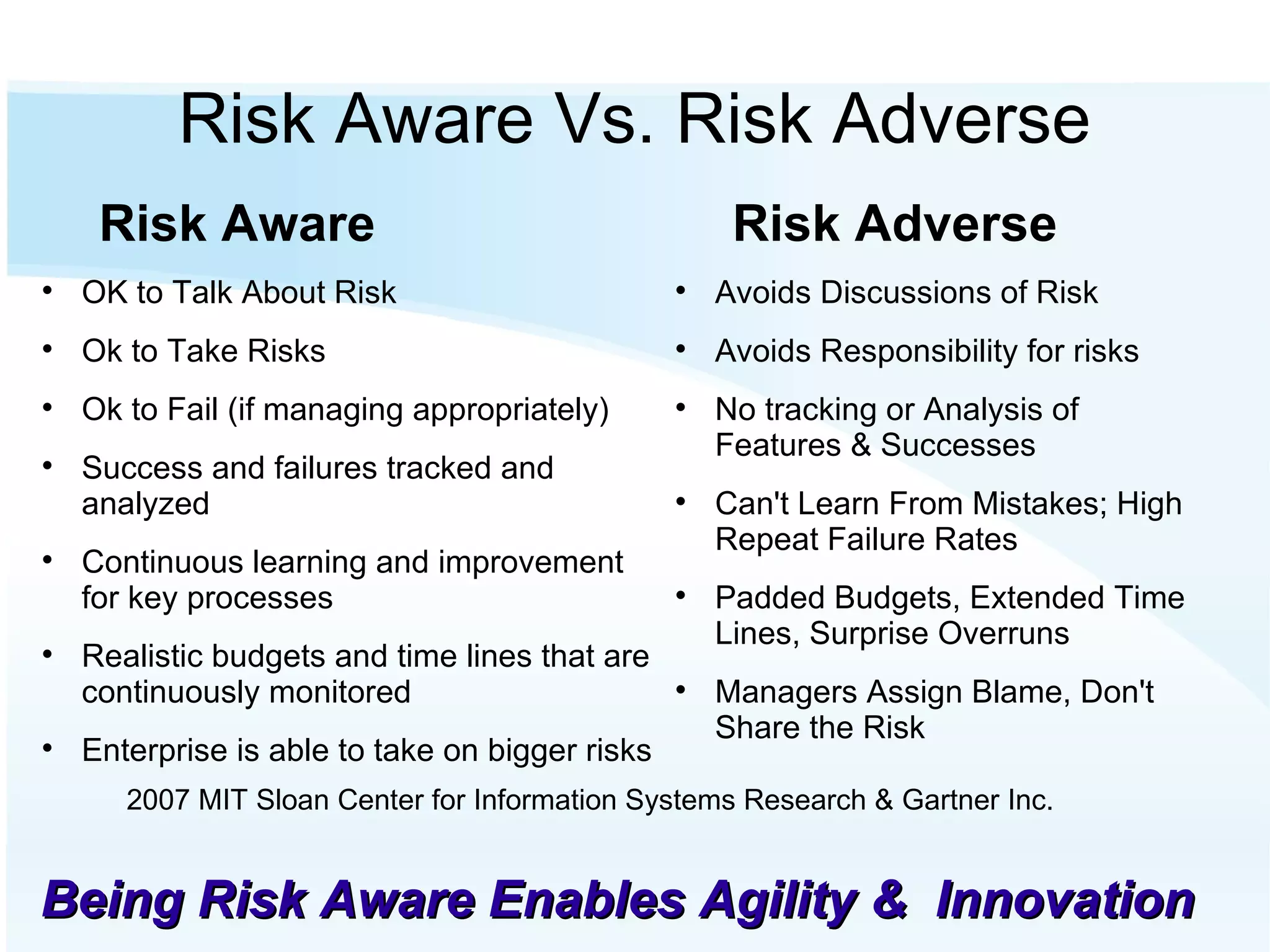
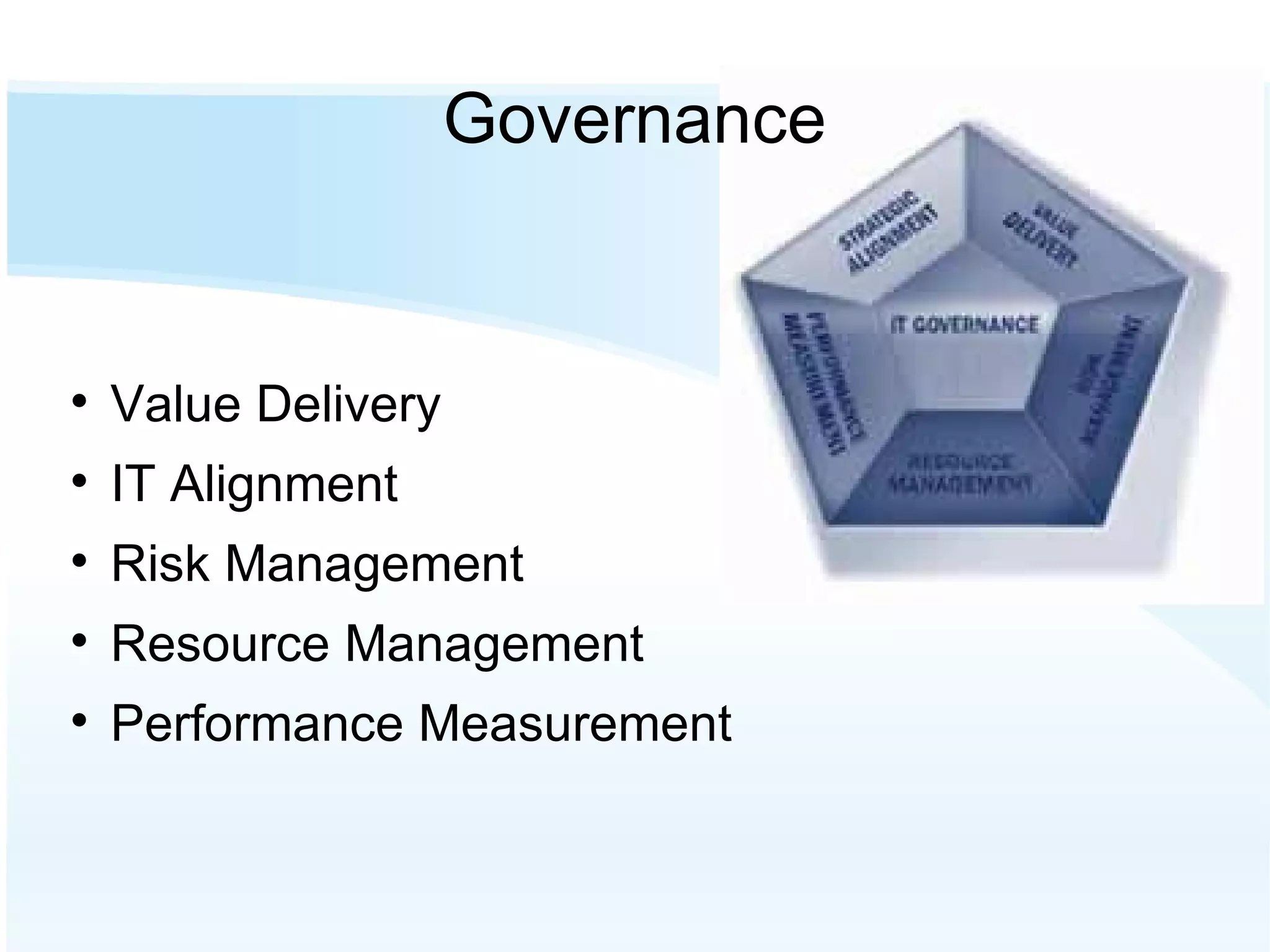
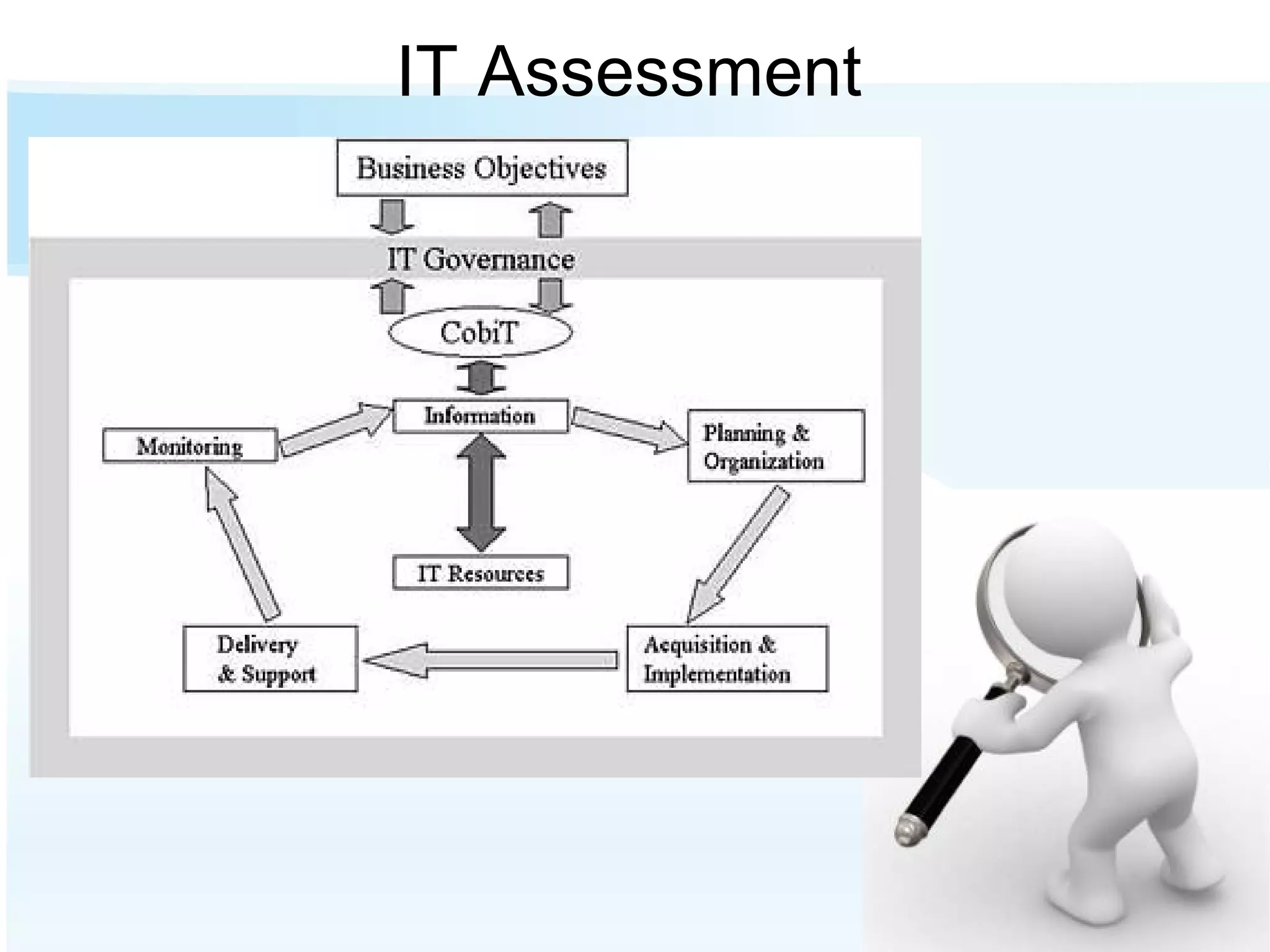
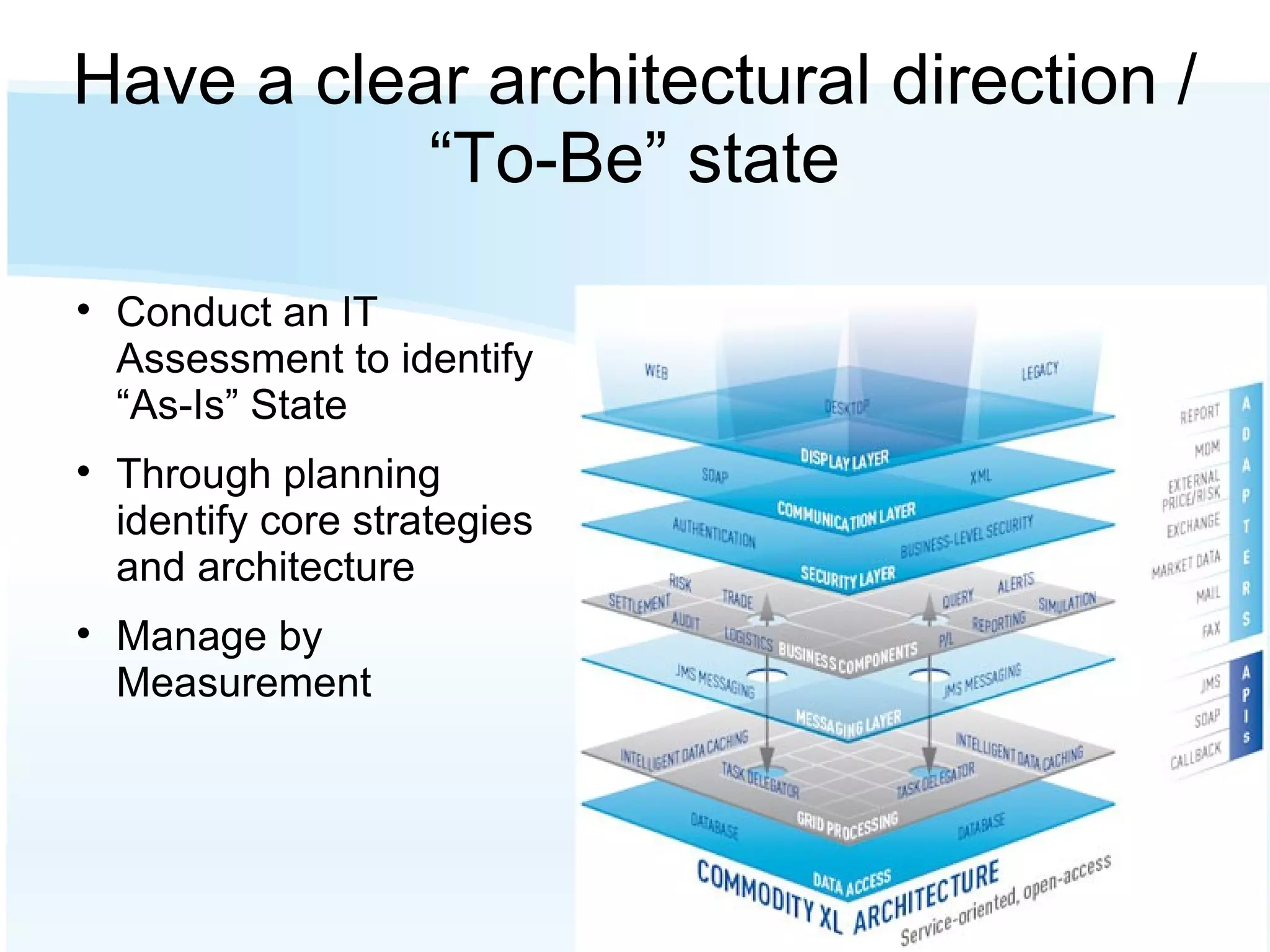
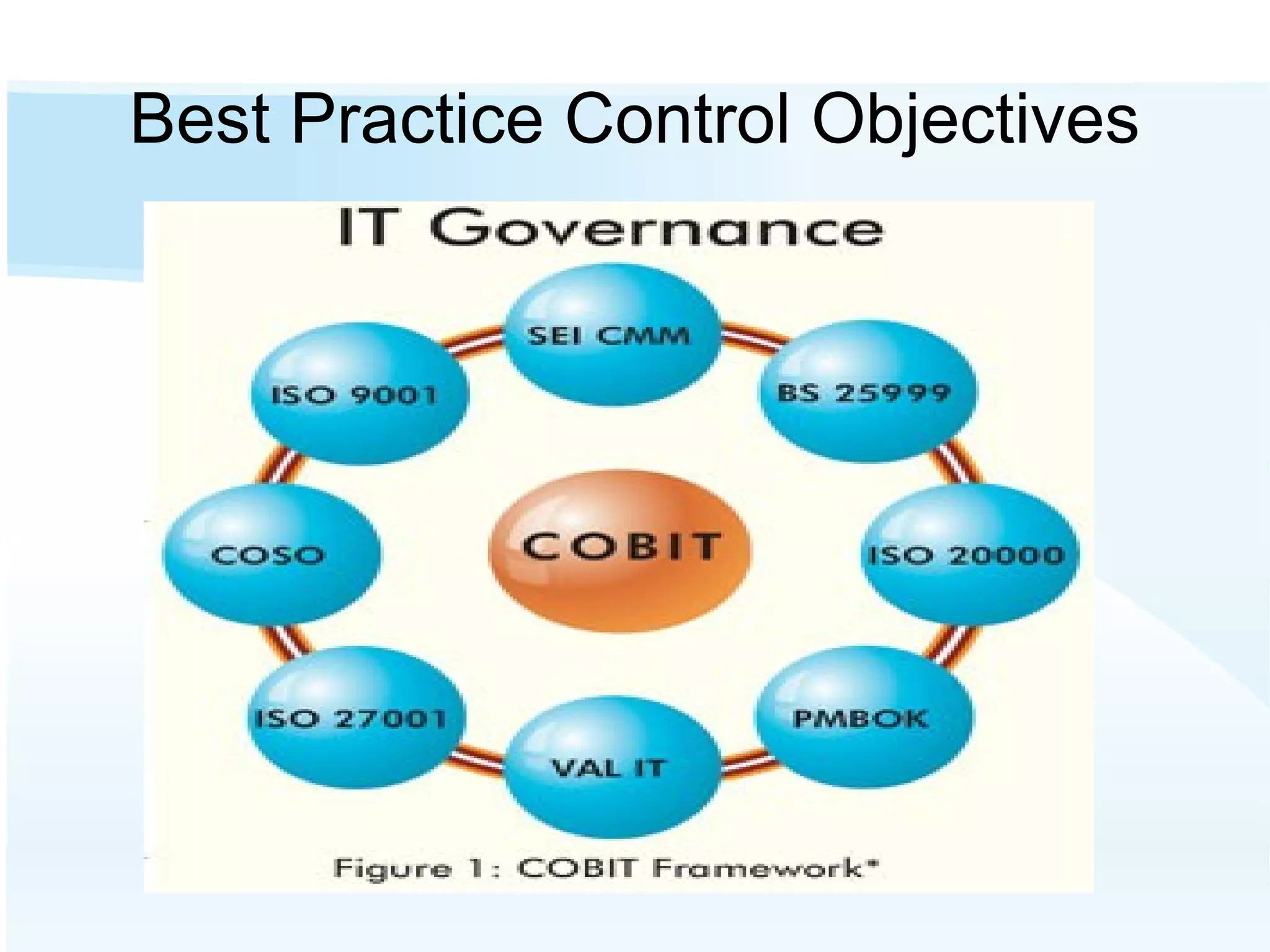
