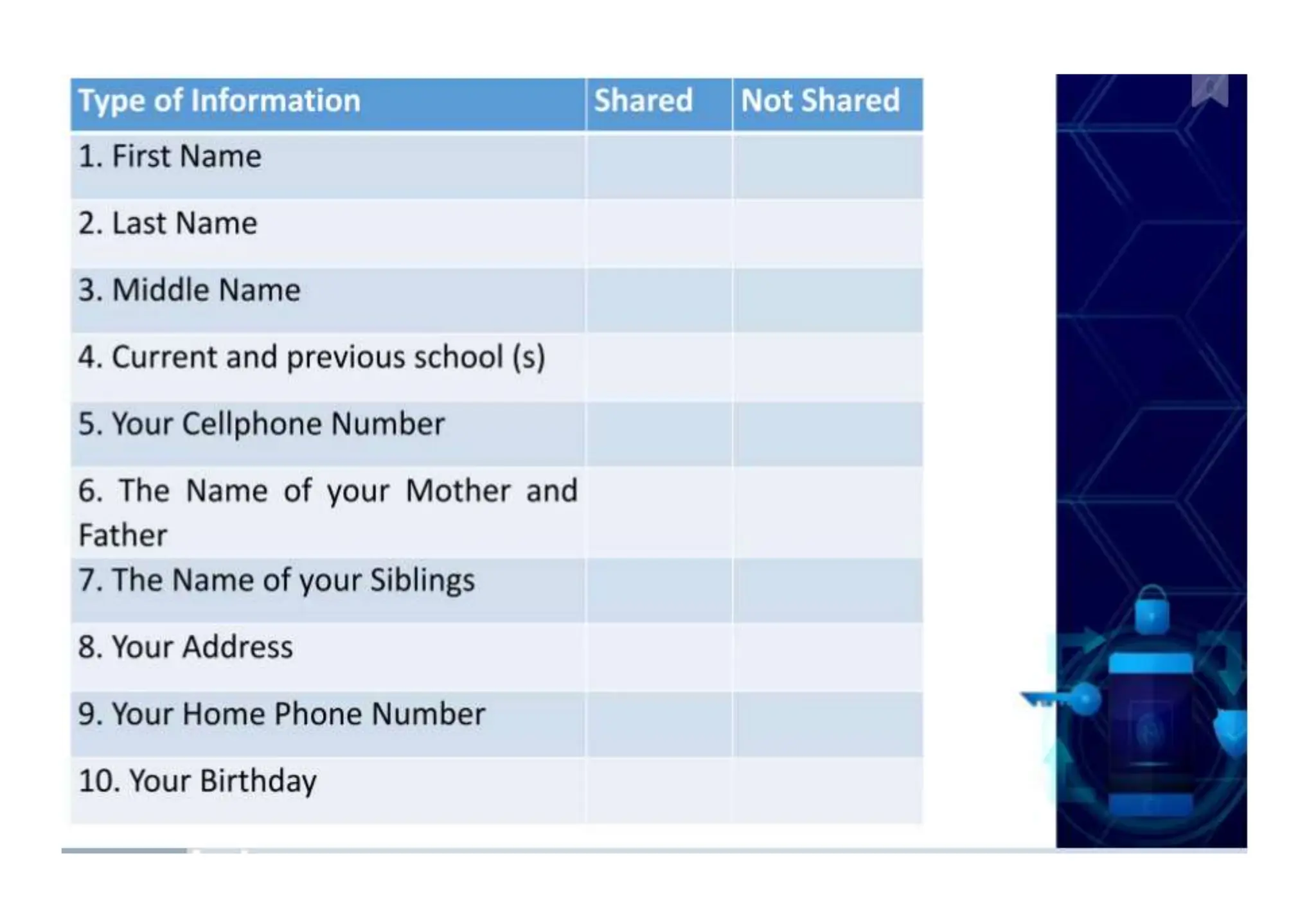
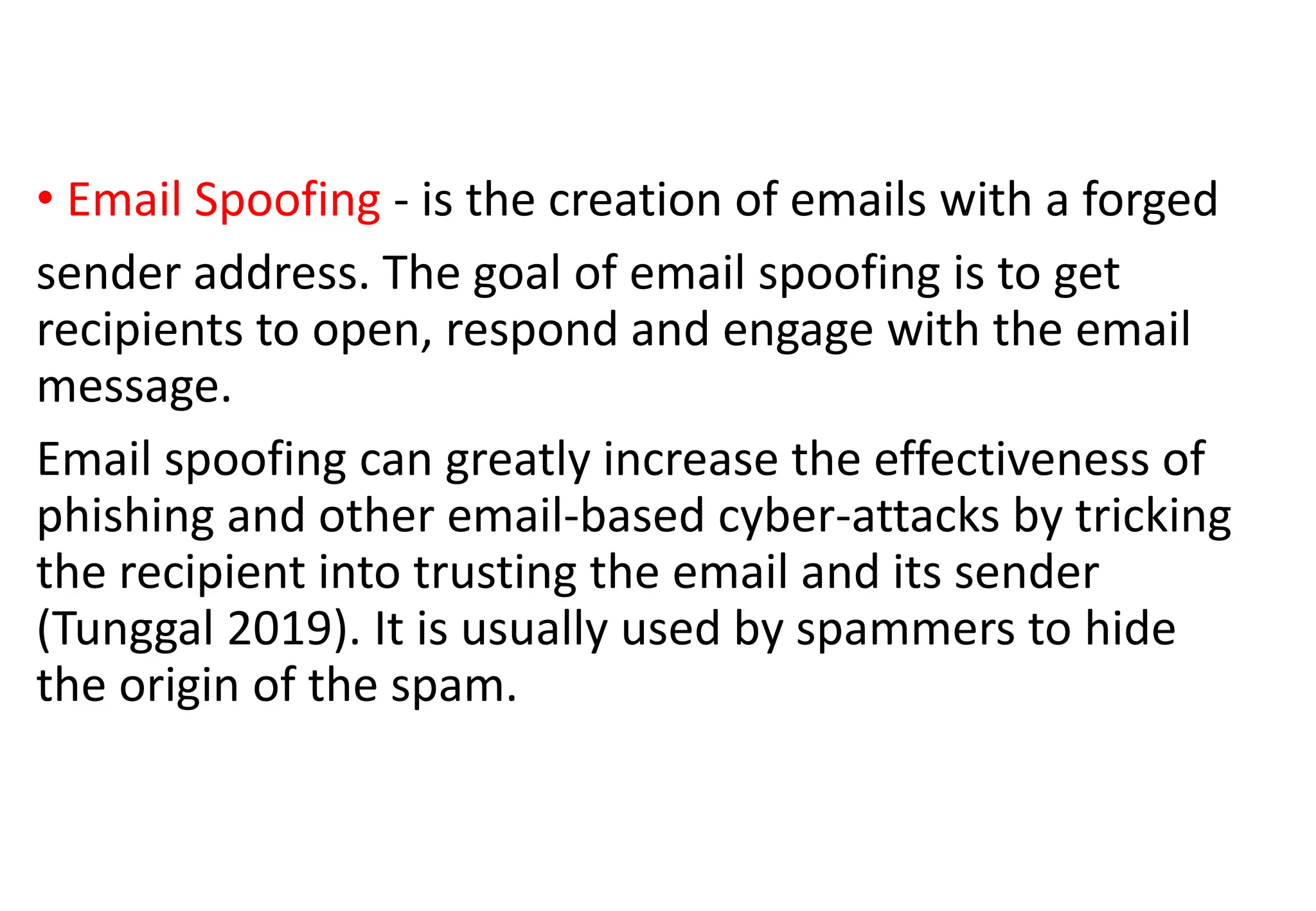
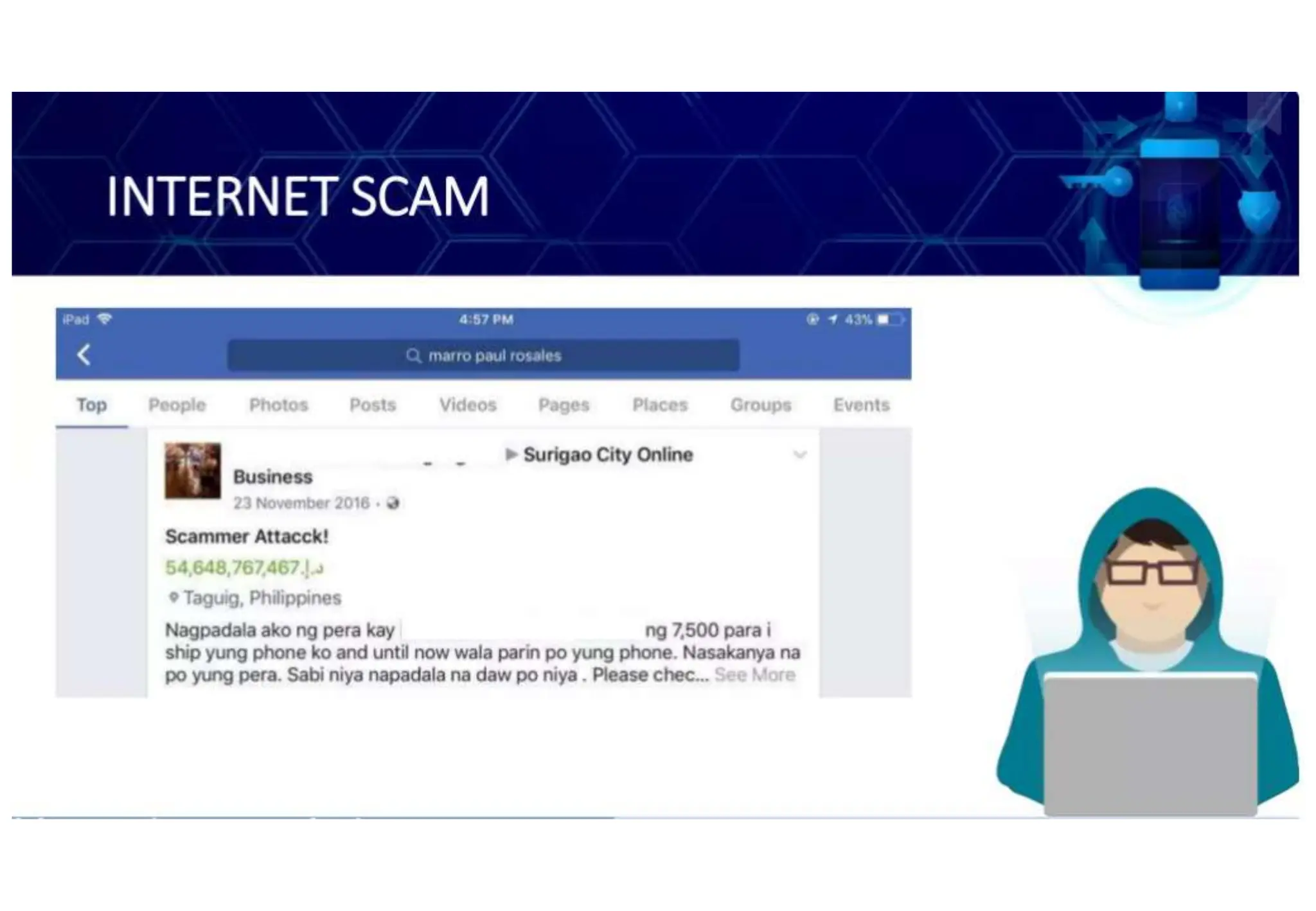
