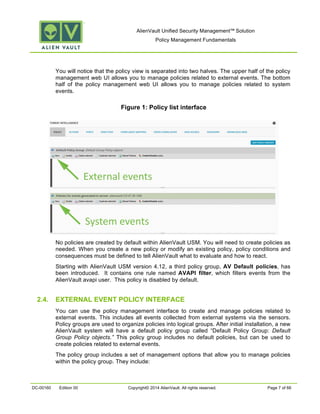
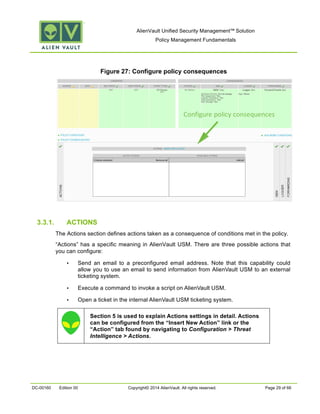
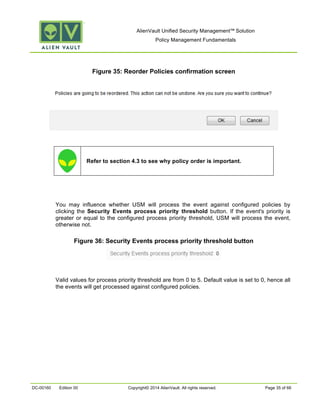
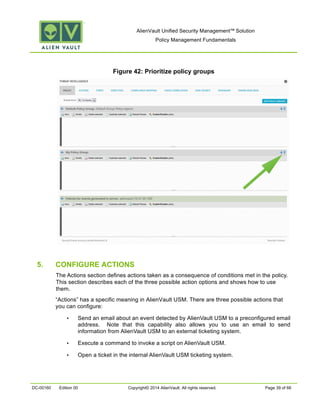
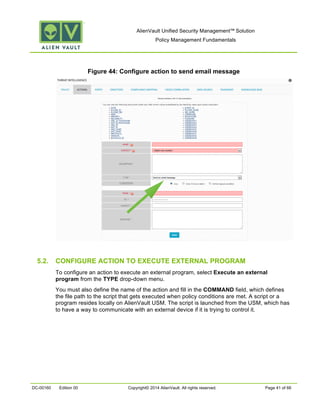
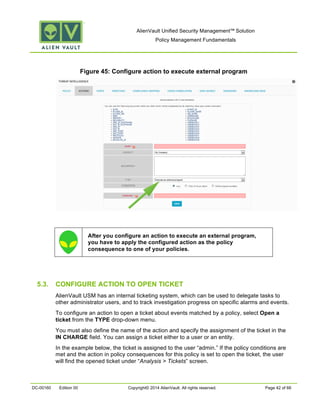
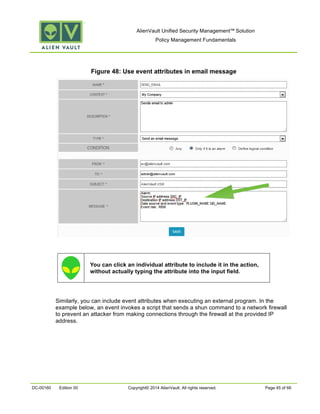
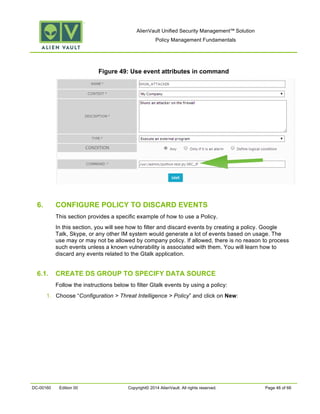
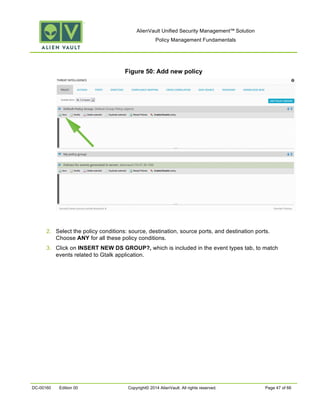
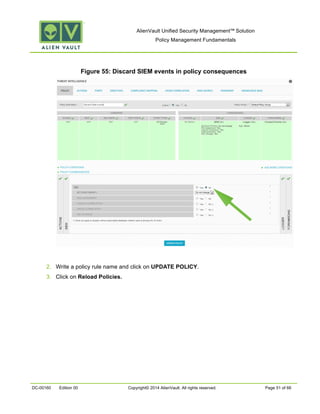
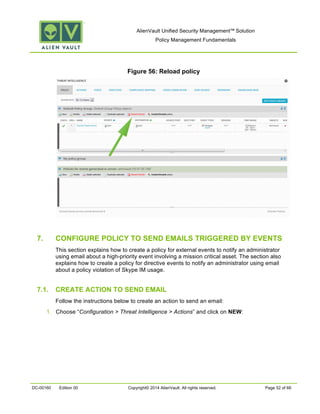
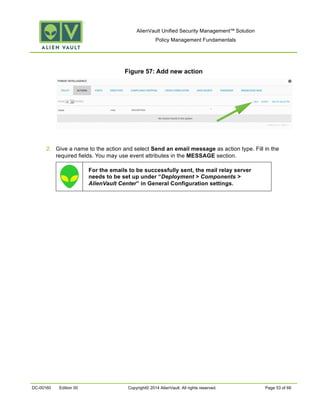
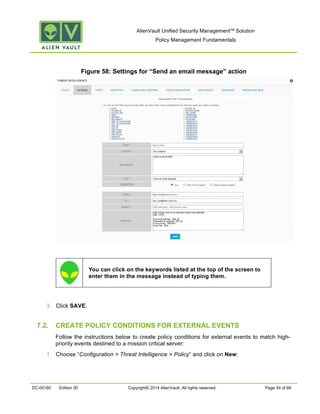
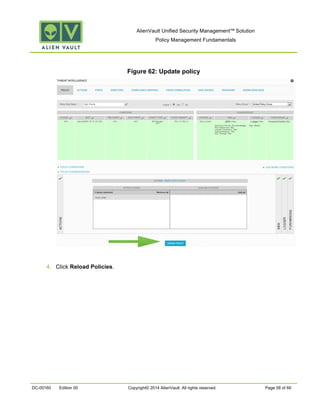
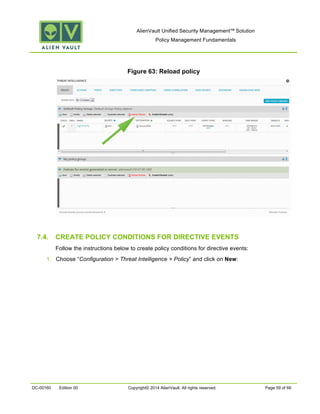
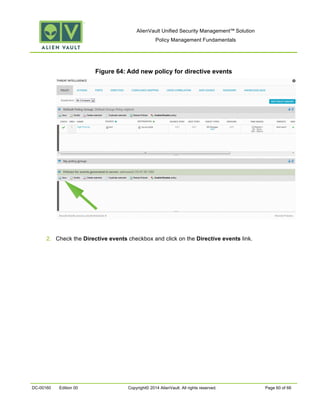
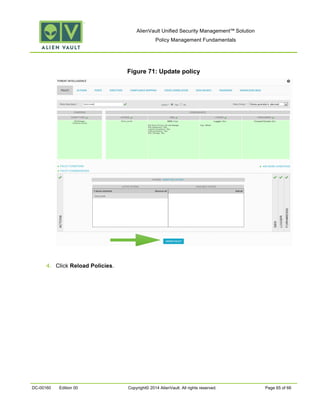
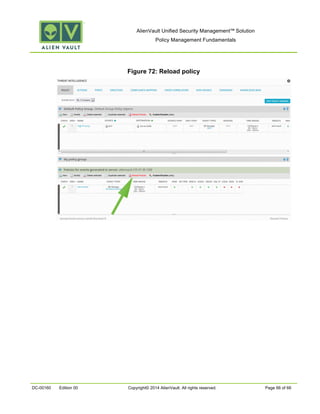
This document provides an overview of policies in AlienVault Unified Security Management. It discusses the different types of events, what policies are used for, how to create and manage policies for external and system events. It also describes the various policy conditions like source, destination, ports, taxonomy and priorities that can be used to filter events, and consequences like actions, forwarding and logging that are triggered when events match policy conditions. The document is intended to help users understand how to use policies to influence event processing and tuning their AlienVault deployment.