Graph traversal techniques under 40 chars
•Download as PPTX, PDF•
0 likes•52 views
Non-Linear Data Structures-Graph
Report
Share
Report
Share
Recommended
More Related Content
More from SIMONTHOMAS S
More from SIMONTHOMAS S (20)
Recently uploaded
★ CALL US 9953330565 ( HOT Young Call Girls In Badarpur delhi NCR

★ CALL US 9953330565 ( HOT Young Call Girls In Badarpur delhi NCR9953056974 Low Rate Call Girls In Saket, Delhi NCR
Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR

Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR9953056974 Low Rate Call Girls In Saket, Delhi NCR
Software and Systems Engineering Standards: Verification and Validation of Sy...

Software and Systems Engineering Standards: Verification and Validation of Sy...VICTOR MAESTRE RAMIREZ
Recently uploaded (20)
Gfe Mayur Vihar Call Girls Service WhatsApp -> 9999965857 Available 24x7 ^ De...

Gfe Mayur Vihar Call Girls Service WhatsApp -> 9999965857 Available 24x7 ^ De...
OSVC_Meta-Data based Simulation Automation to overcome Verification Challenge...

OSVC_Meta-Data based Simulation Automation to overcome Verification Challenge...
★ CALL US 9953330565 ( HOT Young Call Girls In Badarpur delhi NCR

★ CALL US 9953330565 ( HOT Young Call Girls In Badarpur delhi NCR
Application of Residue Theorem to evaluate real integrations.pptx

Application of Residue Theorem to evaluate real integrations.pptx
Introduction to Microprocesso programming and interfacing.pptx

Introduction to Microprocesso programming and interfacing.pptx
Biology for Computer Engineers Course Handout.pptx

Biology for Computer Engineers Course Handout.pptx
ZXCTN 5804 / ZTE PTN / ZTE POTN / ZTE 5804 PTN / ZTE POTN 5804 ( 100/200 GE Z...

ZXCTN 5804 / ZTE PTN / ZTE POTN / ZTE 5804 PTN / ZTE POTN 5804 ( 100/200 GE Z...
CCS355 Neural Network & Deep Learning UNIT III notes and Question bank .pdf

CCS355 Neural Network & Deep Learning UNIT III notes and Question bank .pdf
APPLICATIONS-AC/DC DRIVES-OPERATING CHARACTERISTICS

APPLICATIONS-AC/DC DRIVES-OPERATING CHARACTERISTICS
Model Call Girl in Narela Delhi reach out to us at 🔝8264348440🔝

Model Call Girl in Narela Delhi reach out to us at 🔝8264348440🔝
Gurgaon ✡️9711147426✨Call In girls Gurgaon Sector 51 escort service

Gurgaon ✡️9711147426✨Call In girls Gurgaon Sector 51 escort service
High Profile Call Girls Nagpur Isha Call 7001035870 Meet With Nagpur Escorts

High Profile Call Girls Nagpur Isha Call 7001035870 Meet With Nagpur Escorts
Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR

Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR
Software and Systems Engineering Standards: Verification and Validation of Sy...

Software and Systems Engineering Standards: Verification and Validation of Sy...
Exploring_Network_Security_with_JA3_by_Rakesh Seal.pptx

Exploring_Network_Security_with_JA3_by_Rakesh Seal.pptx
chaitra-1.pptx fake news detection using machine learning

chaitra-1.pptx fake news detection using machine learning
Graph traversal techniques under 40 chars
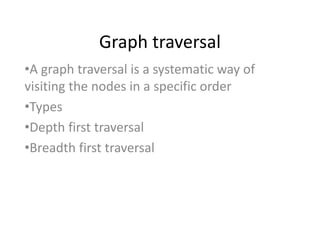
- 1. Graph traversal •A graph traversal is a systematic way of visiting the nodes in a specific order •Types •Depth first traversal •Breadth first traversal
- 2. Breadth first traversal(BFS) • Graph G starts from an unvisited vertex u • Then all unvisited vertices vi adjacent to u are visited and then all unvisited vertices wj adjacent to vj are visited and so on
- 3. • Choose any node in the graph designate it as the search node & mark it as visited • Using the adjacency matrix of the graph, find all the unvisited adjacent nodes to the search node and enqueue them into the queue Q • Then the search node is dequeued from the queue. Mark that node as visited and select the new search node • Repeat step 2 & 3 using the new search node
- 4. Void BFS(vertex u) { initialize queue Q; visited[u]=1; enqueue(u,Q); while(!isempty) { u= Dequeue(Q) print u for all vertices v adjacent to u do if (visited[v]==0) then { Enqueue(v,Q) visited[v]=1; } } }
- 5. applications • To check whether the graph is connected or not
- 6. Depth first search • Depth first search works by selecting one vertex V of G as a start vertex • V is marked visited • Then each unvisited vertex adjacent to V is searched using depth first search recursively • This process continues until a dead end / no adjacent unvisited vertices is encountered
- 7. 1. Choose any node in the graph. Designate it as the search node and mark it as visited 2. Using the adjacency matrix of the graph, find a node adjacent to the search node that has not been visited yet. Designate this as the new search node and mark it as visited. 3. Repeat step 1 & 2 using the new search node
- 8. Routine for DFS Void DFS(Vertex V) { visited[V]=True; for each W adjacent to V if (! Visited[W]) DFS(W); }
