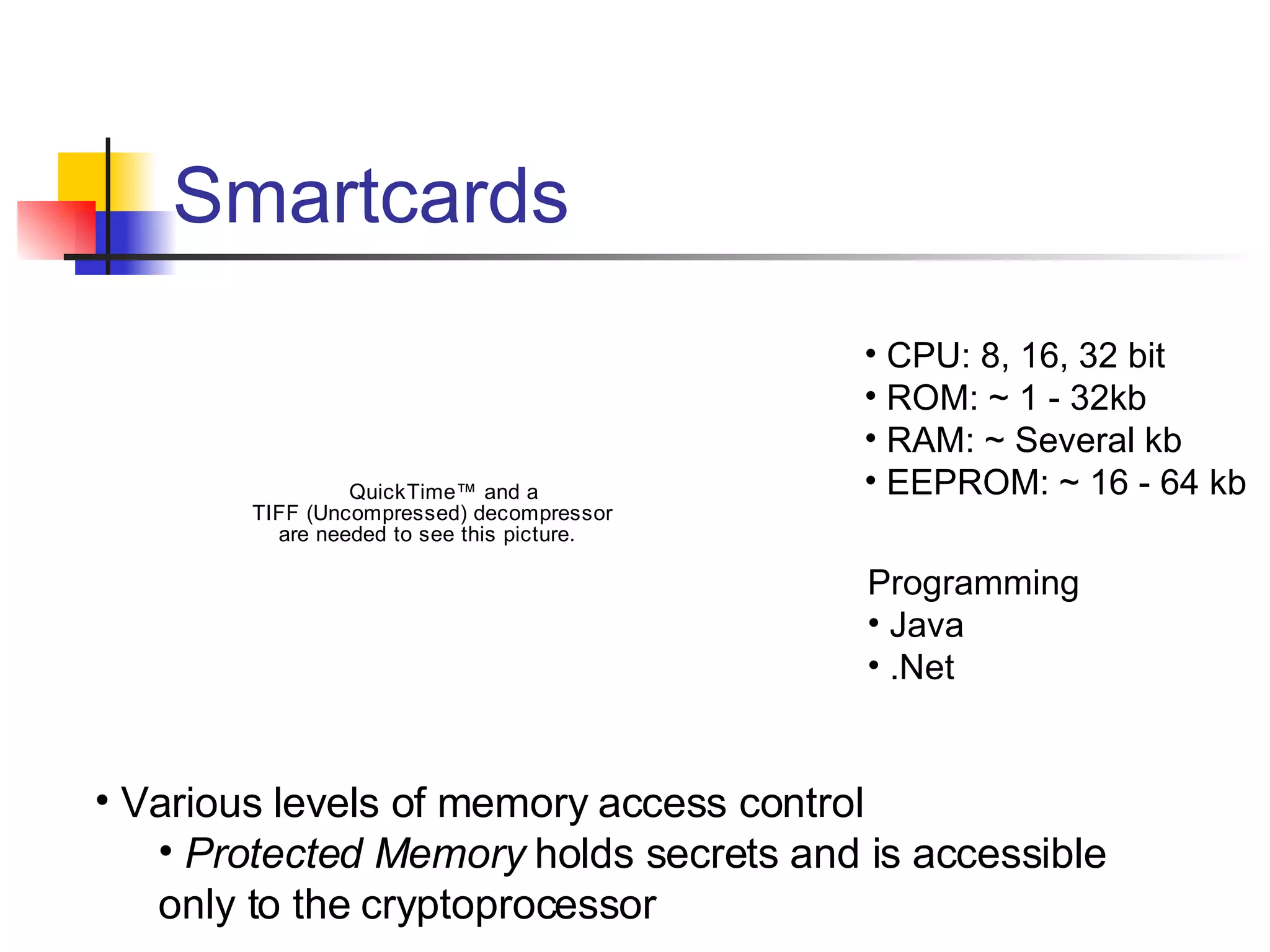
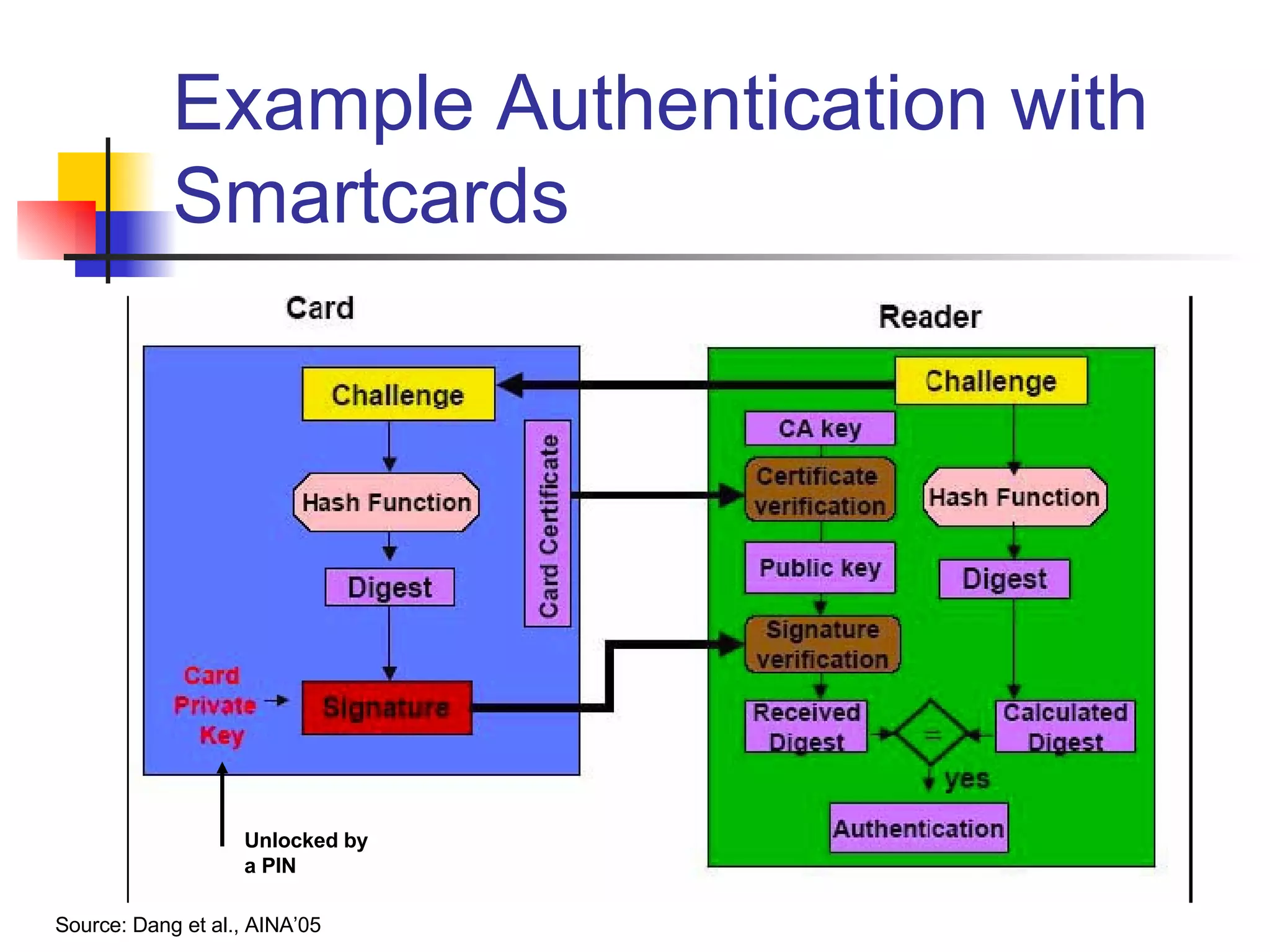
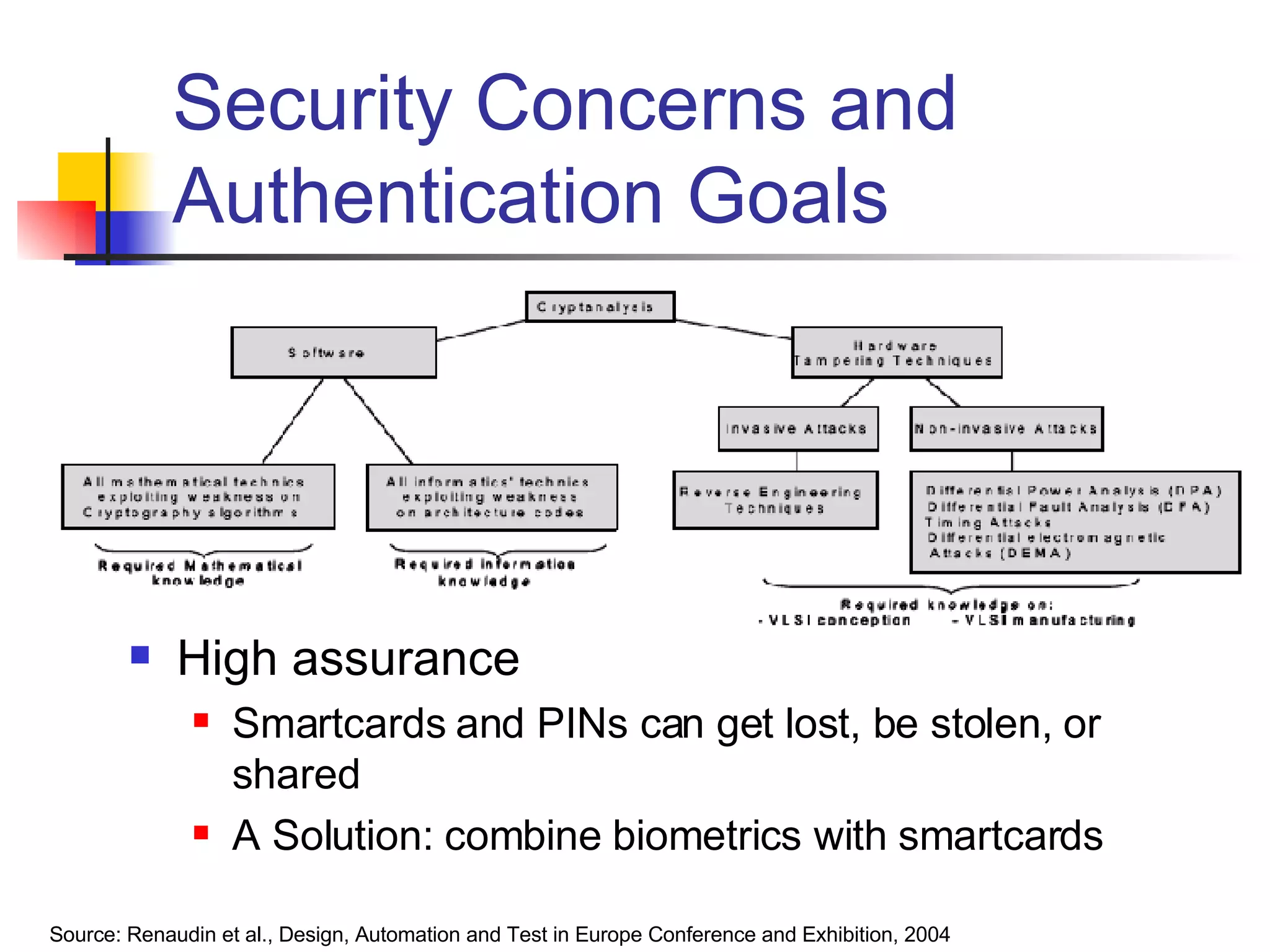
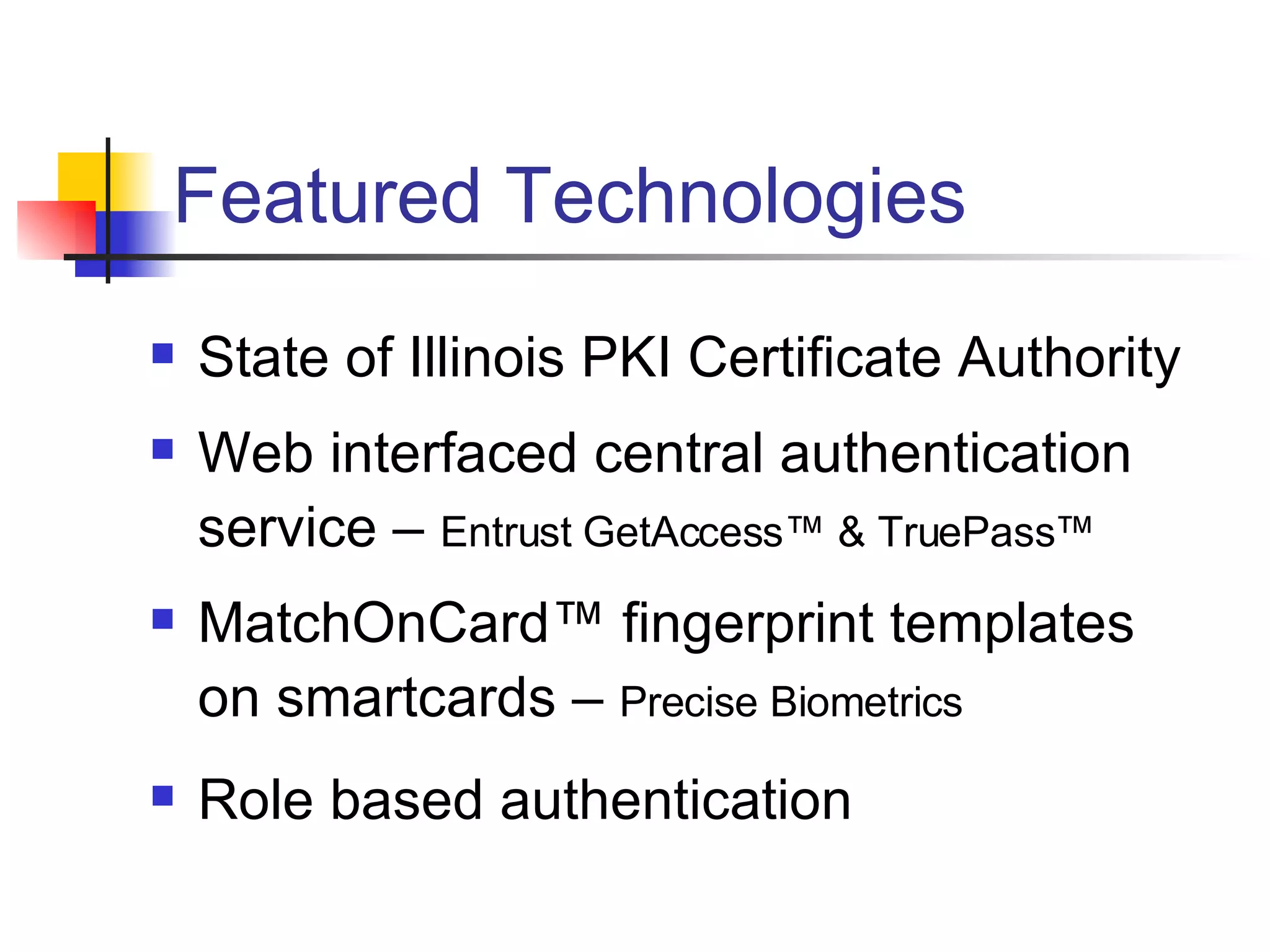
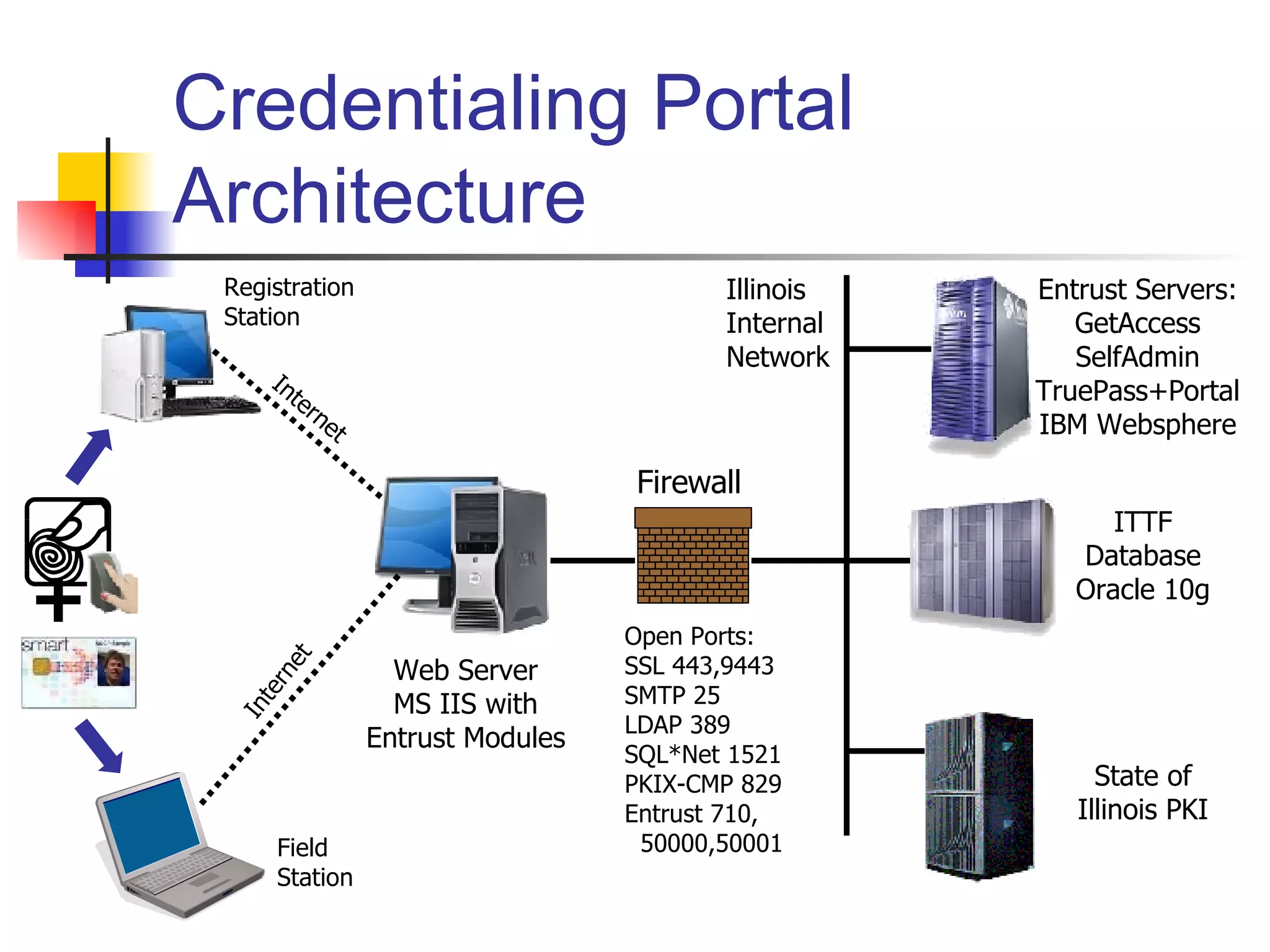
