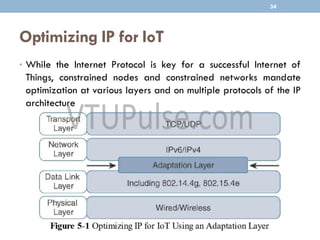
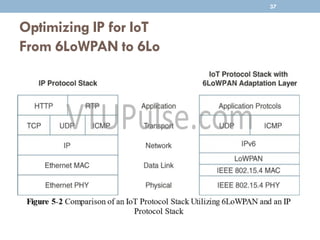
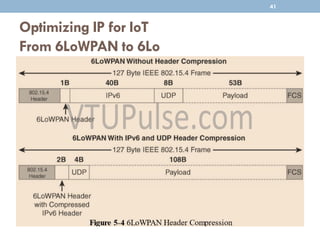
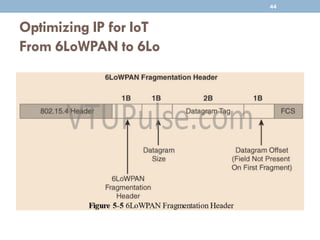
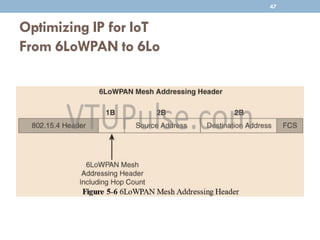
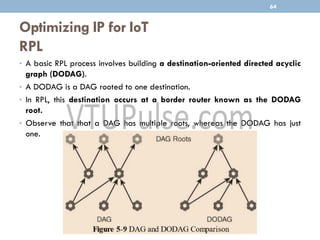
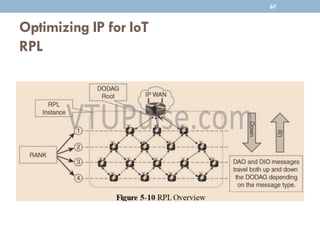
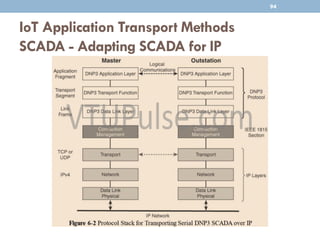
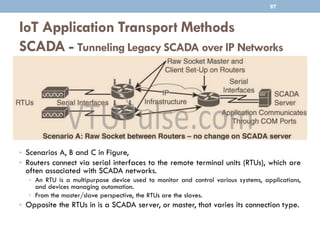
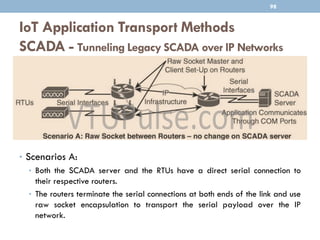
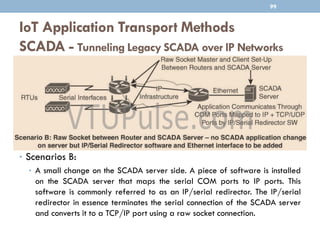
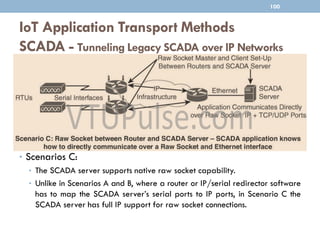
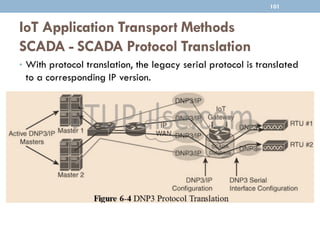
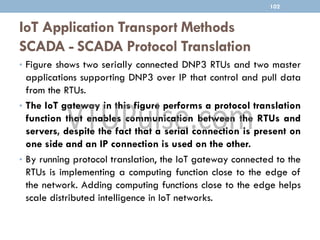
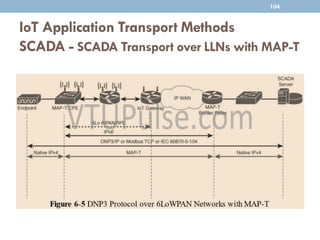
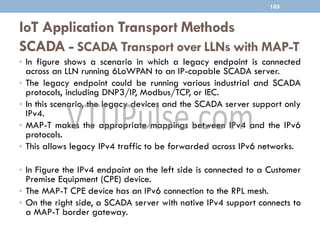
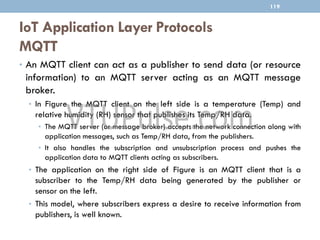
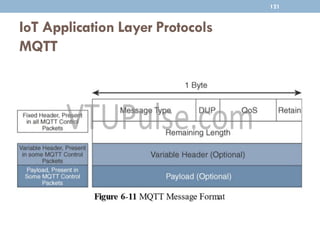
The document discusses IP as the network layer for the Internet of Things. It outlines the business case for using IP, including advantages like being open, versatile, ubiquitous, scalable, secure, stable, and enabling innovation. It also discusses the need to optimize IP for constrained IoT devices and networks. Common protocols for IoT utilizing IP include 6LoWPAN, 6TiSCH, and RPL. Adoption of IP may involve replacing non-IP layers completely or using application layer gateways for adaptation between IP and non-IP layers. Factors like data flow direction, overhead, and network diversity should be considered when choosing an adoption or adaptation approach.