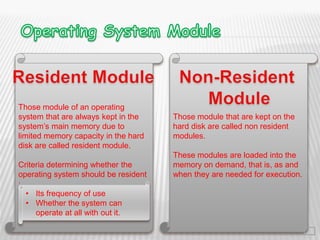
The document discusses operating system concepts including time sharing systems, file management, file access methods, OS structure, kernels, and monolithic vs microkernels. It provides details on:
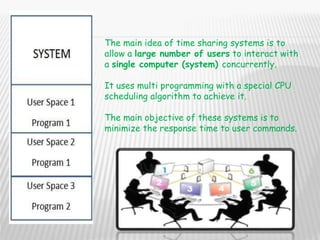
1) The main idea of time sharing systems is to allow multiple users to interact with a single computer concurrently using multi-programming and CPU scheduling.
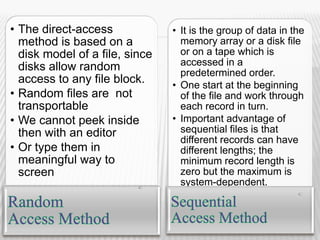
2) File management involves activities like structuring, accessing, naming, sharing and protecting files through operations like create, delete, open, close, read, write, seek, rename and copy.
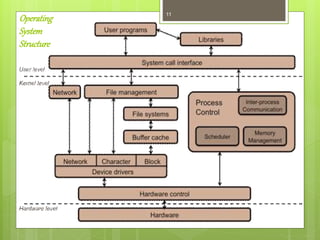
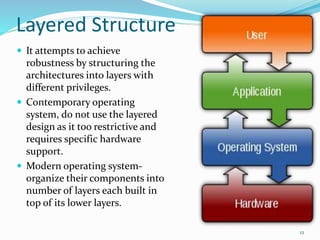
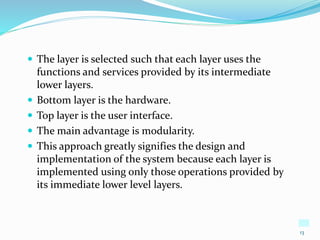
3) OS structure can use a layered approach with different privilege levels or organize components into layers with each layer building on lower layers.