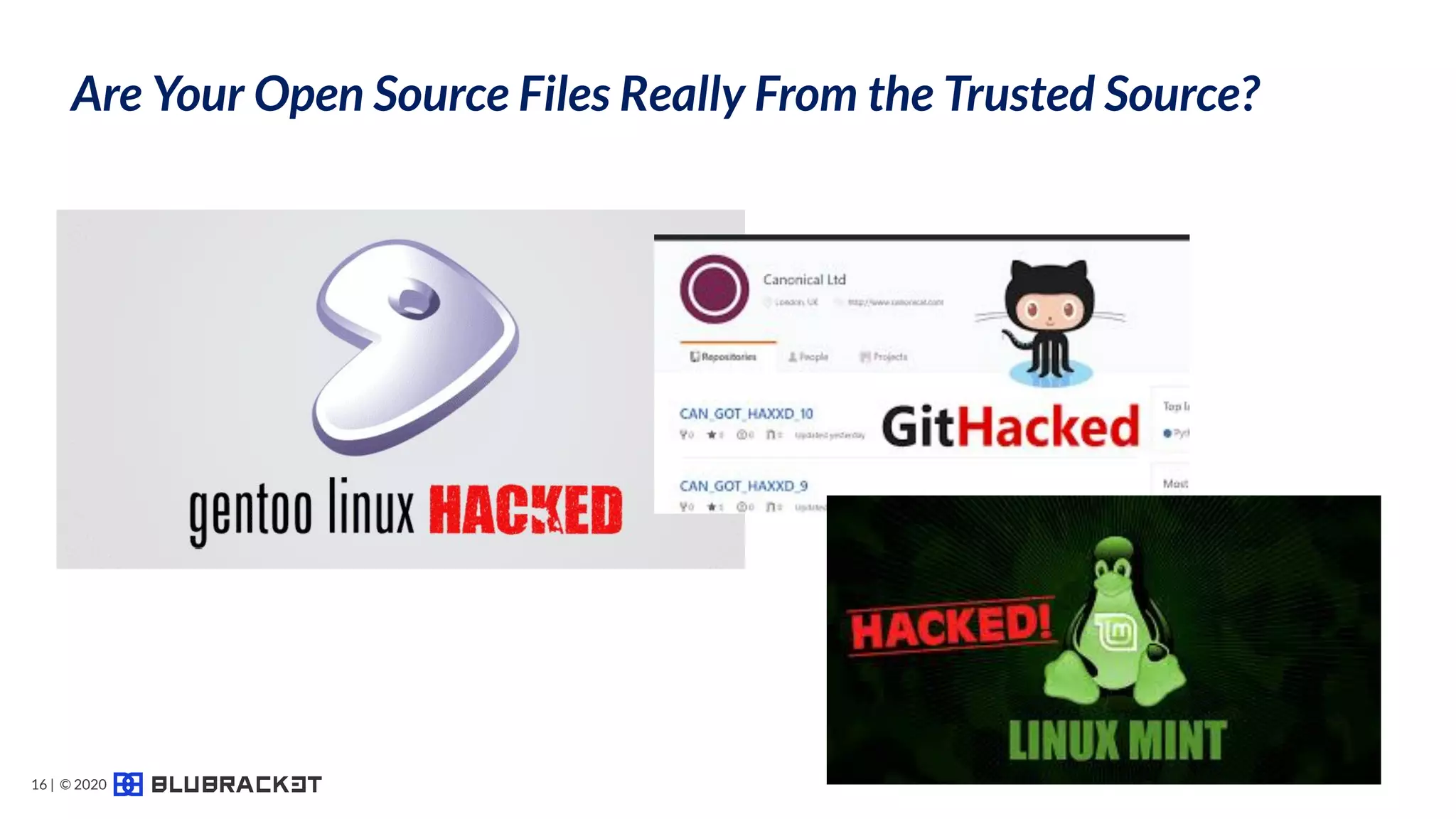
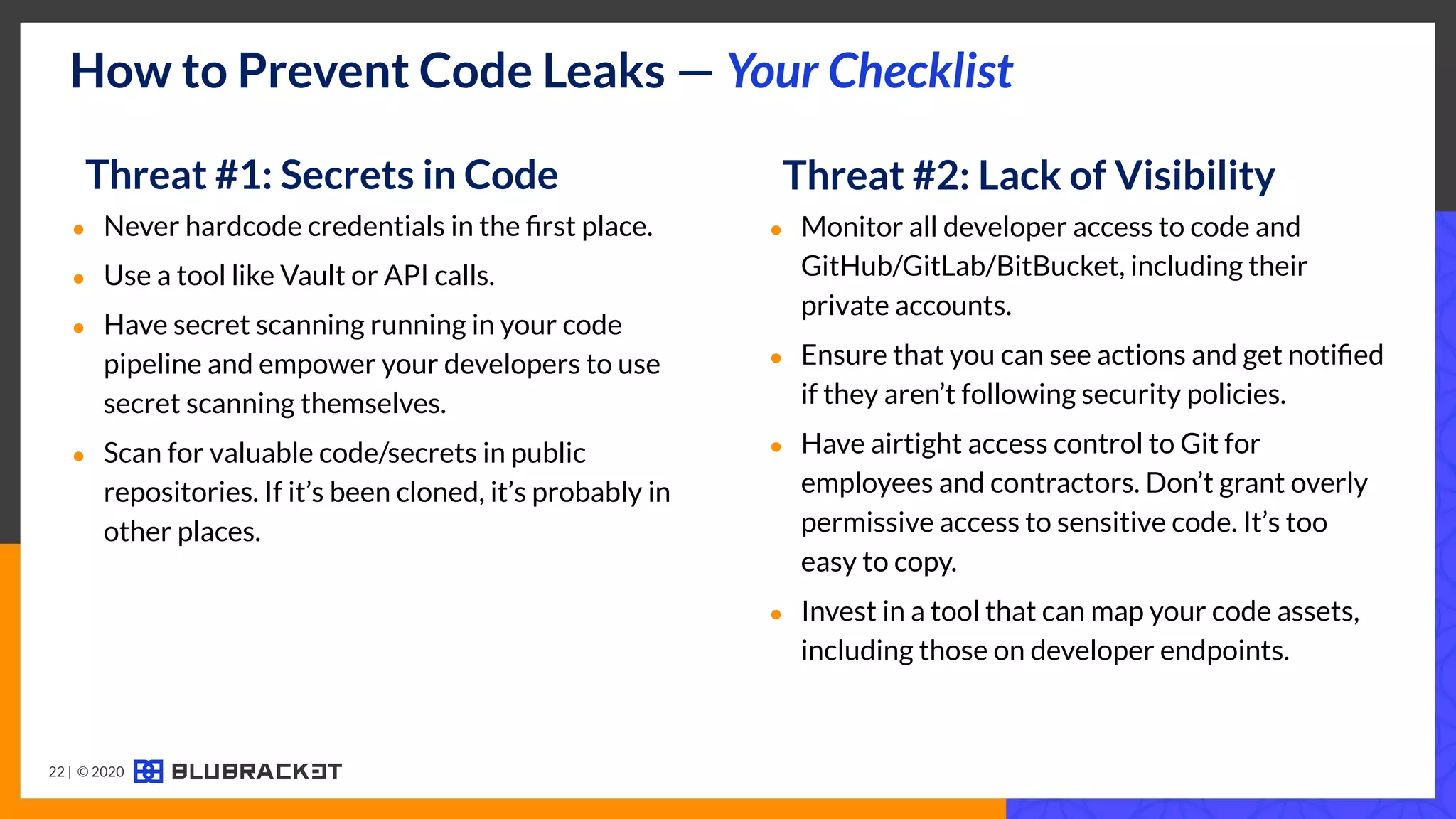
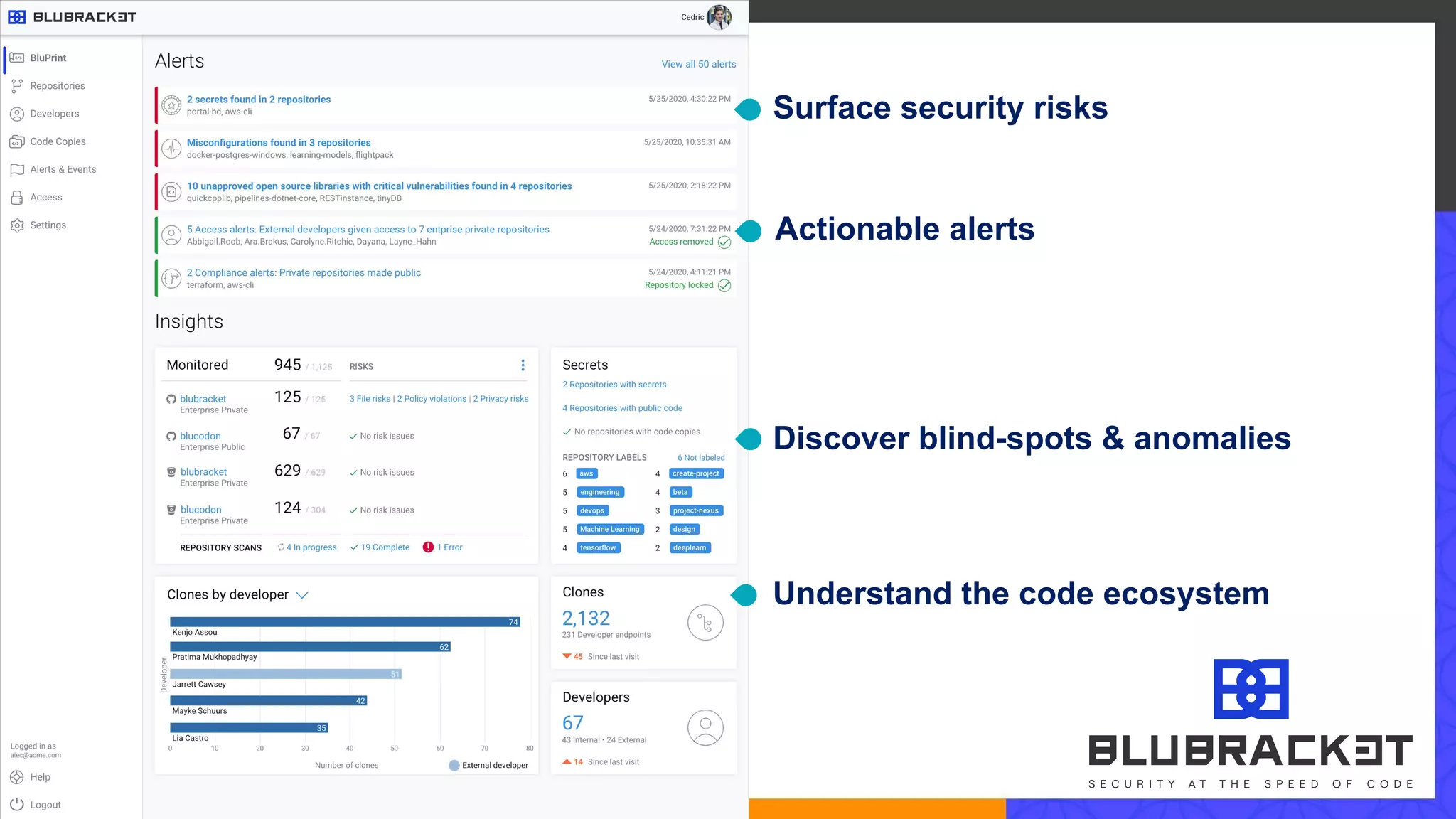
The document addresses critical code security risks, highlighting the prevalence of sensitive data in code and vulnerabilities stemming from open source software. It outlines five key threats, including secrets in code, lack of visibility, malicious code from unauthorized sources, exposure of business infrastructure, and leakage of personal identifiable information (PII). The document concludes with a checklist for preventing code leaks and improving security measures related to code management practices.