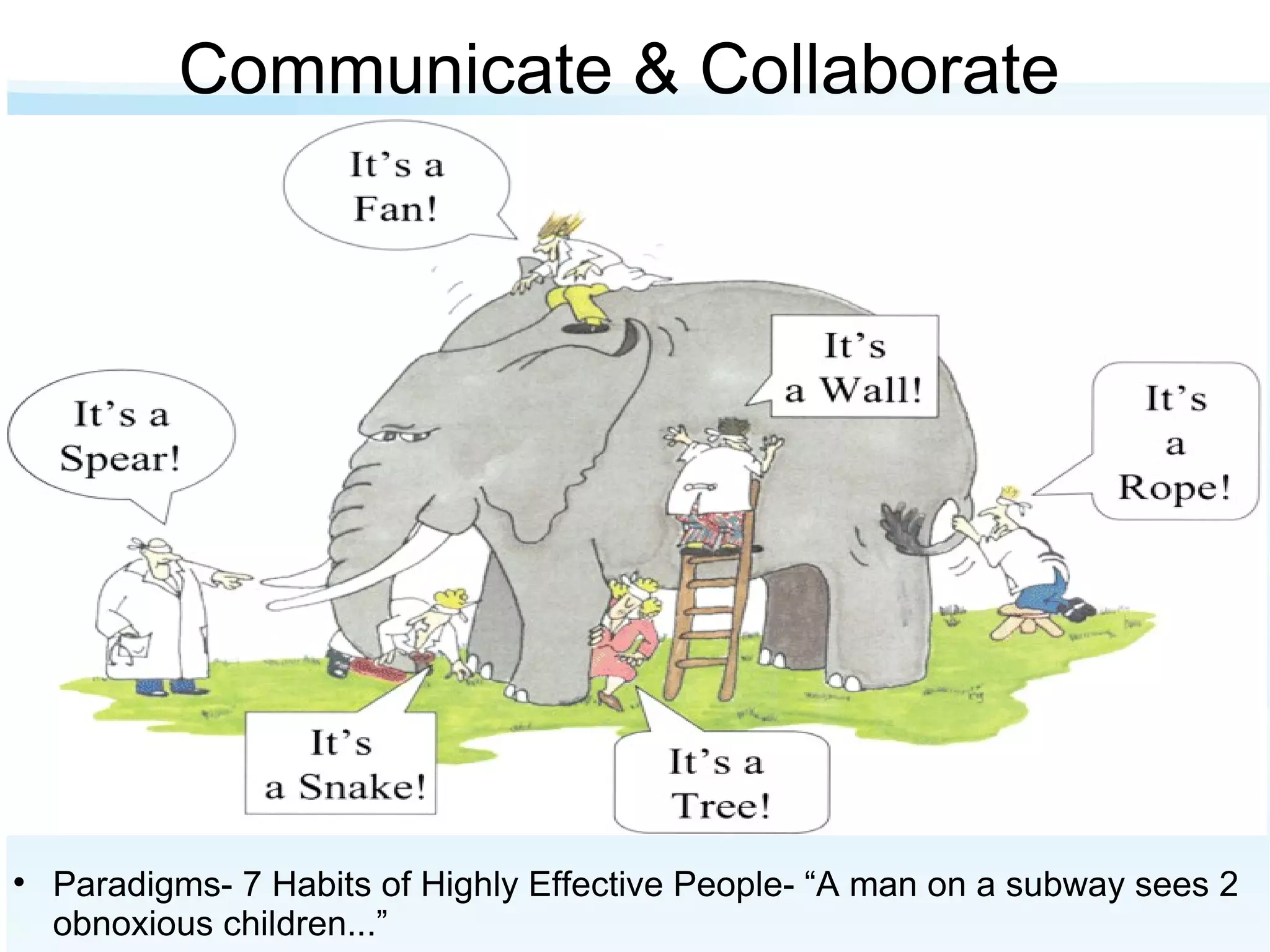
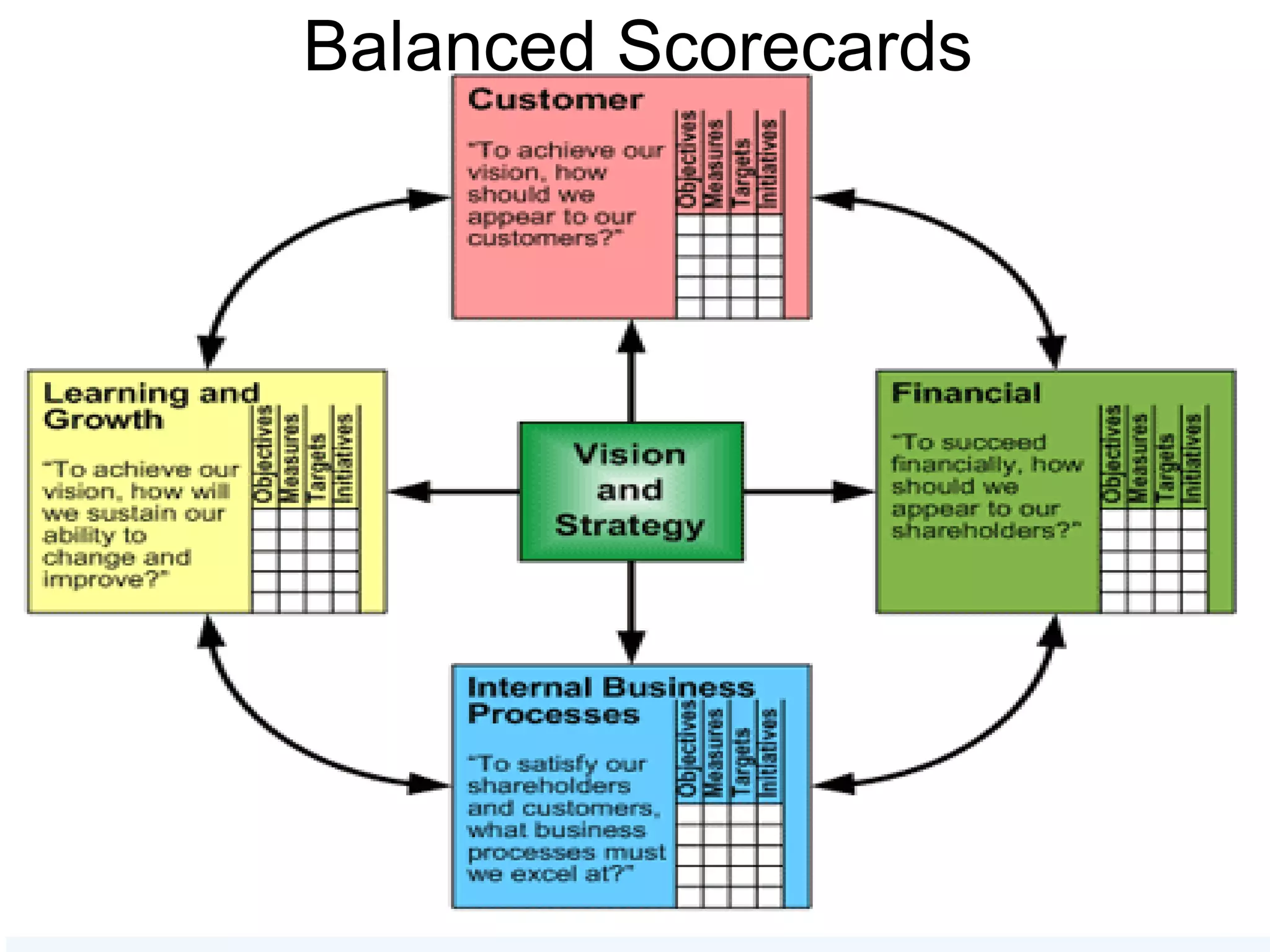
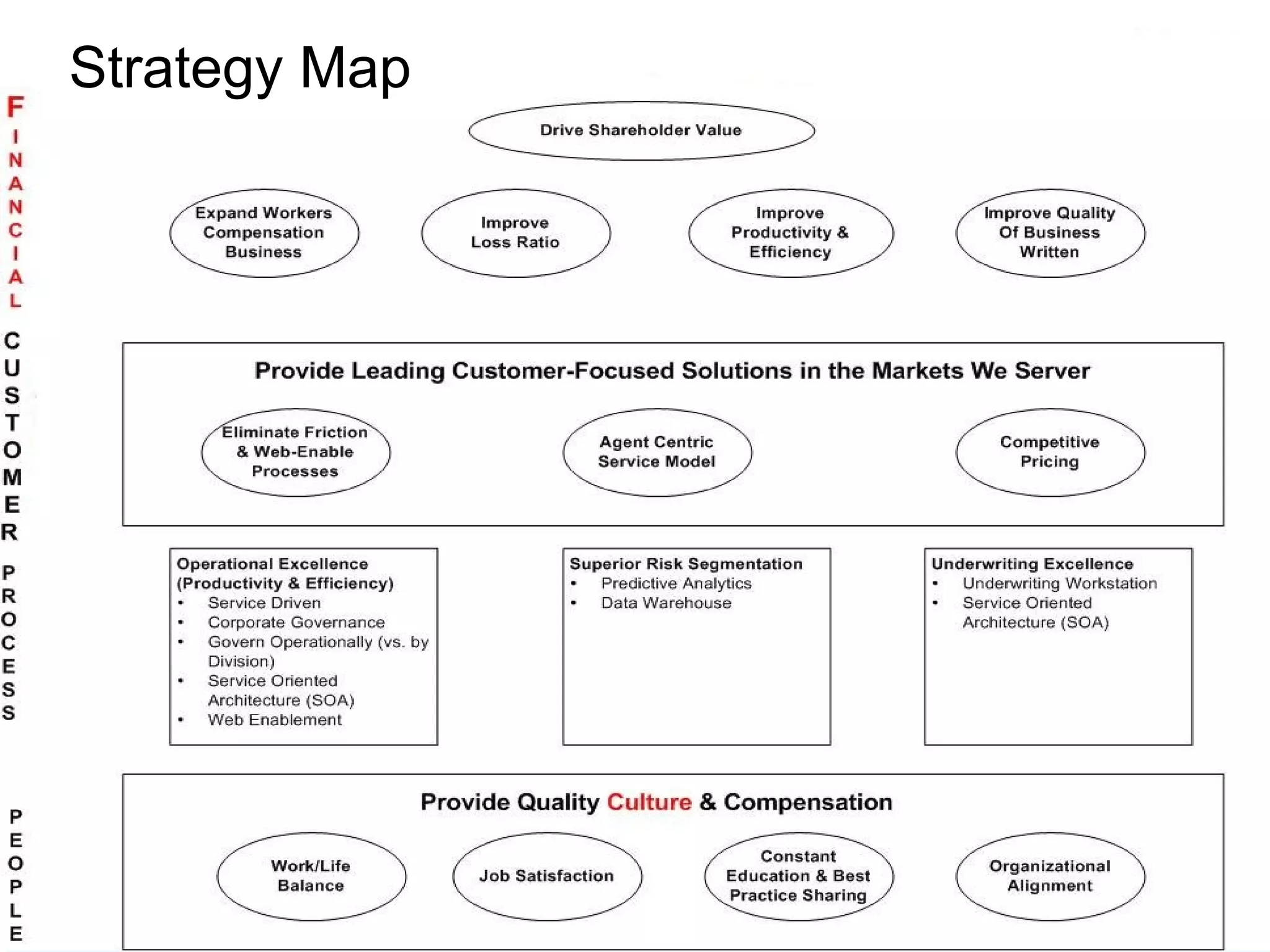
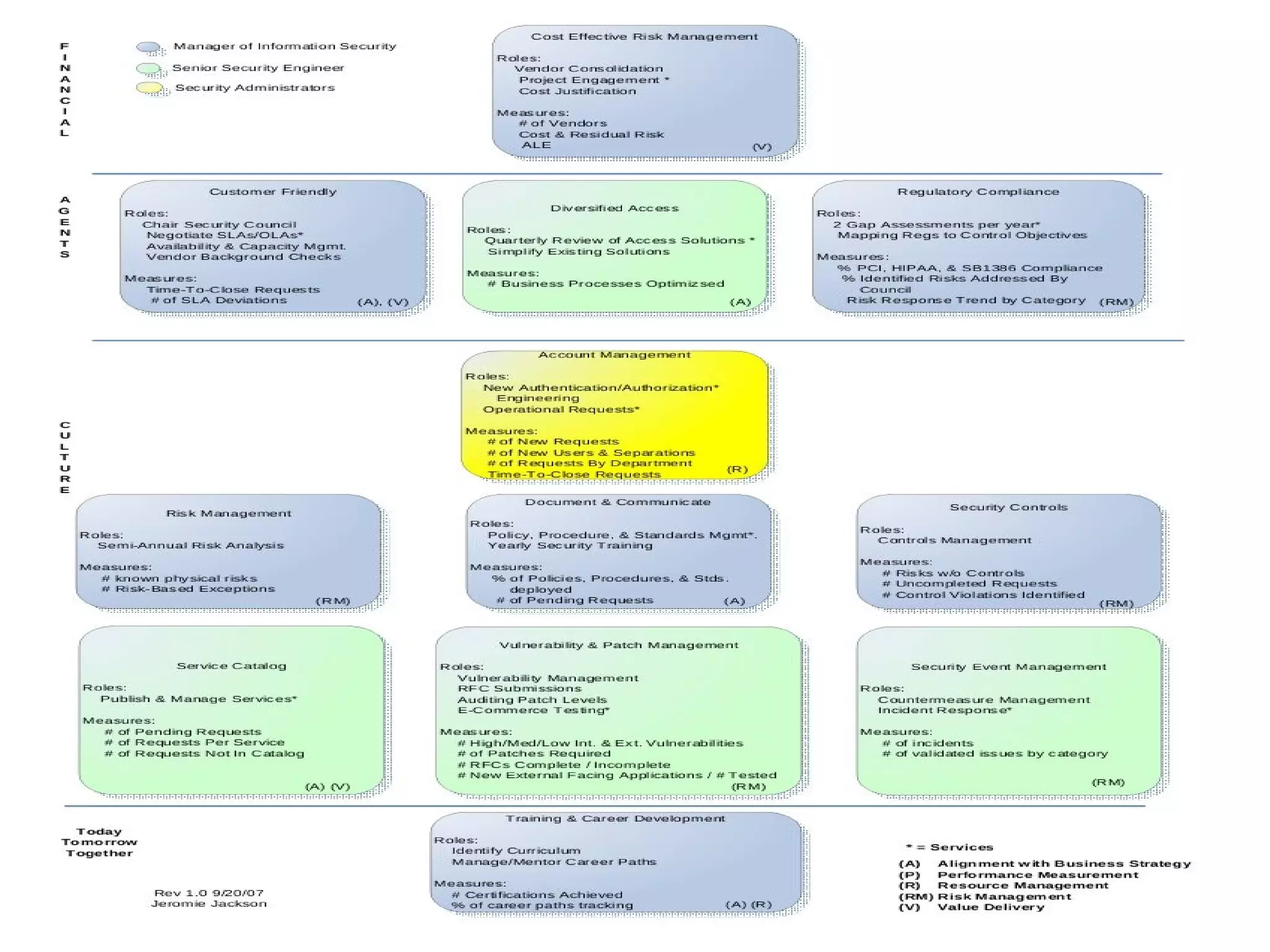
The document discusses the importance of risk management in business, highlighting that ignoring financial risks can lead to severe consequences, as evidenced by the 2008 financial crisis. It contrasts risk-aware and risk-adverse mindsets, advocating for a culture of continuous improvement, learning, and effective governance to mitigate IT risks. The text emphasizes the benefits of best practices in managing risks and promoting communication, collaboration, and strategic alignment in organizations.
![Ignorance is Risk Manage by Measurement Through the Use of a Control Framework Jeromie Jackson- CISM, CISSP Security Solutions Architect Technology Integration Group (TIG) [email_address] 858-205-3645- BB 619-368-7353-cell](https://image.slidesharecdn.com/ignoranceisrisk-123922031539-phpapp02/75/Ignorance-Is-Risk-1-2048.jpg)
















![Questions? 5 Jeromie Jackson- CISM, CISSP Security Solutions Architect Technology Integration Group (TIG) [email_address] 858-205-3645- BB 619-368-7353-cell](https://image.slidesharecdn.com/ignoranceisrisk-123922031539-phpapp02/75/Ignorance-Is-Risk-32-2048.jpg)