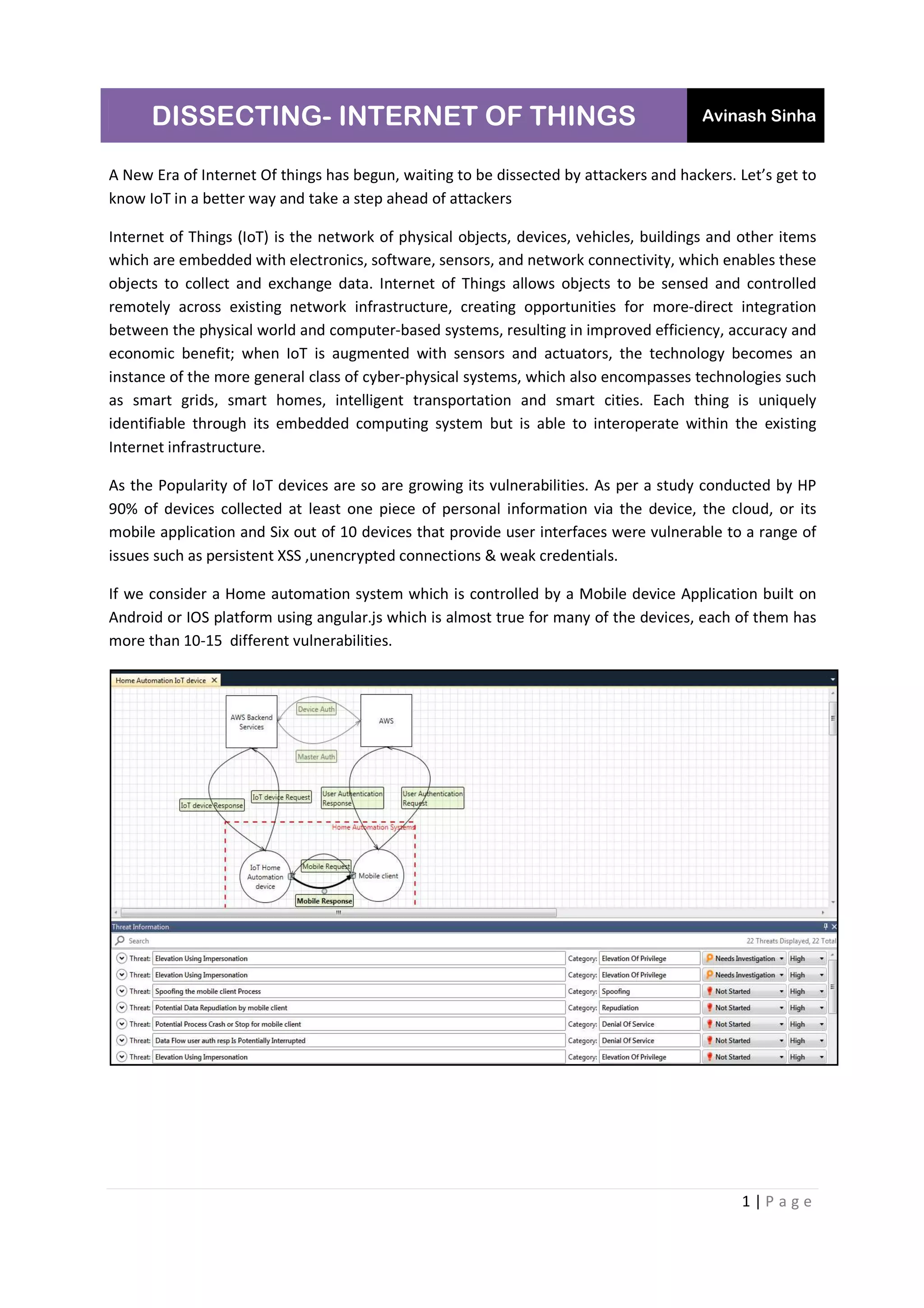
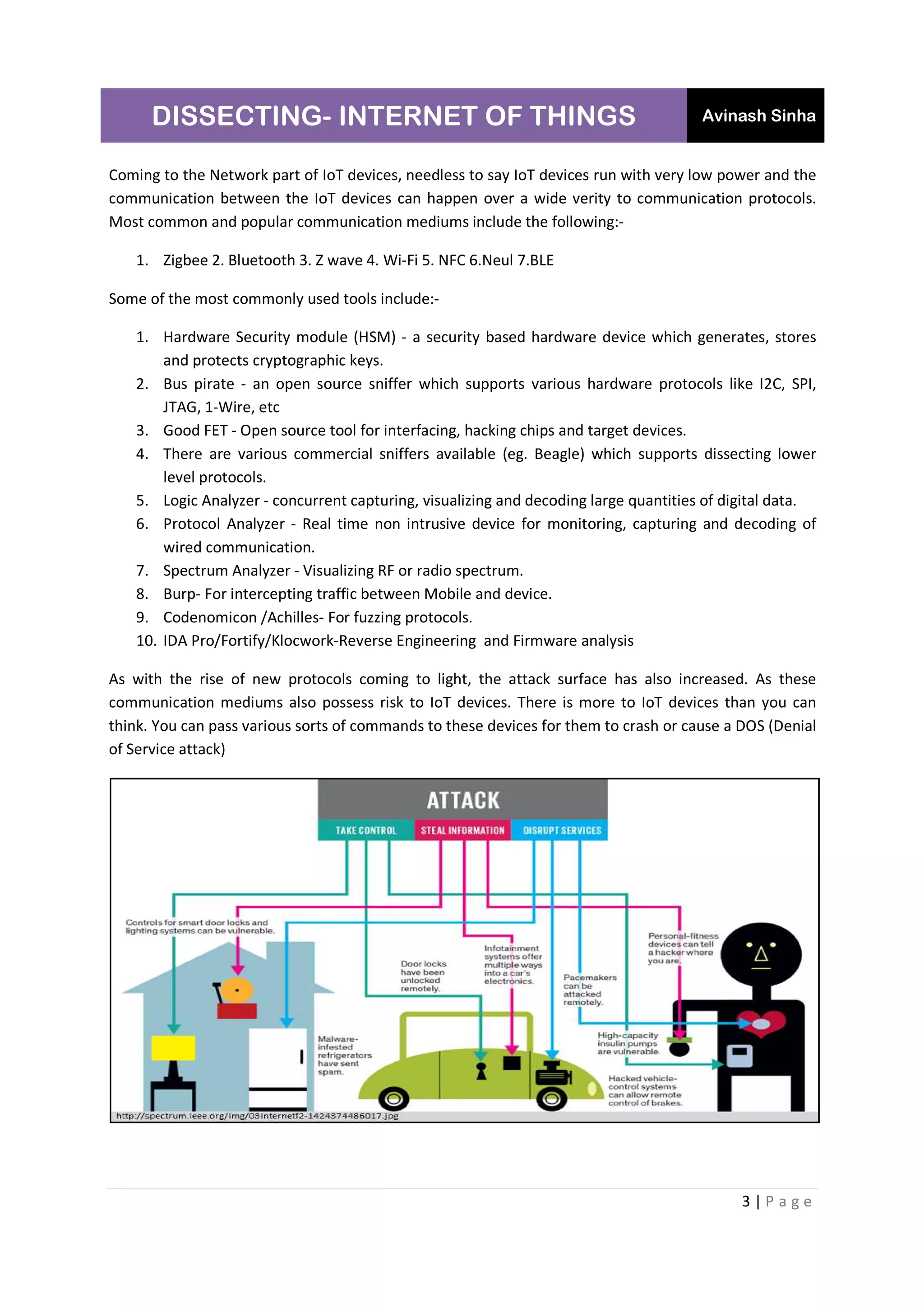
The document discusses the Internet of Things (IoT), its vulnerabilities, and the associated security risks posed by attackers. It highlights various weaknesses in IoT devices, particularly in home automation systems, and categorizes them based on the OWASP Top 10 IoT vulnerabilities. The author, Avinash Sinha, emphasizes the growing need for security in IoT as the number of devices increases, predicting significant usage by consumers and potential hackers.