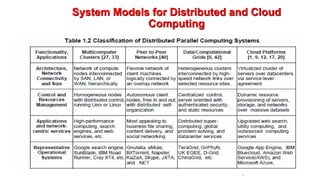
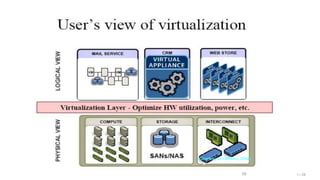
The document discusses cloud and big data analytics, focusing on the enabling technologies for network-based systems, virtualization, and the evolution of high-performance computing towards cloud computing over the past 30 years. It covers various models like infrastructure as a service (IaaS) and platform as a service (PaaS), detailing the advantages and disadvantages of virtualization at different implementation levels. Additionally, it highlights cloud computing as a new paradigm allowing on-demand access to distributed resources and addresses the challenges associated with its adoption.













































































![81
Copyright © 2012, Elsevier Inc. All rights reserved. 1 - 81
Multi-Core Virtualization:
VCPU vs. traditional CPU
Figure 3.16 Four VCPUs are exposed to the software, only three cores are actually present. VCPUs V0, V1, and V3 have
been transparently migrated, while VCPU V2 has been transparently suspended. (Courtesy of Wells, et al., “Dynamic
Heterogeneity and the Need for Multicore Virtualization”, ACM SIGOPS Operating Systems Review, ACM Press, 2009 [68] )](https://image.slidesharecdn.com/it19741uniticloudenablingtechnologies-220903044909-26b77f27/85/CLOUD-ENABLING-TECHNOLOGIES-pptx-81-320.jpg)






























