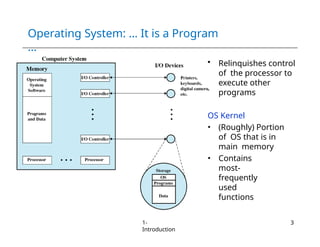
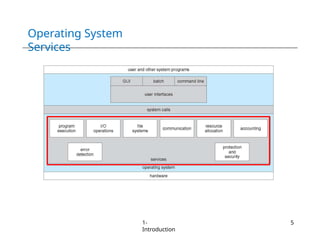
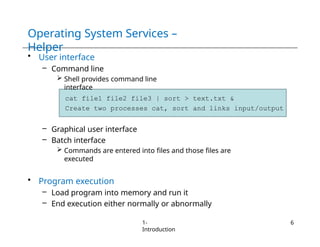
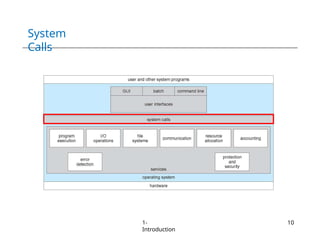
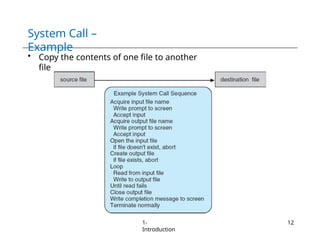
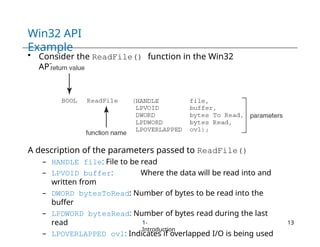
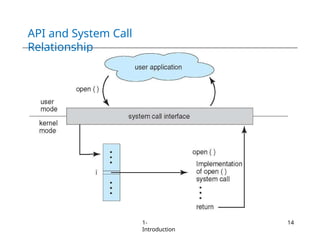
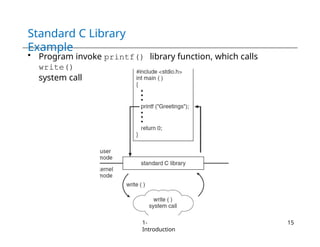
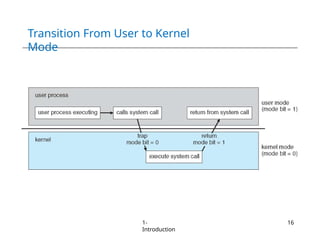
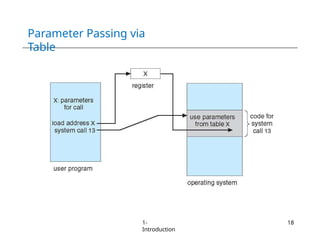
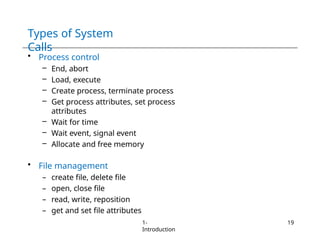
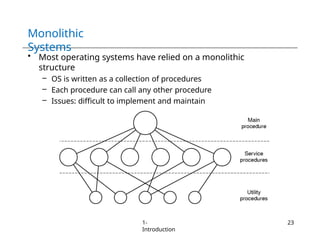
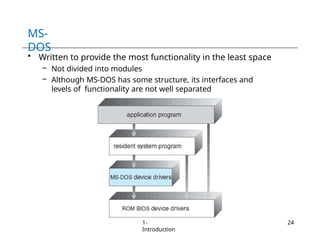
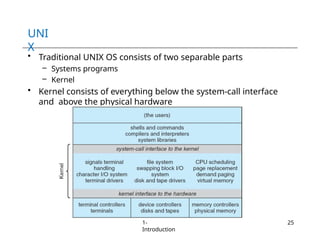
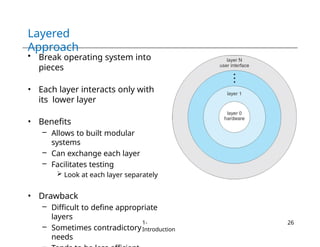
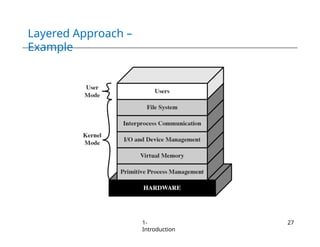
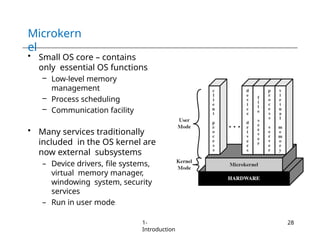
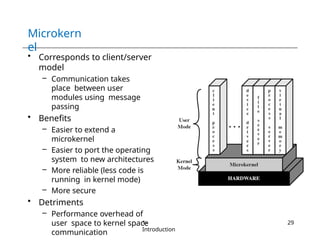
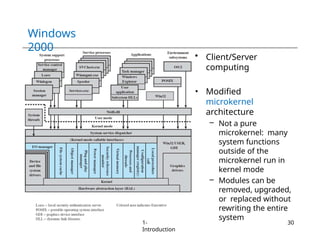
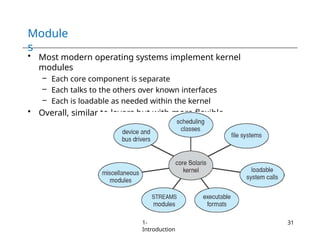
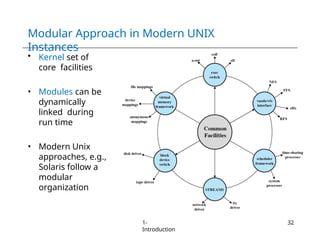
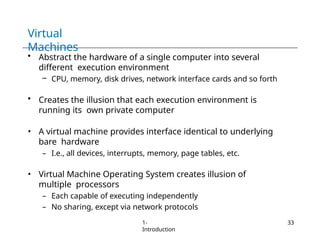
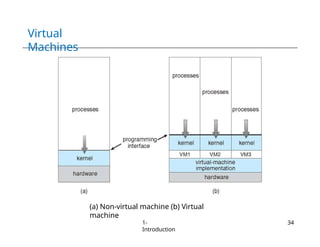
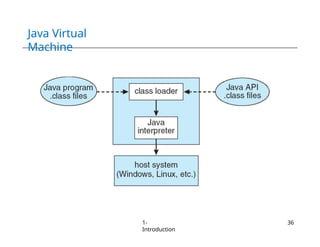
The document provides an overview of operating systems, detailing their services including user interfaces, program execution, file management, and error detection. It discusses system calls, API relationships, and the structure of operating systems including monolithic and microkernel approaches. Additionally, it covers the concept of virtual machines and the Java Virtual Machine, highlighting their role in creating isolated execution environments.