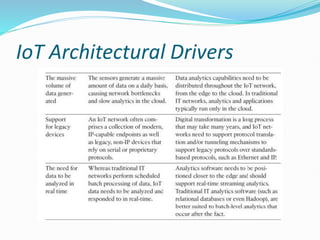
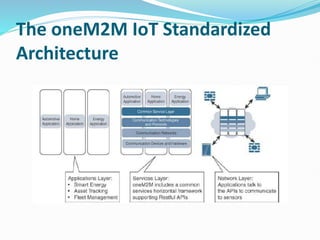
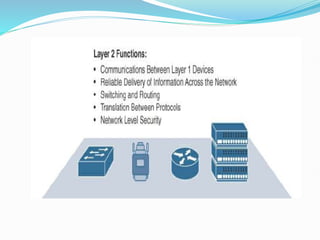
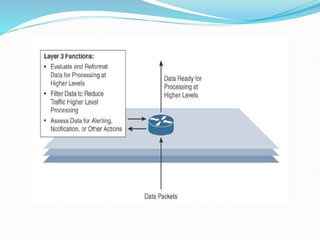
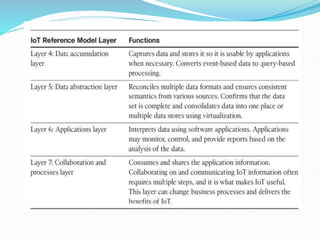
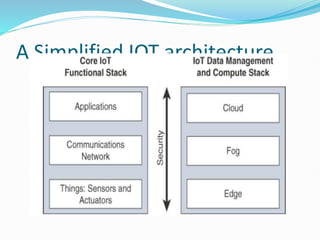
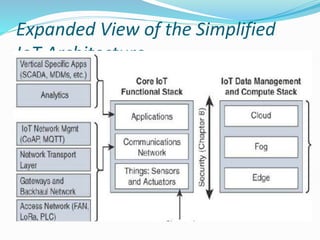
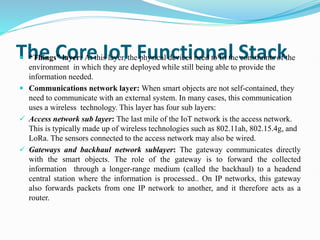
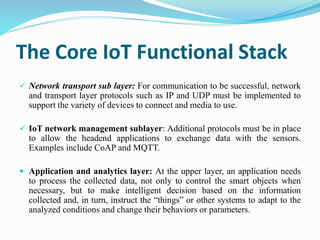
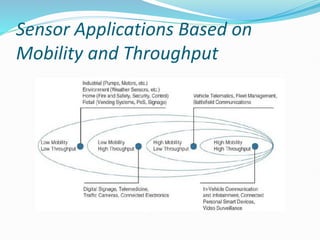
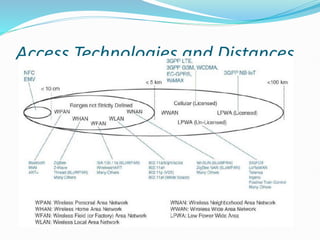
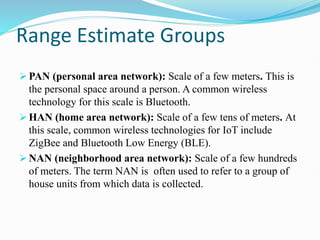
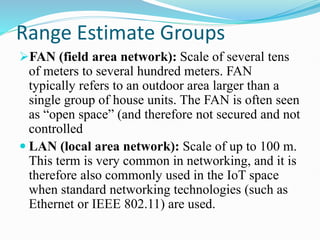
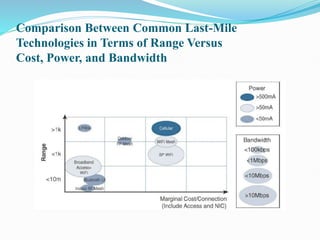
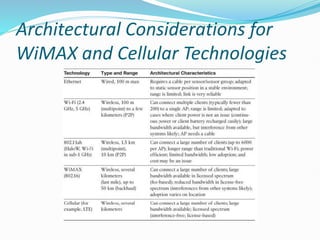
The document discusses Internet of Things (IoT) network architecture and design. It provides an overview of key aspects of IoT architecture including drivers behind new network architectures, comparing IoT architectures from ETSI and IoT World Forum, and presenting a simplified IoT architecture model. The core IoT functional stack is also explained, covering the things layer, communications network layer, and application and analytics layer. Specific protocols and technologies for each layer are described such as LoRa, CoAP, MQTT, and more.