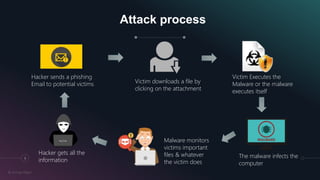
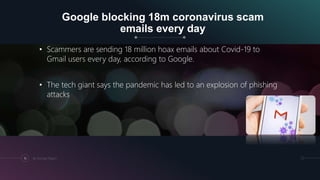
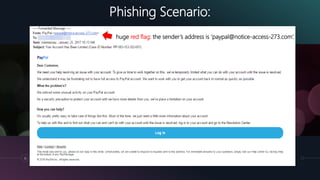
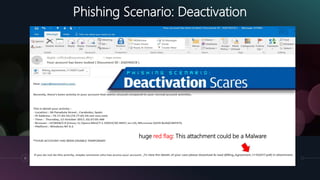
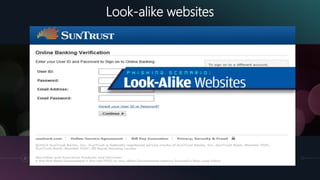
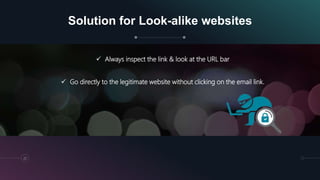
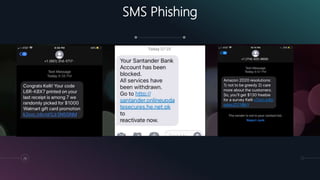
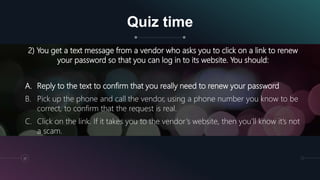
The document is a presentation by Kumayl Rajani on cybersecurity, detailing concepts such as hacking, malware, and phishing attacks. It emphasizes the importance of cybersecurity awareness and provides prevention tips against various cyber threats, including ransomware and phishing scams. Training programs for different demographics are also mentioned, highlighting the need for education in cybersecurity.