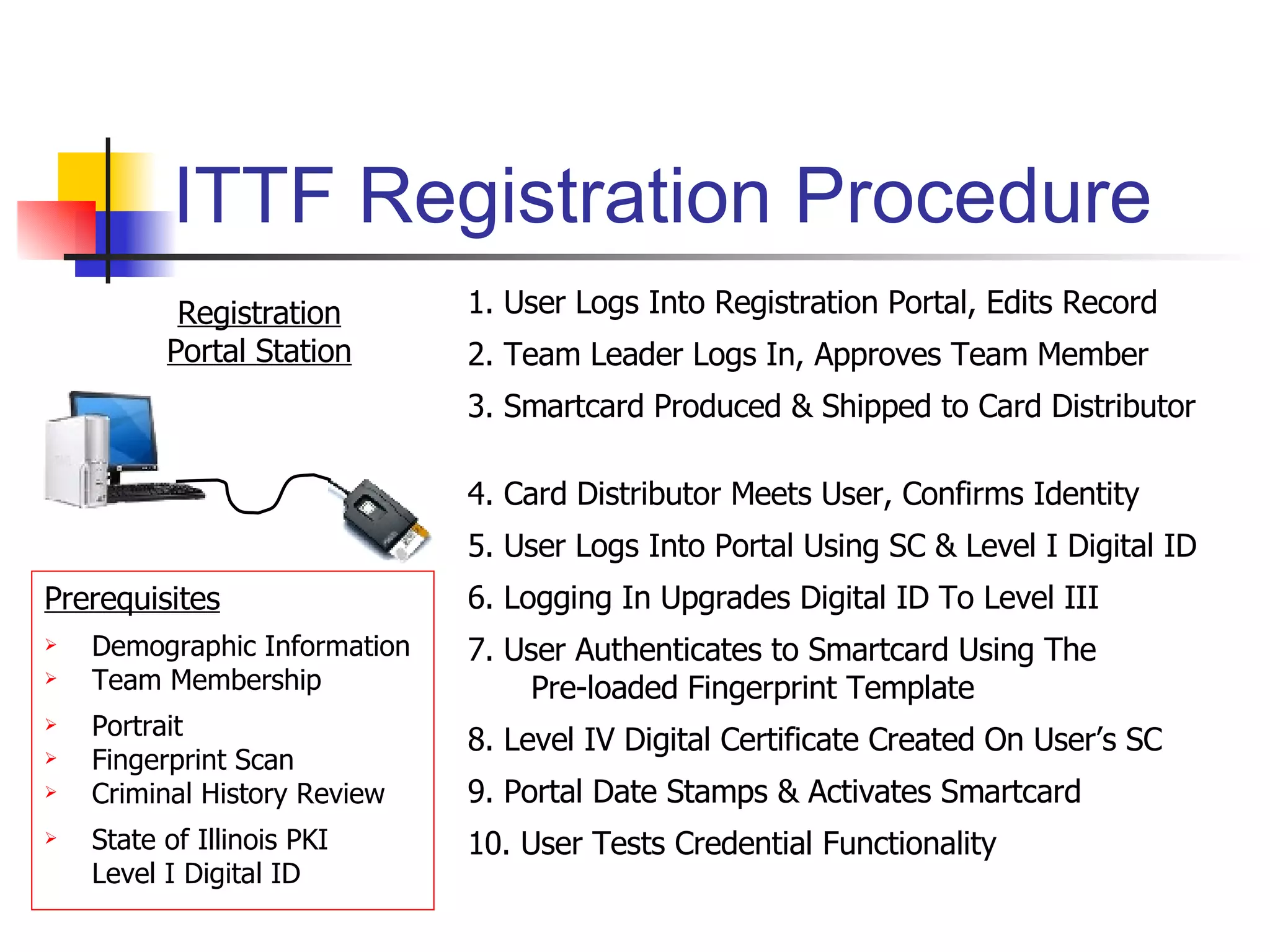
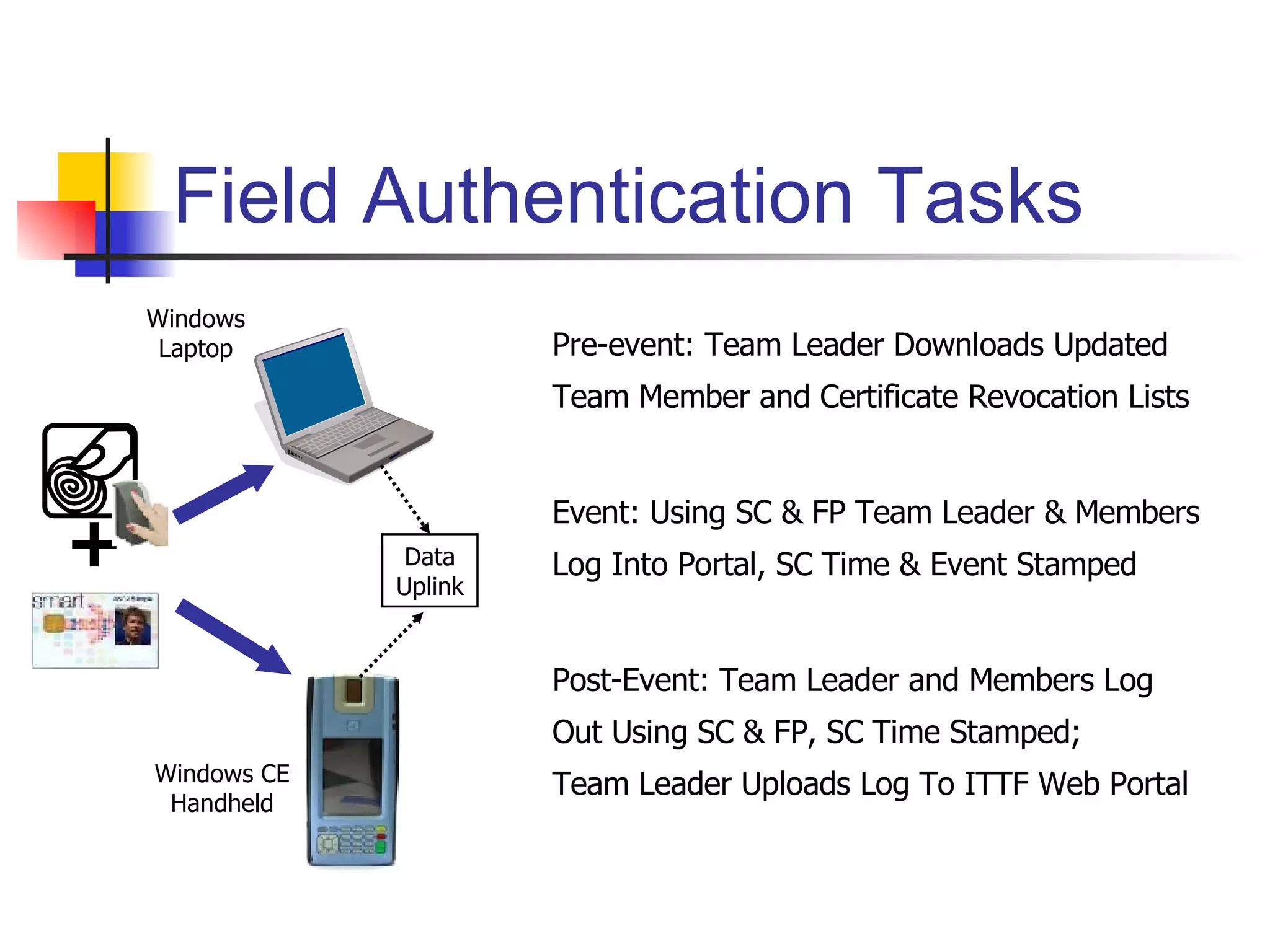
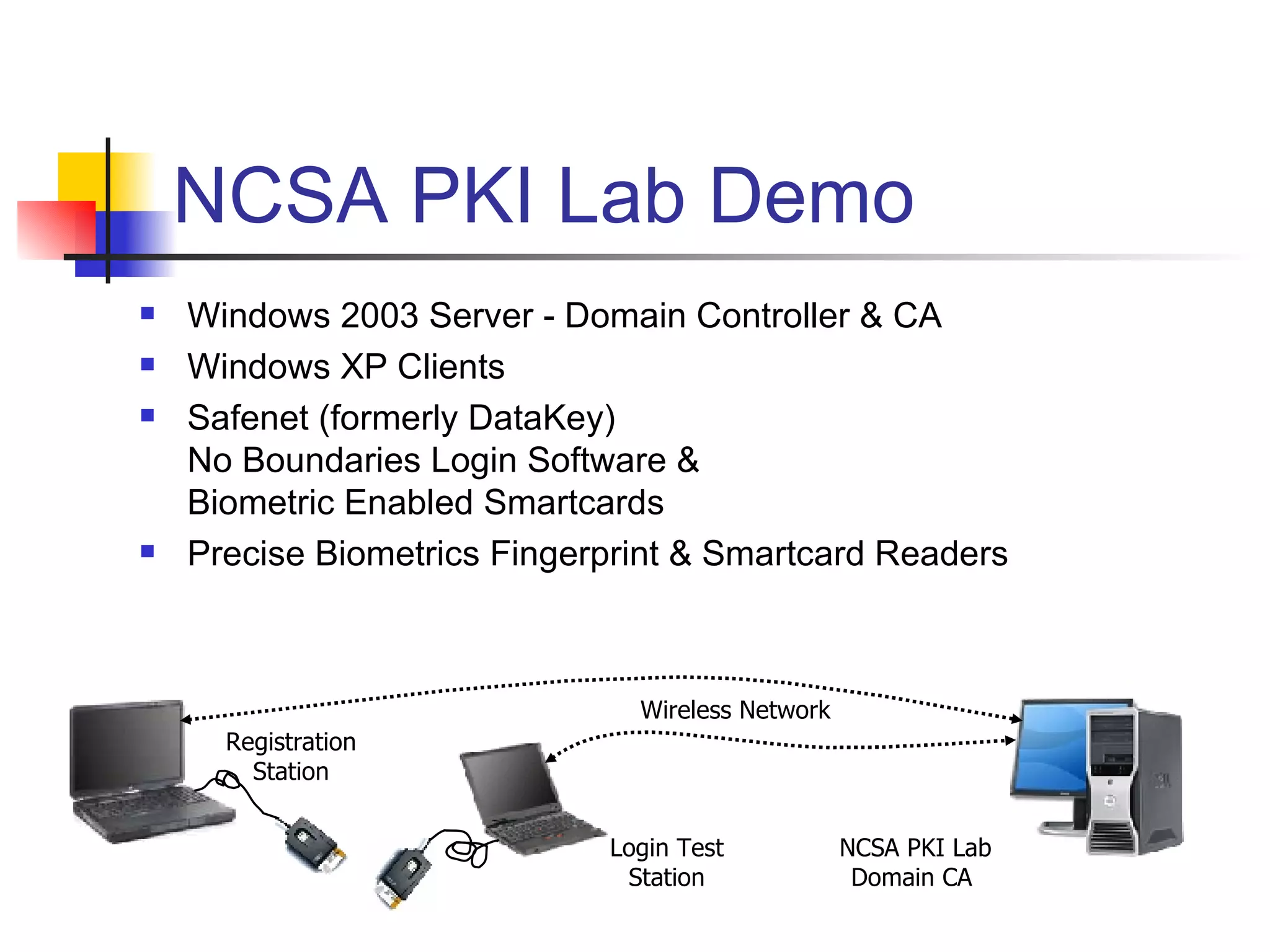
The document discusses using smartcards and biometrics like fingerprints for multi-factor authentication. It outlines