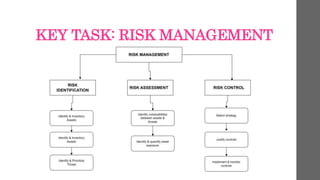
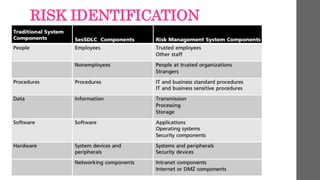
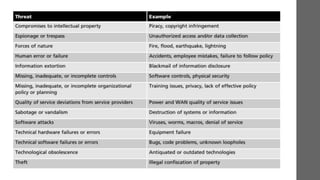
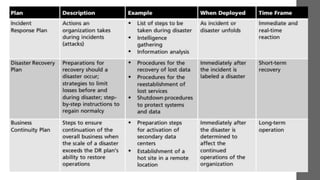
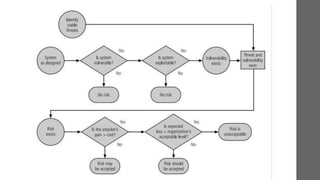
Risk management involves recognizing and minimizing risks to an organization’s information assets to protect against financial losses and operational disruptions. Key components include risk identification, assessment, and control, focused on vulnerability management and threat prioritization. An effective risk management plan aims to enhance compliance, customer trust, and overall organizational resilience.