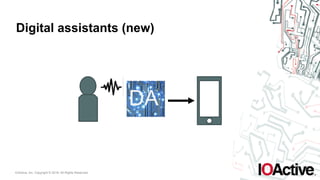
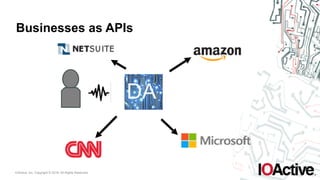
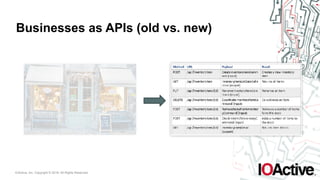
The document outlines key technology forces affecting applications, emphasizing a shift towards natural, real-time, and continuous user interfaces, including voice and chat interfaces. It highlights the evolution of businesses as APIs, suggesting that interaction with digital assistants (DAs) will redefine application usability. The key takeaways encourage developers to consider usability trends, the potential for bot functionality, and the future landscape of applications dominated by APIs.