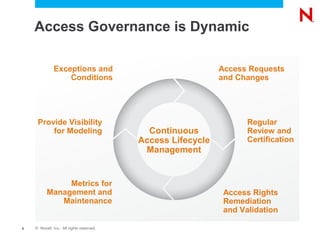
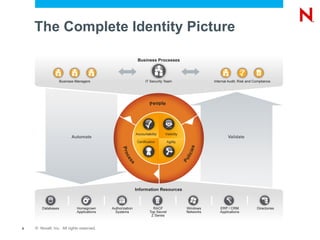
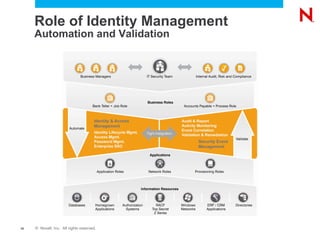
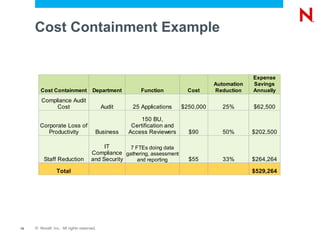
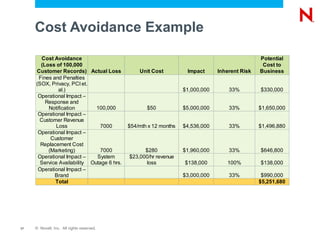
The document discusses Novell's Access Governance Suite, which helps organizations reduce costs, manage complexity, and mitigate risks related to access governance and identity management. It outlines the growing risks and regulations organizations face, and how the suite provides visibility and automation to help with continuous access lifecycle management. Implementing the suite can help contain costs through reduced compliance audit costs, improved productivity, and staff redeployment. It can also help avoid costs from fines, loss of customers or revenue, and operational impacts. The suite further helps avoid risks from inappropriate access, aged entitlements, and orphaned accounts. The document calls organizations to schedule demonstrations and assessments to build business cases for implementing access governance solutions.