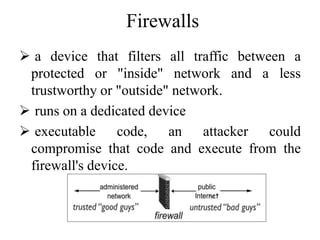
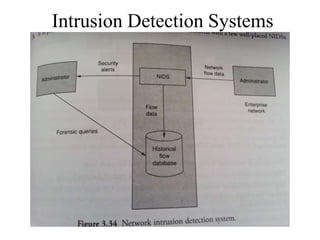
The document discusses various aspects of program security including types of flaws, malicious code, and controls against threats. It describes different types of flaws such as buffer overflows, incomplete mediation, and time-of-check to time-of-use errors. Malicious code like viruses, trojan horses, and worms are also explained. Controls during software development include following principles of modularity, encapsulation, and information hiding. Techniques like code reviews and testing aim to identify and fix flaws to enhance program security.














![Program Security
Types of flaws: Non- Malicious flaws (not
very serious)
Buffer Overflows:
A buffer (or array or string) is a space in which data can
be held.
Example: char sample[10];](https://image.slidesharecdn.com/it6701imunitii-210524101816/85/IT6701-Information-Management-Unit-2-15-320.jpg)





































![Controls Against Program Threats
Developmental Controls:
Encapsulation:
hides a component's implementation details, but it does
not necessarily mean complete isolation
"technique for packaging the information [inside a
component] in such a way as to hide what should be
hidden and make visible what is intended to be visible."](https://image.slidesharecdn.com/it6701imunitii-210524101816/85/IT6701-Information-Management-Unit-2-53-320.jpg)