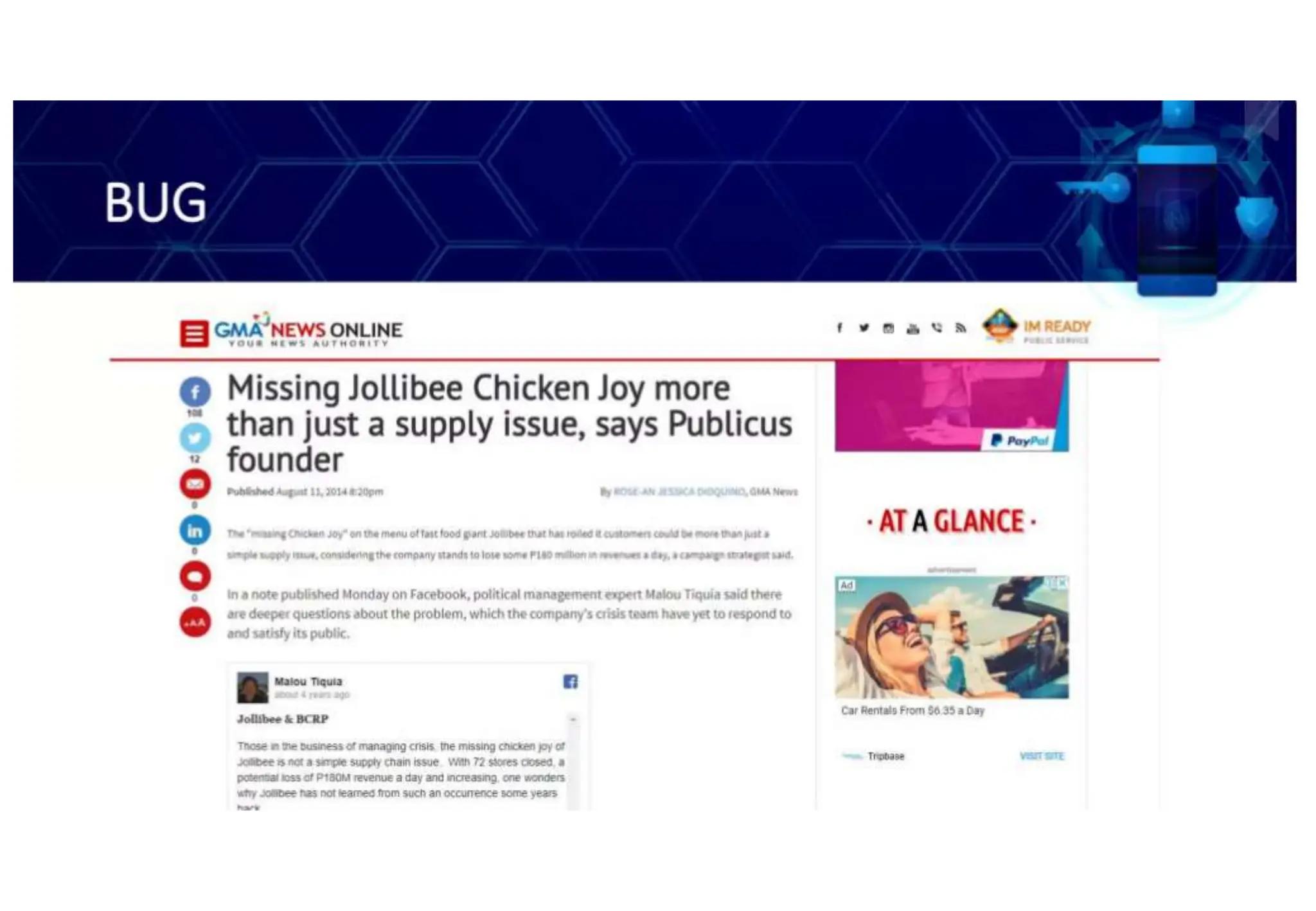
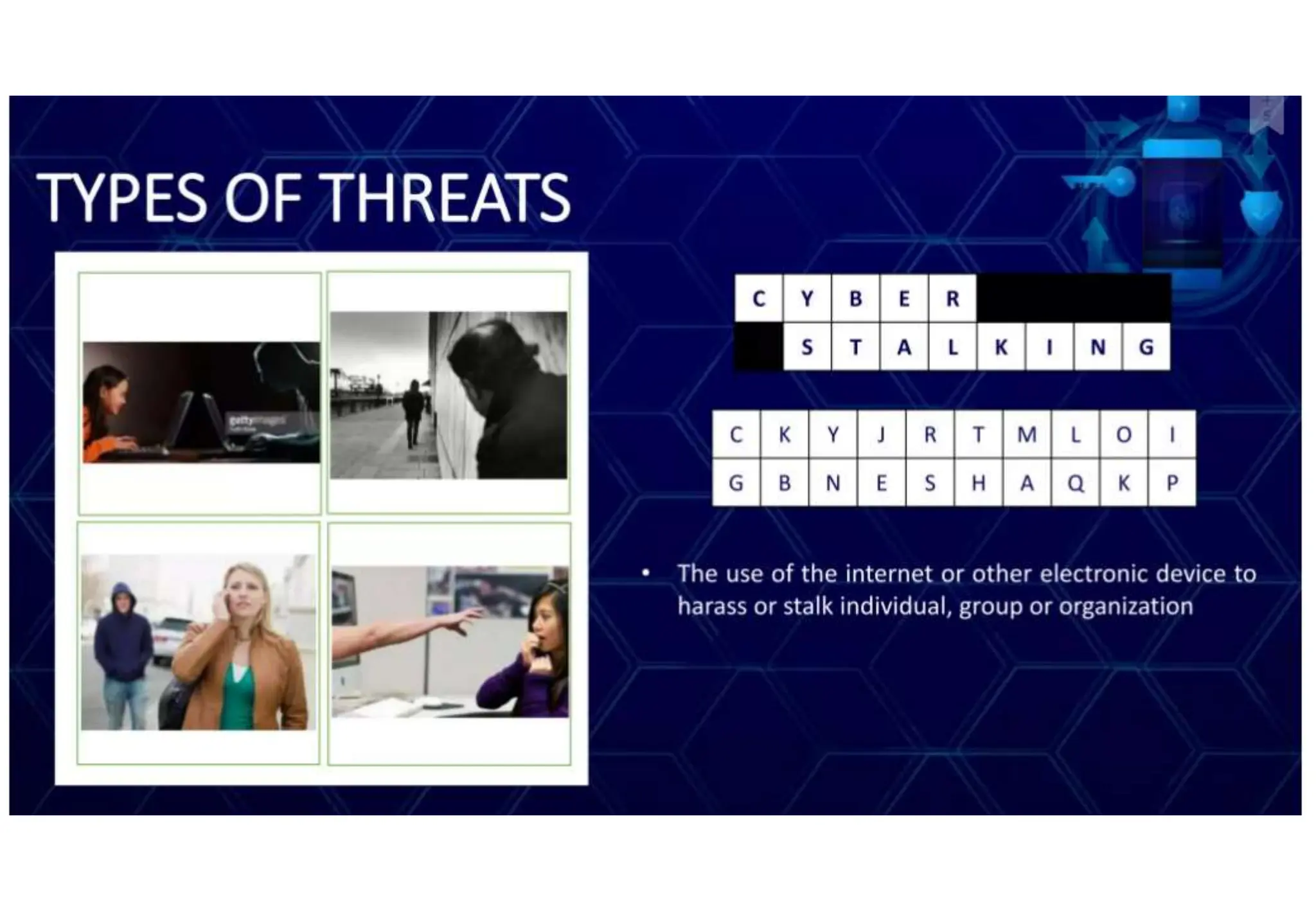
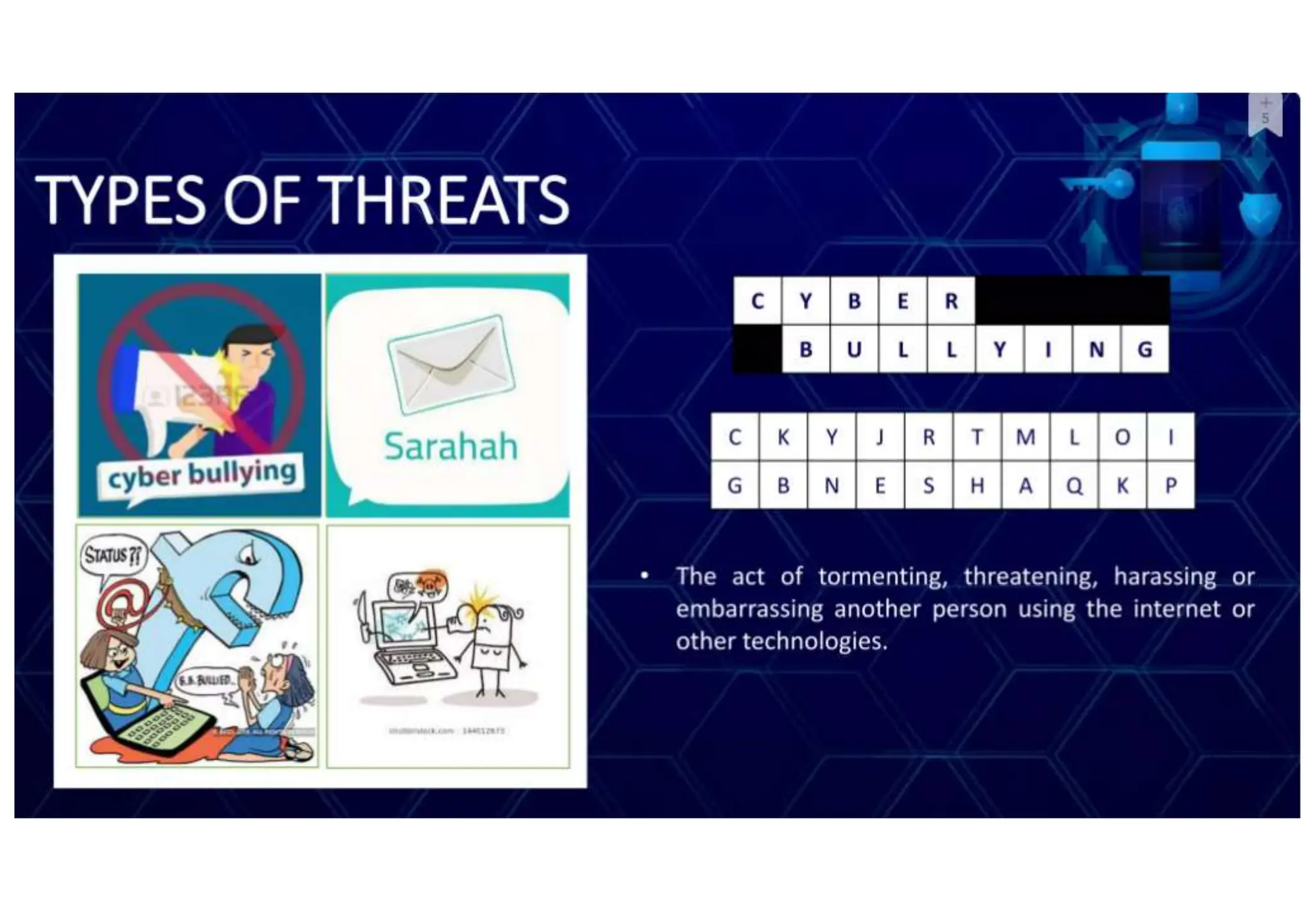
The document addresses the importance of online safety, security, ethics, and etiquette as society increasingly relies on information and communication technologies. It outlines various internet threats such as phishing, cyberbullying, and online predation, while emphasizing the necessity of protecting personal information and adhering to ethical online behavior. The text provides a list of netiquette rules to guide appropriate online conduct and safeguard privacy.