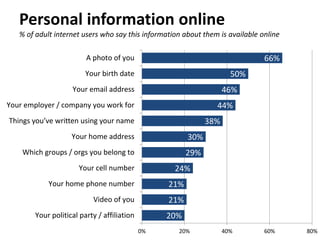
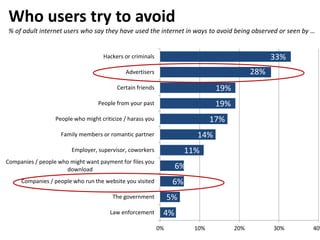
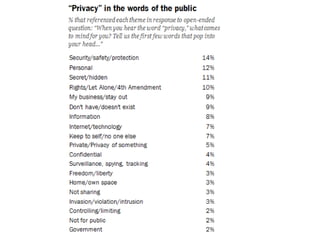
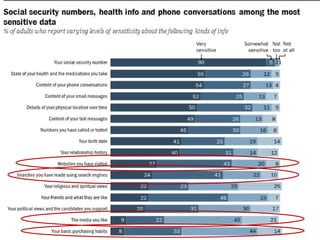
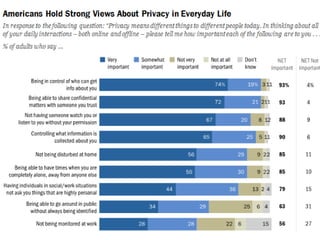
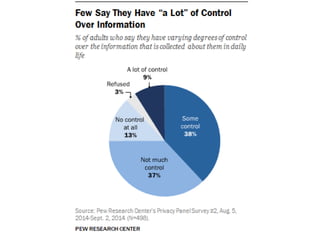
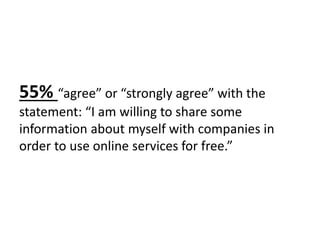
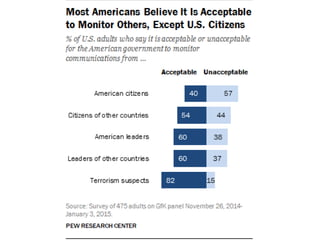
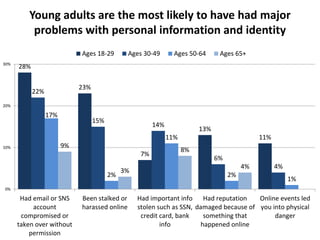
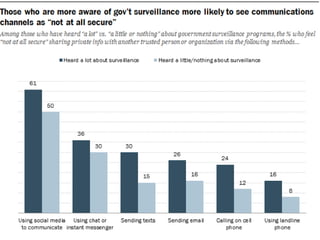
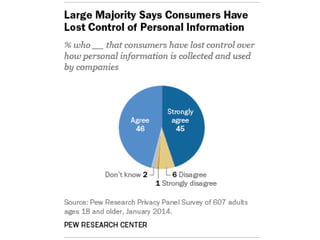
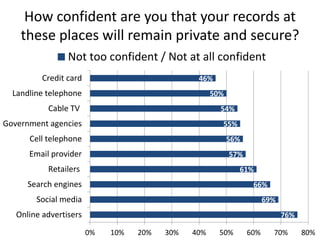
The document discusses privacy issues in the digital age, highlighting the complexity of personal information online and how perceptions of privacy have shifted, with individuals being 'public by default.' It reveals that younger adults are more proactive in managing their online privacy but also face significant risks, such as identity theft and harassment. Additionally, there is a widespread belief that current laws do not adequately protect online privacy, with many individuals seeking more government regulation and expressing a desire to improve their own privacy efforts.