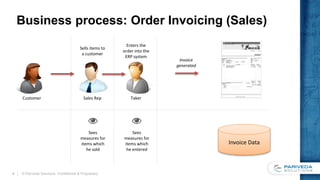
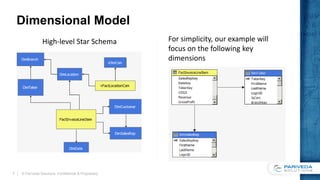
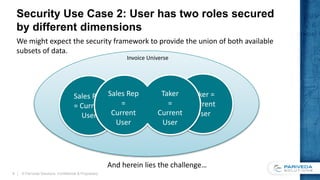
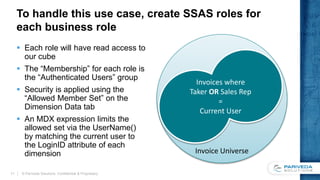
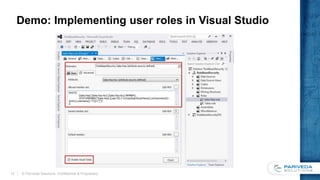
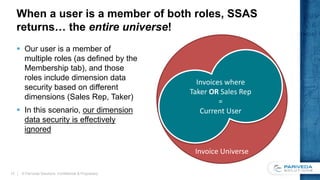
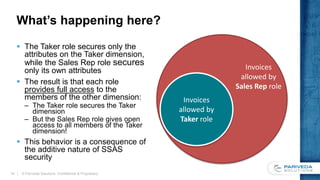
This document discusses implementing a data-driven security model in SQL Server Analysis Services (SSAS). It describes the problem of users having access to more data than intended when they belong to multiple roles secured by different dimensions. The solution is to use a single "data security" role and dimension that represents every fact-dimension combination, and dynamically filters data based on the user's login credentials. An alternative is a custom role assembly that can short-circuit the additive nature of multiple roles in SSAS.









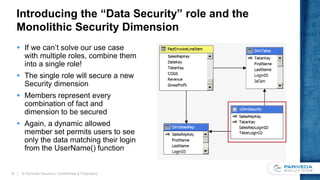
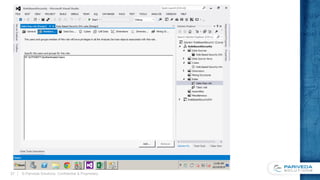
![Implementing the Security dimension in the data
warehouse or data source view
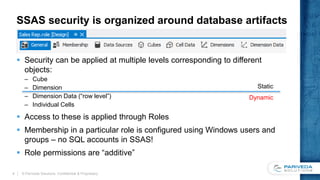
Implemented as a view or a
named query against the fact
and dimension tables
Selects all distinct combinations
of keys for the dimensions to be
secured
© Pariveda Solutions. Confidential & Proprietary.19
CREATE VIEW [dbo].[vDimSecurity]
WITH SCHEMABINDING
AS
SELECT DISTINCT
SalesRepKey = Rep.SalesRepKey,
SalesRepLoginID = UPPER(RTRIM(LTRIM(Rep.LoginID))),
TakerKey = Taker.TakerKey,
TakerLoginID = UPPER(RTRIM(LTRIM(Taker.LoginID))),
FROM
dbo.FactInvoiceLineItem InvLn
INNER JOIN
dbo.DimSalesRep Rep
ON InvLn.SalesRepKey = Rep.SalesRepKey
INNER JOIN
dbo.DimTaker Taker
ON InvLn.TakerKey = Taker.TakerKey
GO](https://image.slidesharecdn.com/ea6de16d-7c3c-4a32-8969-0c1b59fffb2b-150222153807-conversion-gate01/85/Data-Driven-Security-in-SSAS-19-320.jpg)

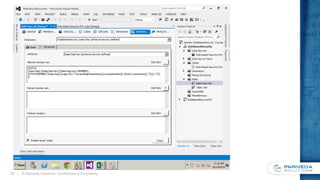
![Implementing the custom assembly
The assembly exposes a static
method, IsUserInRole
– Queries the roles of the current user
– Returns true when the specified role is
in the list
Used in the allowed member set
of the other dimensions for each
role
– For Sales Rep, we add attribute
security for the Taker role
– Uses IIF to return the empty set if the
user is in the Taker role
– If not, returns all members of the Taker
dimension
Becomes more complex as
roles are added to the cube
public static bool IsUserInRole(string roleName)
{
AdomdCommand cmd = new AdomdCommand(
@"SELECT ROLES FROM SYSTEMRESTRICTSCHEMA
($System.dbschema_catalogs, [CATALOG_NAME]
= '"
+ Context.CurrentDatabaseName
+ "')");
if (
(cmd.ExecuteScalar() as string)
.ToLower().Contains(roleName.ToLower())
)
return true;
else
return false;
}
© Pariveda Solutions. Confidential & Proprietary.22](https://image.slidesharecdn.com/ea6de16d-7c3c-4a32-8969-0c1b59fffb2b-150222153807-conversion-gate01/85/Data-Driven-Security-in-SSAS-22-320.jpg)