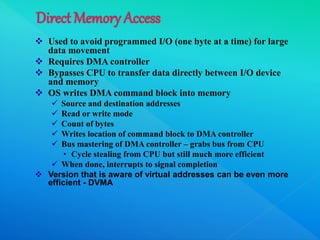
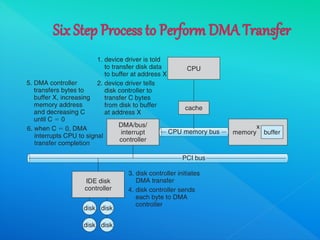
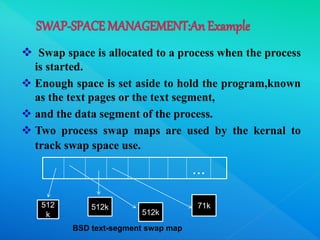
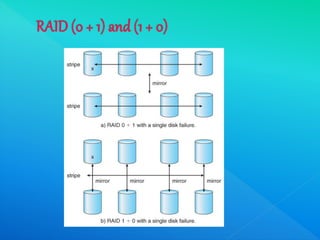
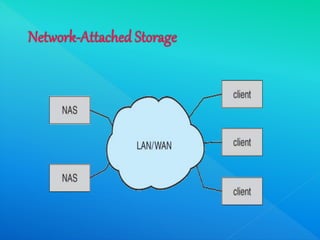
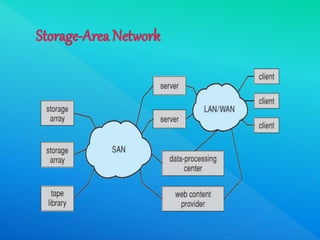
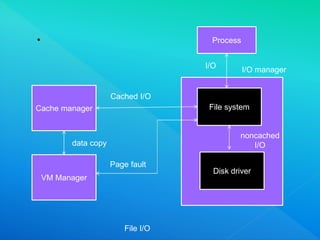
The document provides information about I/O systems and a case study, including details about disk structure, disk scheduling algorithms, disk management techniques, direct memory access, swap space management, RAID structure, disk attachment methods, and features of the Windows 2000 and MS-DOS operating systems. Key points covered include how disks are addressed as logical blocks, techniques for minimizing seek time and maximizing disk bandwidth, common disk scheduling algorithms like SSTF and SCAN, and how swap space is allocated and managed in different operating systems.