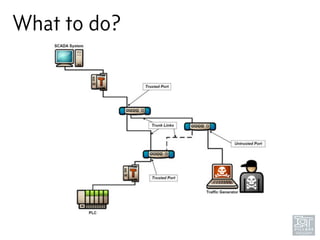
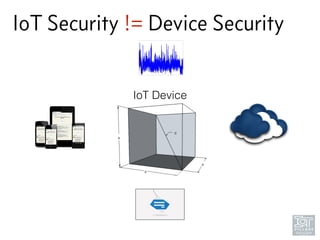
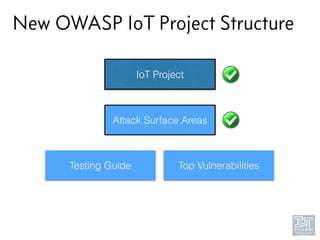
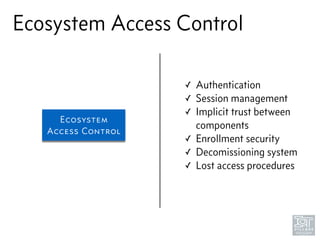
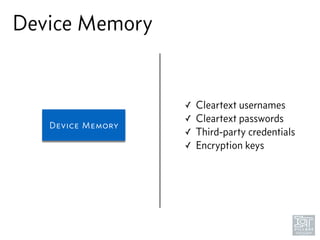
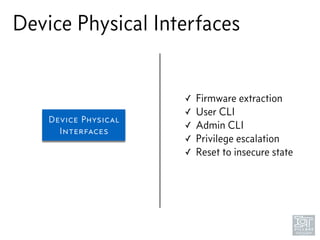
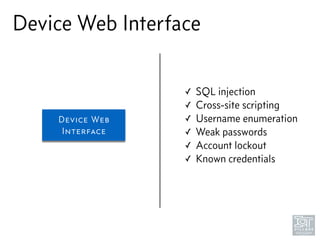
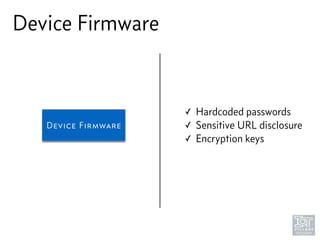
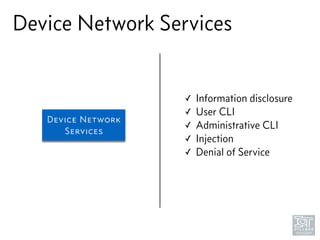
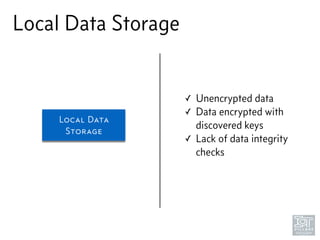
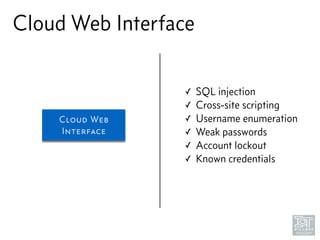
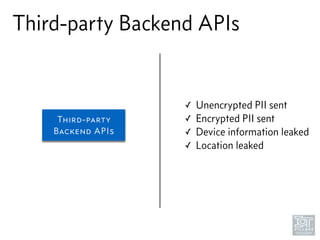
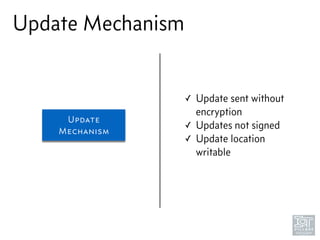
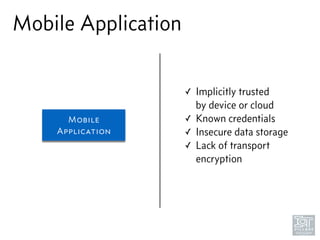
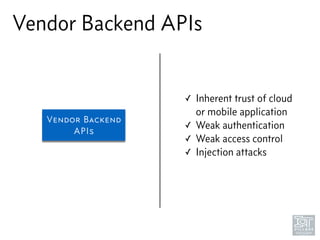
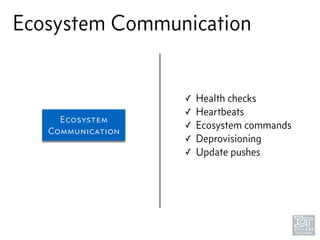
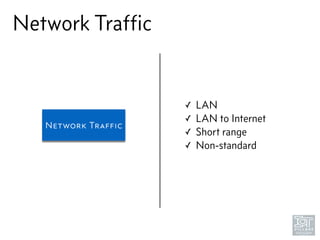
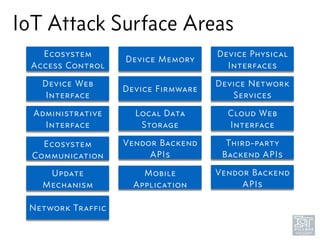
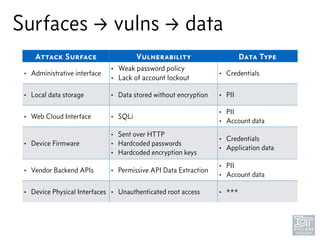
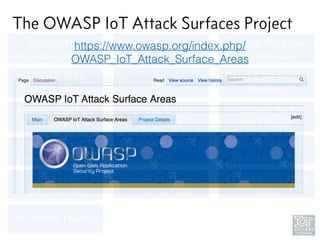
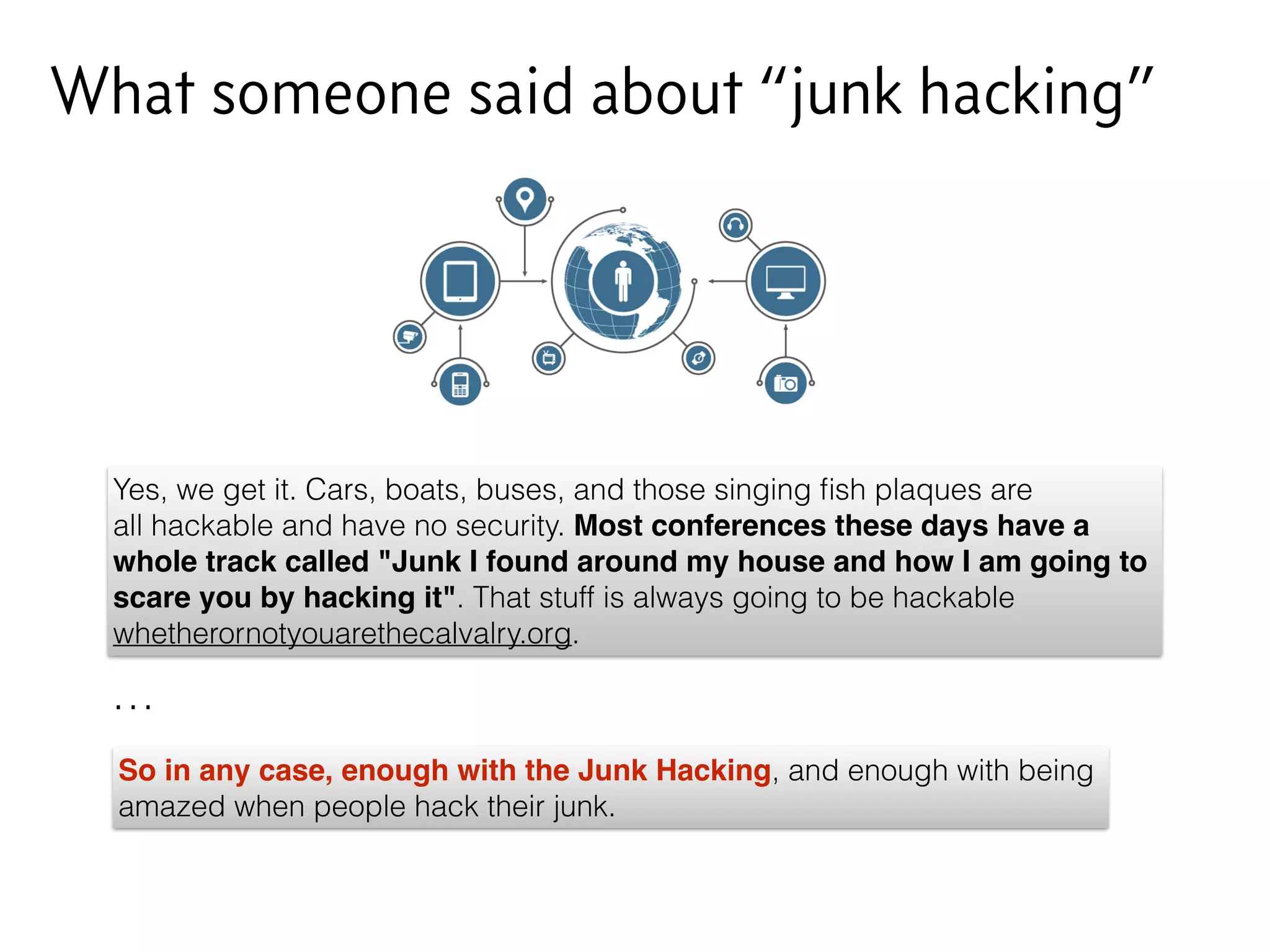
The document discusses junk hacking and vulnerability research of IoT devices. It notes that many IoT devices have no security and can easily be hacked. It argues that while demonstrating vulnerabilities in everyday devices is interesting, the "junk hacking" trend has become overdone at security conferences. The document advocates moving the discussion beyond just identifying vulnerabilities and toward developing a standardized approach for assessing IoT security across different device types and platforms.


![Defining IoT ๏ [ WIKIPEDIA ] The Internet of Things (IoT)
is the network of physical objects or "things"
embedded with electronics, software,
sensors and connectivity to enable it to
achieve greater value and service by
exchanging data with the manufacturer,
operator and/or other connected devices.
๏ [ OXFORD ] A proposed development of the
Internet in which everyday objects have
network connectivity, allowing them to send
and receive data.
๏ [ MY PREFERRED ] The interface between
the physical and digital world that allows
one to gather information from—and
control—everyday objects.](https://image.slidesharecdn.com/iotattacksurfaces-defcon2015-150813155432-lva1-app6892/85/IoT-Attack-Surfaces-DEFCON-2015-5-320.jpg)