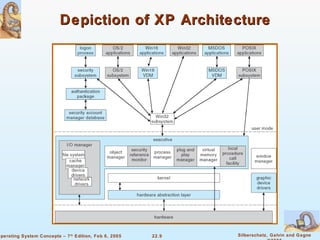
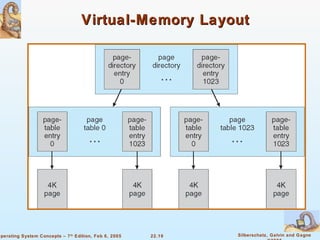
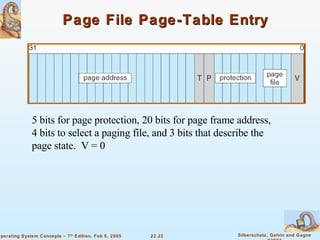
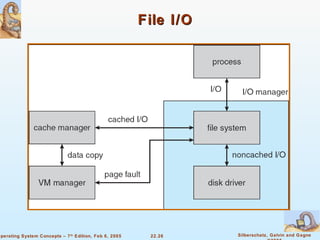
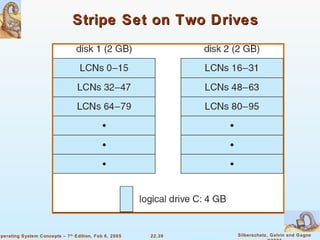
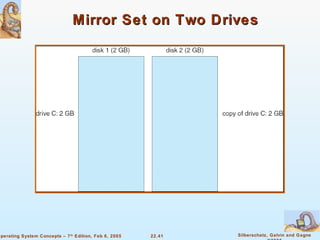
The document provides a comprehensive overview of Windows XP, detailing its history, design principles, system components, and networking capabilities. It emphasizes its extensibility, reliability, and compatibility with various operating systems while outlining key features like the file system organization, process management, and security protocols. Furthermore, it discusses networking protocols such as TCP/IP and SMB, and how XP supports both peer-to-peer and client/server networking models.