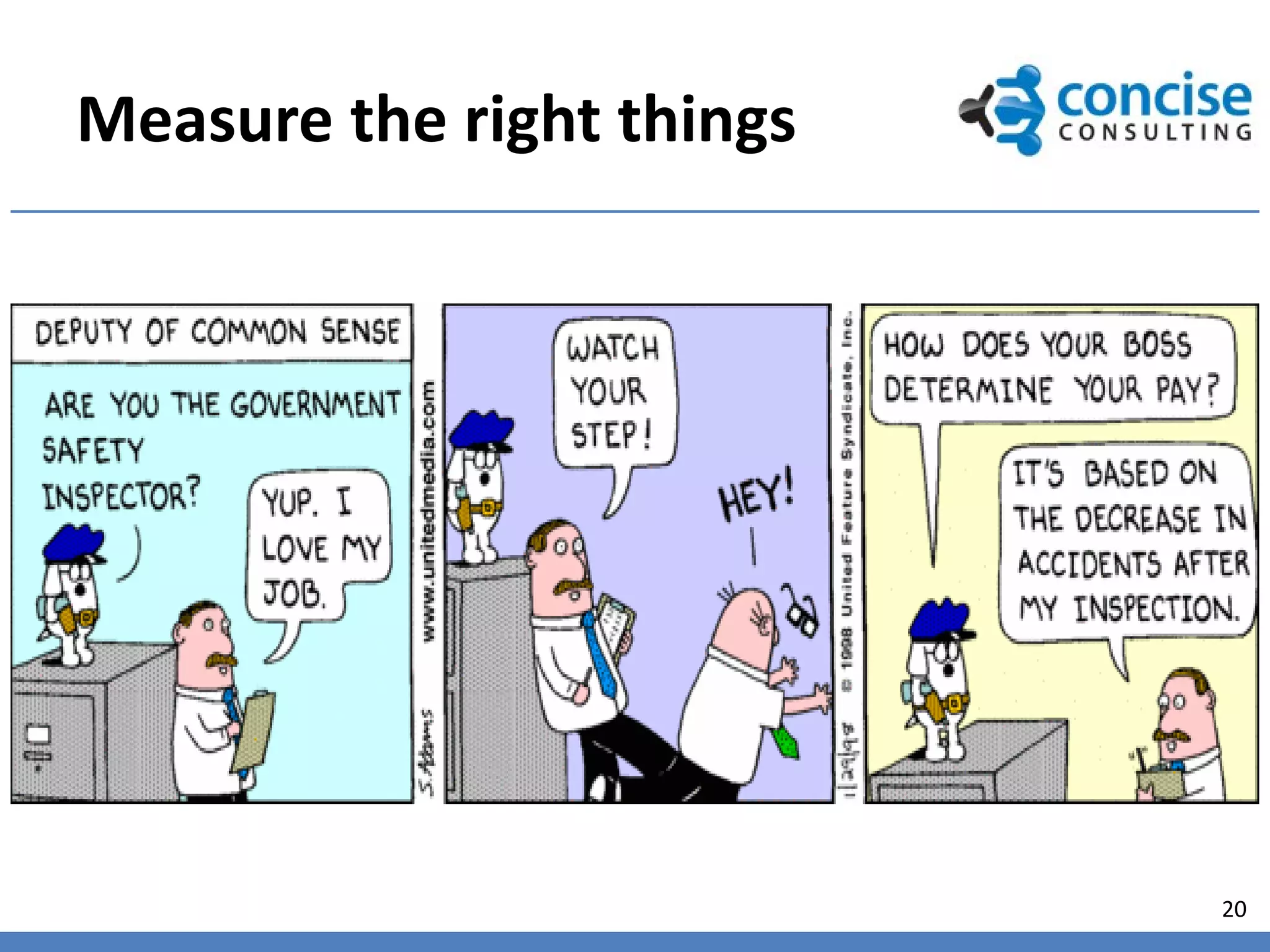
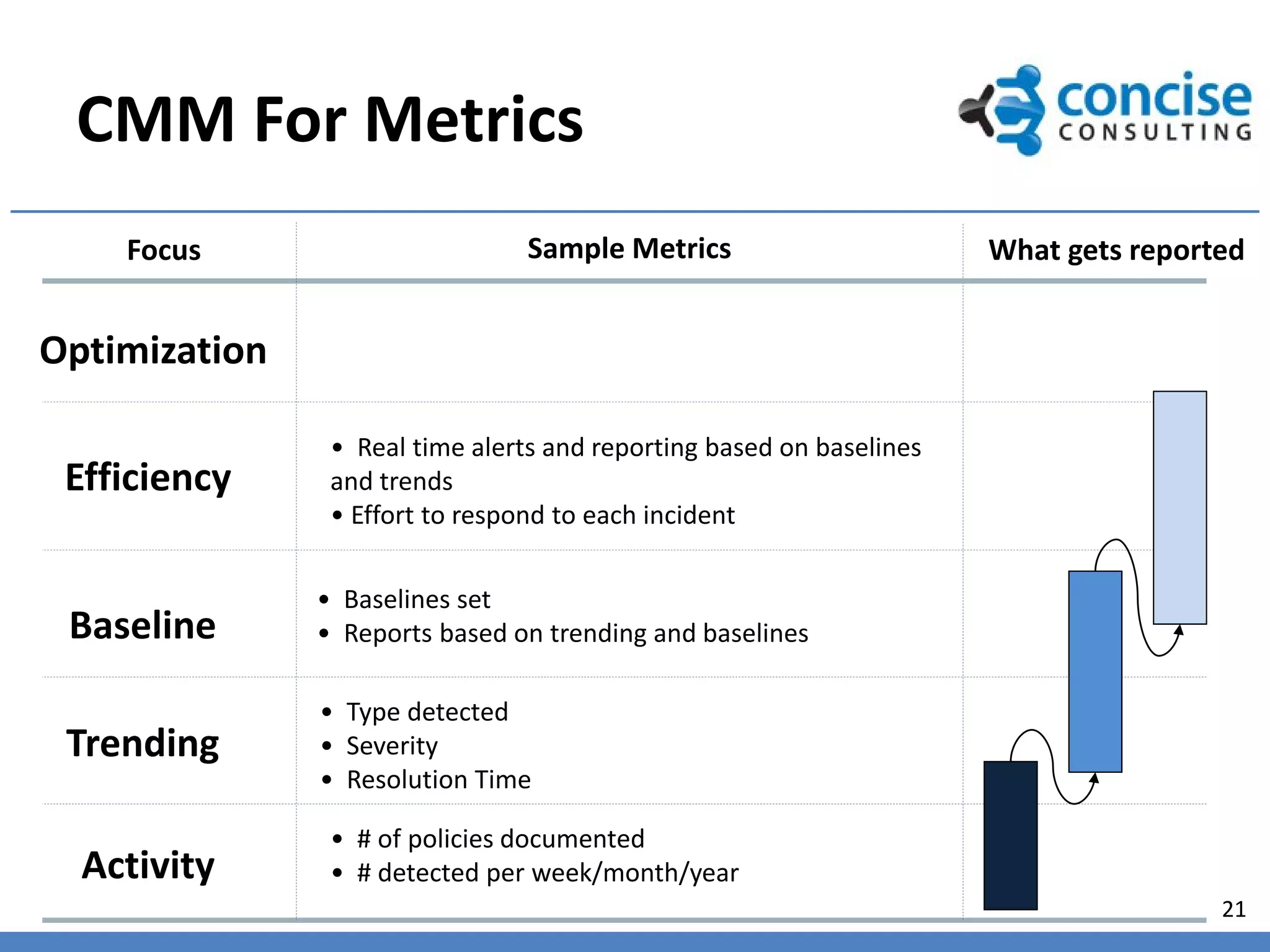
This document discusses taking a value-centric approach to governance, risk, and compliance. It argues that governance, risk, and compliance should be integrated, not separate activities, with governance directing the IT organization to achieve business objectives while managing risks and ensuring compliance. The document provides examples of governance frameworks and principles and emphasizes measuring the right things to demonstrate the value of IT investments.

















![But can be challenging to
achieve
Only 38 percent of executives/senior management can describe
their enterprise’s IT governance process. This is largely because
in most cases, IT governance has not been designed; it has just
developed ‘piecemeal’ in response to specific issues.
[IT Governance, Weil and Ross]
Only 40% of approved projects have realistic benefit
statements.
<10% of enterprises ensure that benefits are realized post-
project.
<5% of enterprises hold project stakeholders responsible for
achieving planned benefits. [META Group]
In many enterprises, less than 8 percent of the IT budget is
actually spent on initiatives that bring value to the enterprise.
[Butler Group]
24](https://image.slidesharecdn.com/governanceriskcompliance-110426135637-phpapp01/75/A-Value-Centric-Approach-to-Governance-Risk-Compliance-24-2048.jpg)


