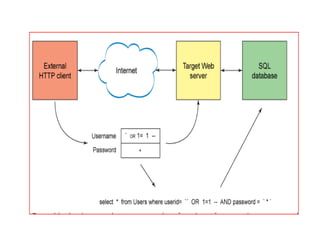
This document summarizes the steps to perform a SQL injection attack on a vulnerable website. It begins by finding a dynamic page that interacts with a database, then determines the number of columns and vulnerable columns. Next, it checks the MySQL version number and retrieves table names from the information schema. Finally, it retrieves column names and extracts data from columns by concatenating values with delimiters. The attack was performed on http://leettime.net/sqlninja.com/tasks/basic_ch1.php?id=1 in 7 steps to demonstrate a SQL injection technique.