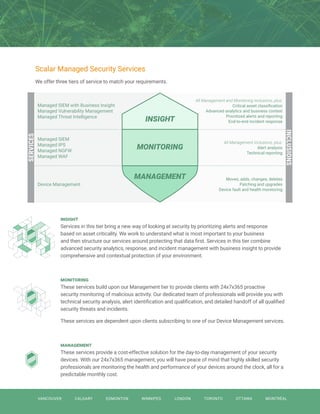
This document describes Scalar's managed security services. It notes that cyber attacks are increasing in frequency and severity, posing a major challenge for organizations. While security has become a top priority, many companies lack the in-house expertise to effectively manage their security. Scalar's managed security services allow companies to leverage their specialized skills and expertise through three tiers - Insight, Monitoring, and Management - to address security issues for a predictable monthly cost. This reduces the need for companies to invest in recruiting and training their own security staff.