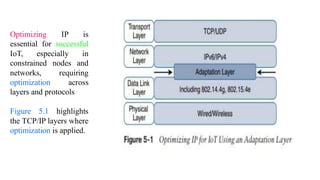
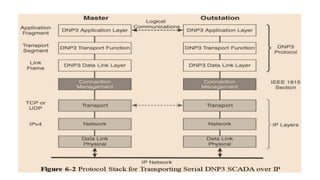
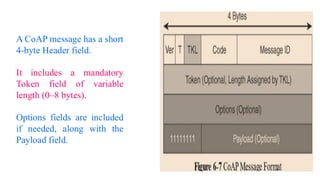
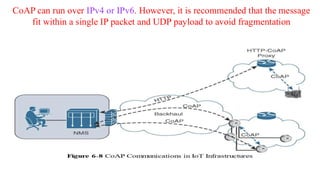
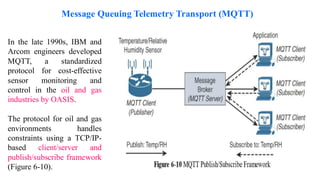
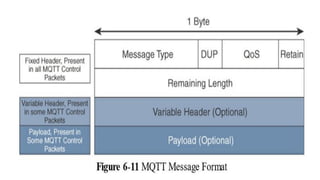
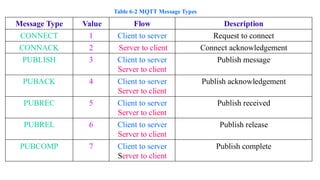
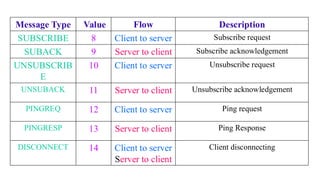
The document discusses the role of Internet Protocol (IP) as the network layer for Internet of Things (IoT) solutions, highlighting its advantages such as scalability, versatility, and standardization. It covers the optimization challenges in constrained networks and nodes, the differences between adopting IP or adapting existing protocols, and essential IoT application protocols. Additionally, it addresses transport methods for data transmission in IoT, emphasizing the choice between Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) based on specific IoT requirements.