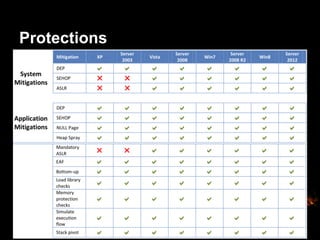
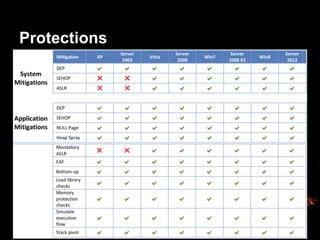
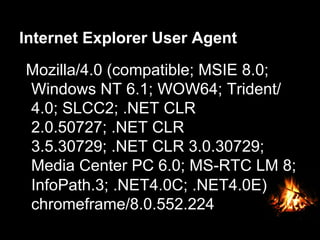
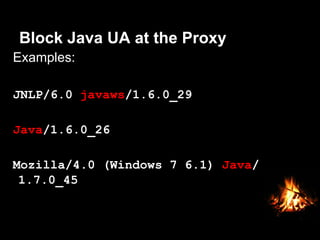
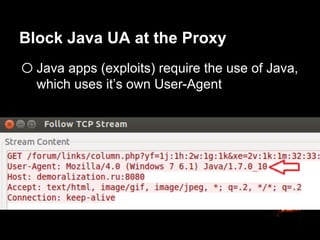
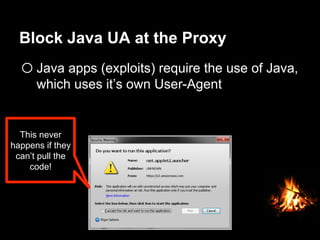
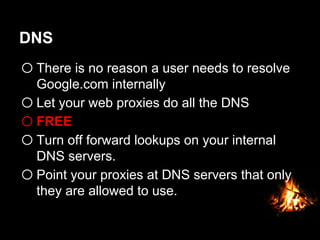
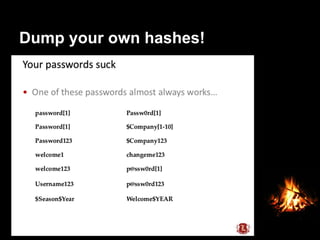
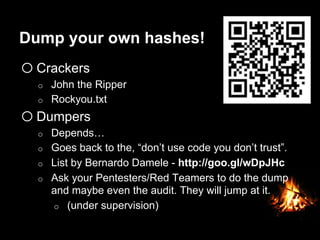
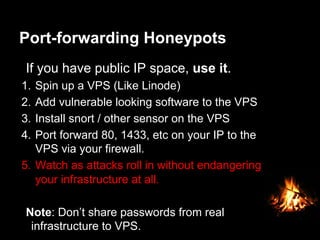
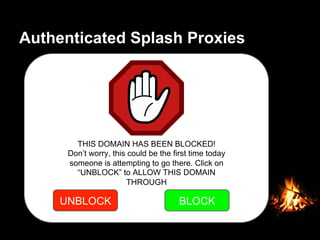
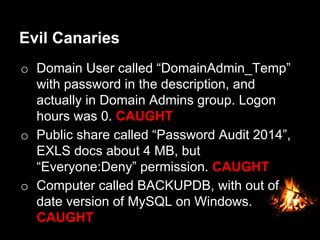
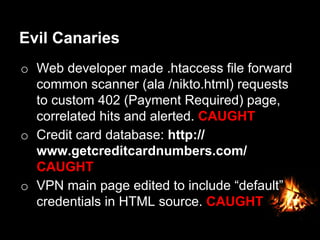
This document provides suggestions for free or low-cost defenses that can frustrate attackers, including enabling EMET, blocking Java user agents at the proxy, port forwarding honeypots, authenticated splash proxies, and deploying "evil canaries" to detect intruders on the network. It emphasizes logging, vulnerability scanning, and getting penetration testers and the help desk involved in security efforts. The document aims to demonstrate mostly free techniques that can significantly improve the security of an organization.