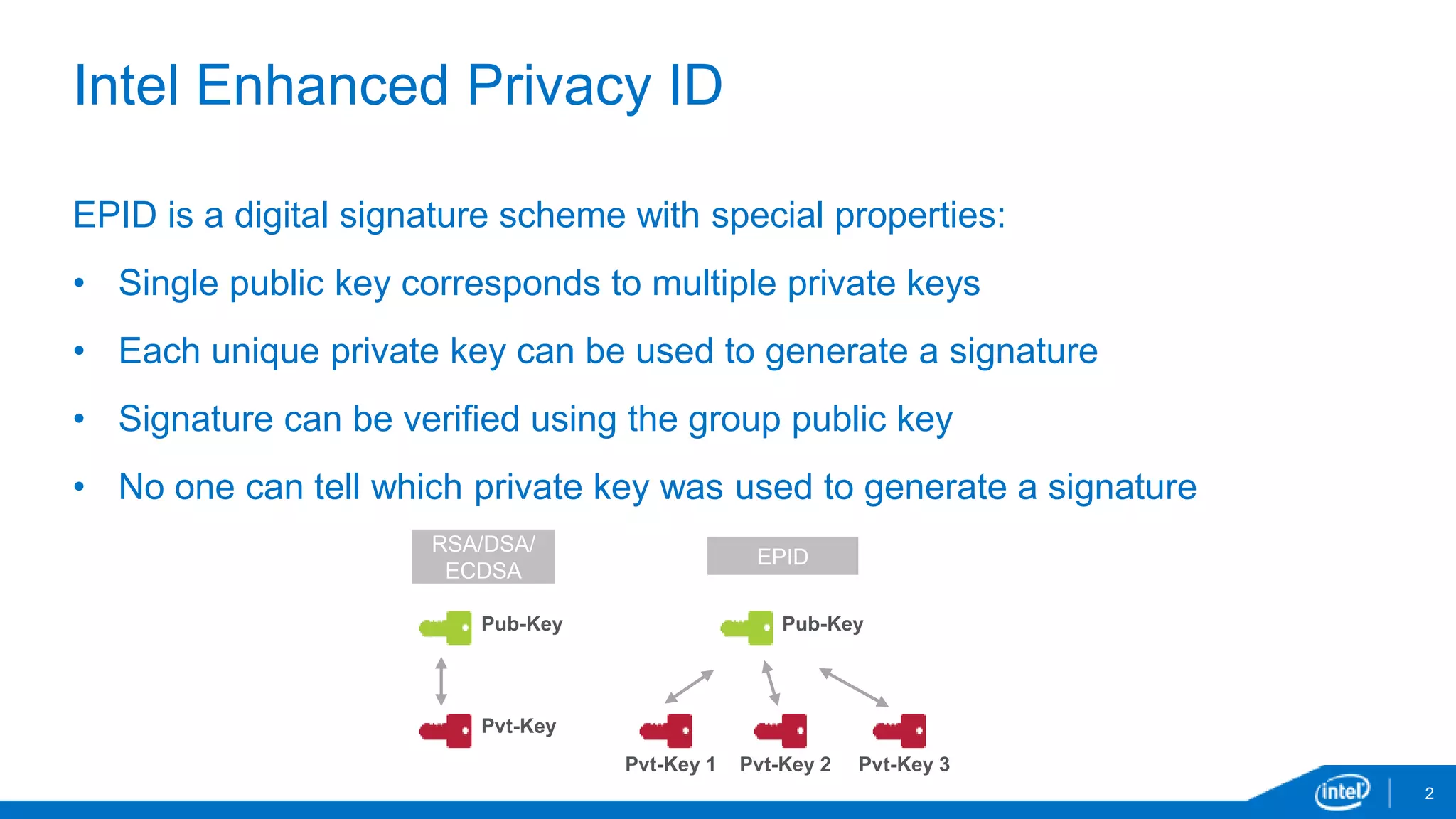
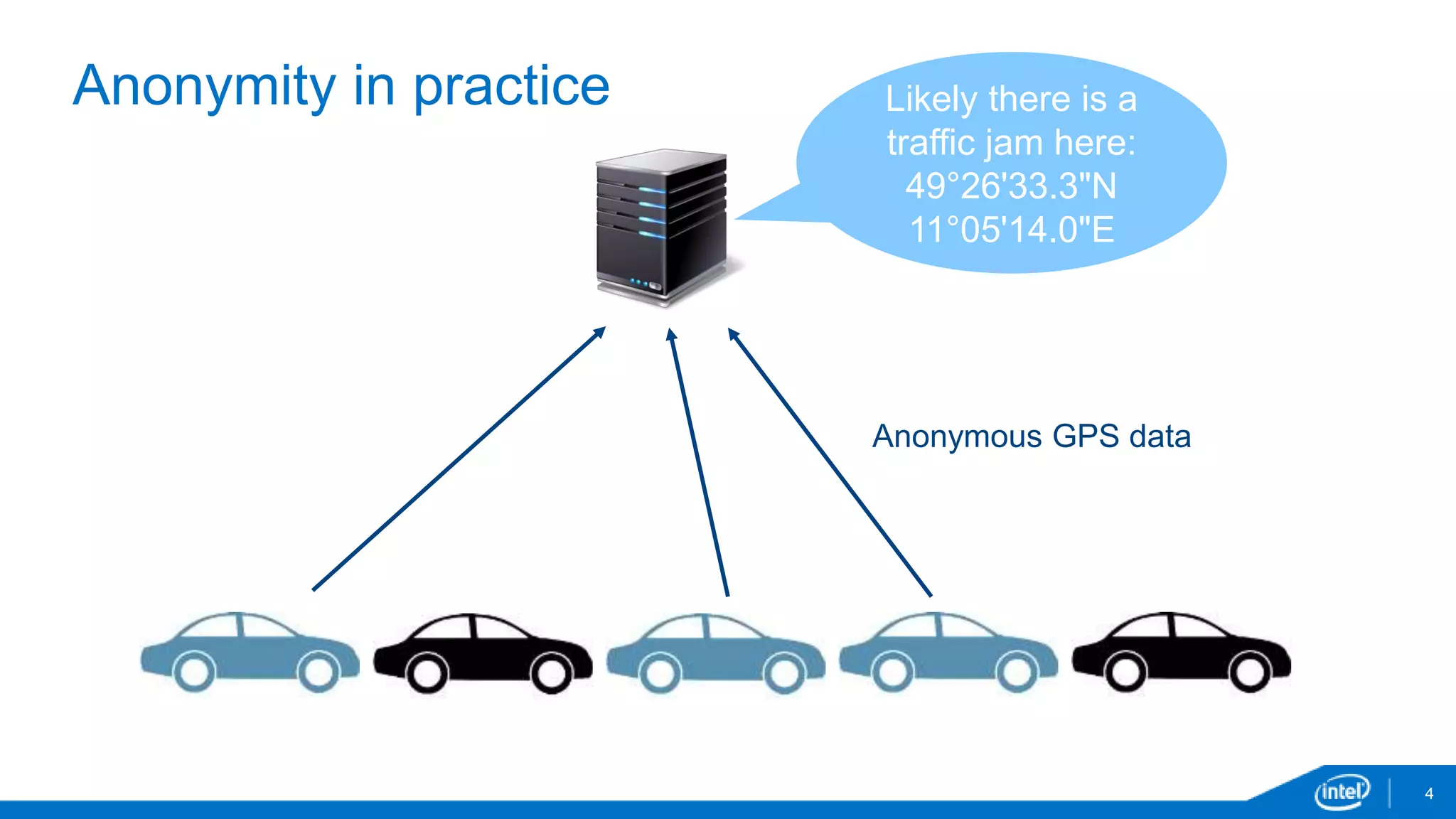
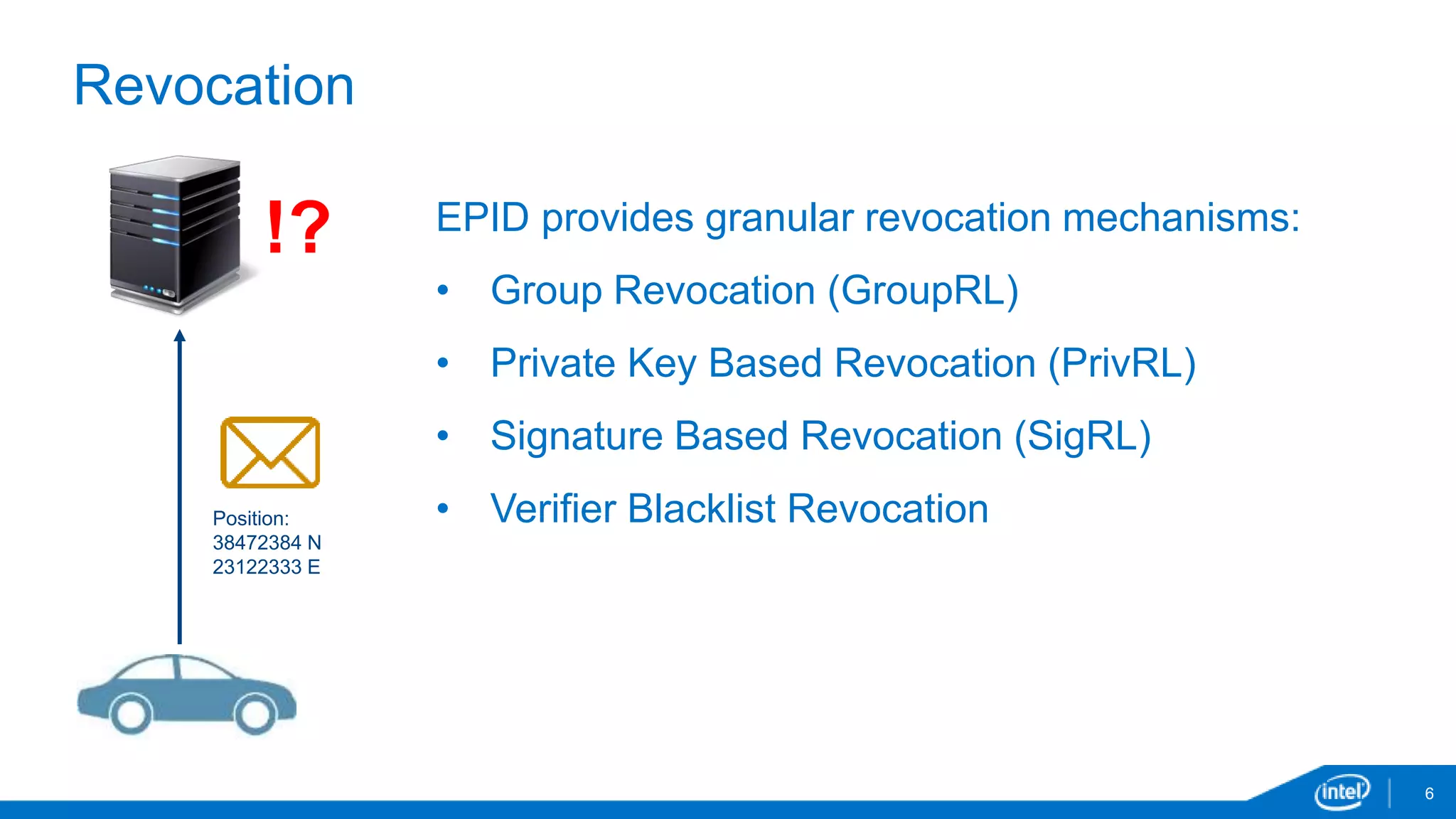
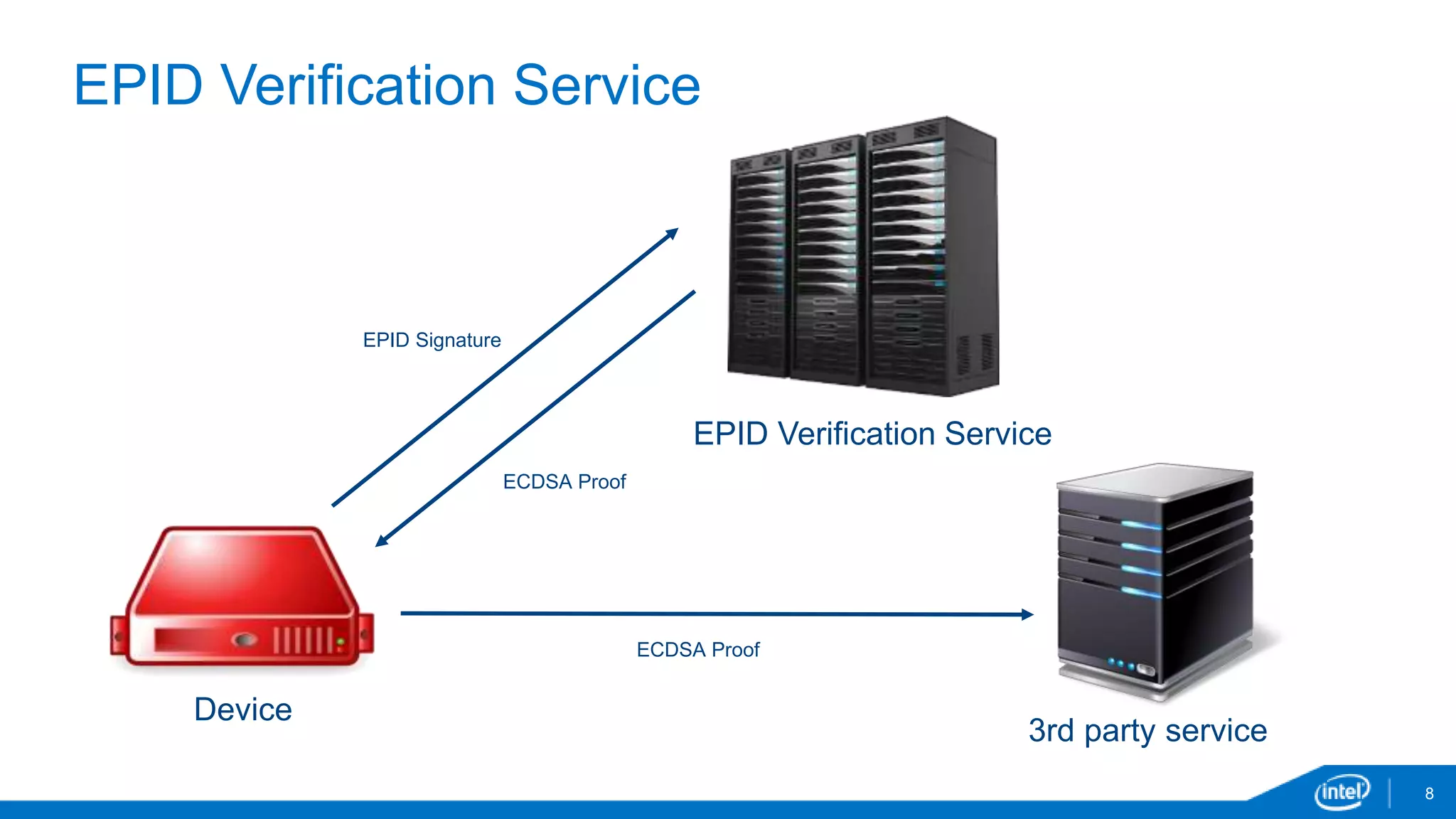
EPID is a digital signature scheme that allows for anonymity and privacy. It uses a single public key that corresponds to multiple private keys, so the private key used to generate a signature cannot be identified. EPID signatures can be verified using the group public key. EPID provides granular revocation mechanisms and has been shipping since 2008 in Intel processors. It is used for technologies like Intel Insider, Intel TXT, Intel IPT and Intel SGX.