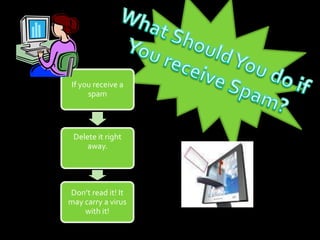
The document discusses internet safety for children, emphasizing the importance of cybersecurity, educating kids about online risks, and providing a kid-safe search engine. It addresses issues like spam, netiquette, and chat room safety, advising against sharing personal information. Tips include using nicknames in chat rooms and reporting uncomfortable situations to adults.