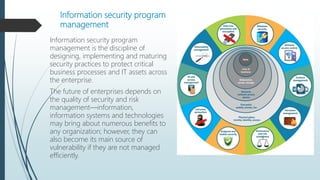
The document outlines the importance of implementing an effective information security management system to protect business processes and IT assets, emphasizing the need for C-suite support and alignment with business strategy. It discusses security risk management, risk appetite, gap analysis, prioritization of security projects, and the significance of security awareness within organizations. Successful security programs require executive backing, alignment with organizational goals, and ongoing measurement and improvement to ensure effective protection against evolving cyber threats.