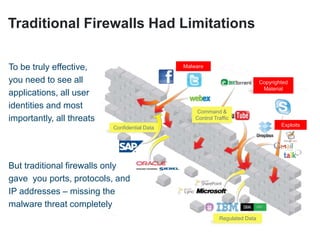
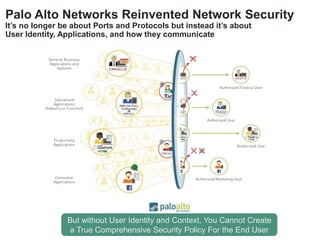
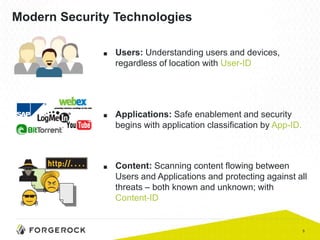
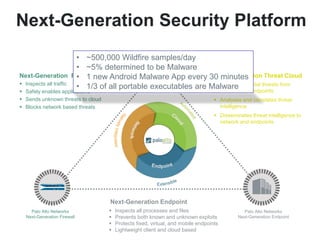
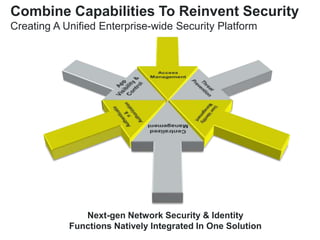
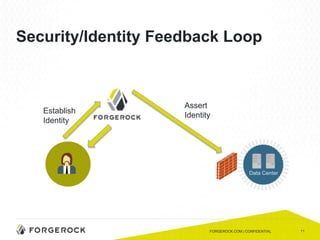
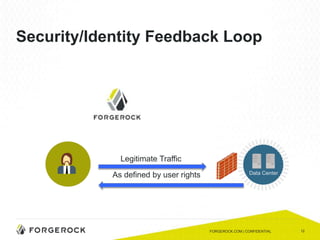
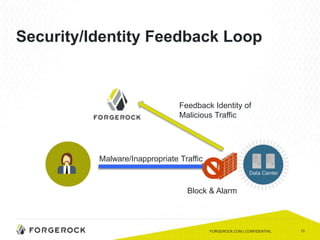
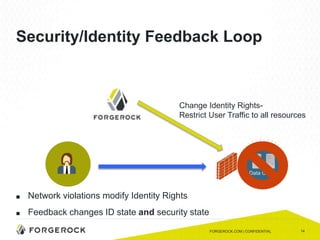
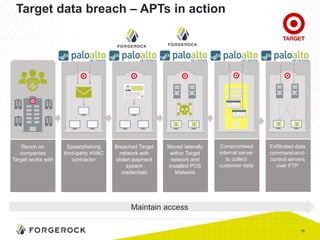
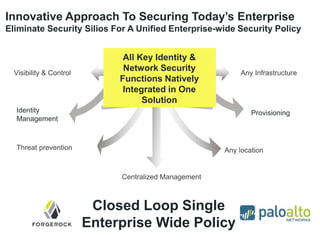
The document discusses the importance of a comprehensive enterprise security policy in light of increasing data breaches and security threats. It emphasizes the limitations of traditional firewalls and advocates for modern security technologies that integrate network security and identity management. The vision is to create a unified identity security platform that enhances safety through real-time automated responses to suspicious activities, improving overall organizational security.