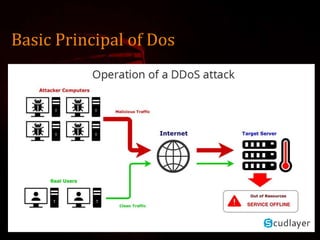
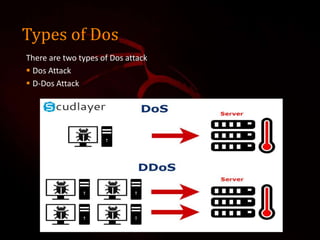
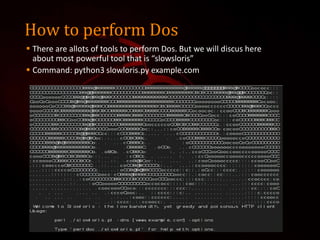
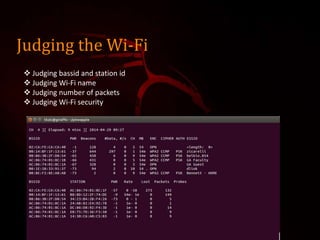
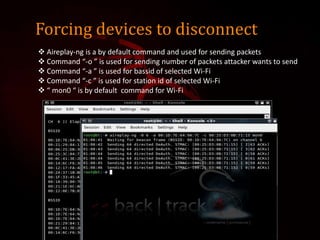
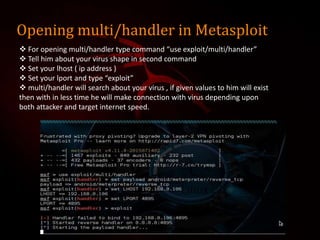
This document outlines a presentation on Kali Linux and its uses for penetration testing. It introduces the group members and discusses types of software. It defines Linux and Kali Linux, highlighting Kali Linux's advantages and tools for penetration testing. It describes how to install Kali Linux and demonstrates attacks that can be performed using its tools, including denial of service attacks, aircrack-ng for cracking wireless networks, and using FatRat and Metasploit to create and deploy viruses for system hacking.