the goals of authentication including verifying identity, preventing secrets from leaking, and providing scalability. Passwords are noted as insufficient for these goals. The solution presented is using smartcards to store credentials alongside biometrics like fingerprints for two-factor authentication. An example project that implemented this was a credentialing system for first responders in Illinois.





![Public-Key Infrastructure (PKI) Public Key Cryptography Sign with private key, verify signature with public key Encrypt with public key, decrypt with private key Key Distribution Who does a public key belong to? Certification Authority (CA) verifies user’s identity and signs certificate Certificate is a document that binds the user’s identity to a public key Authentication Signature [ h ( random, … ) ] Subject: CA signs Issuer: CA Subject: Jim Issuer: CA Source: Jim Basney’s MyProxy presentation](https://image.slidesharecdn.com/ynamono-hs-lecture697/75/Ynamono-Hs-Lecture-6-2048.jpg)




![Authentication with Smartcards and Fingerprints Any Questions?? http://www.ncassr.org/ http://www.ncsa.uiuc.edu/Projects/cybertechnologies.html#security http://pkilab.ncsa.uiuc.edu Himanshu Khurana [email_address] Joe Muggli [email_address]](https://image.slidesharecdn.com/ynamono-hs-lecture697/75/Ynamono-Hs-Lecture-24-2048.jpg)