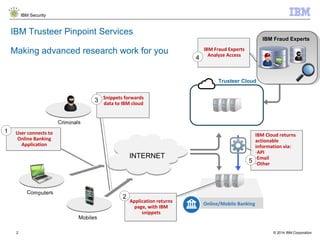
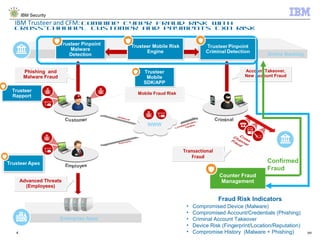
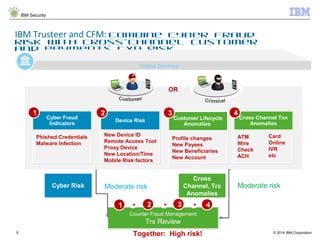
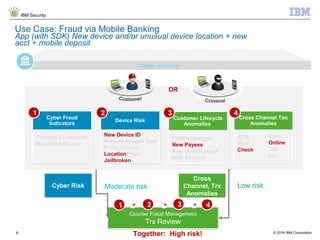
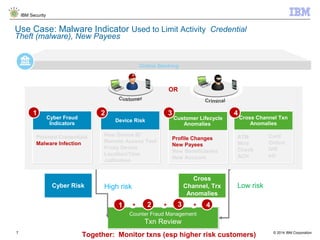
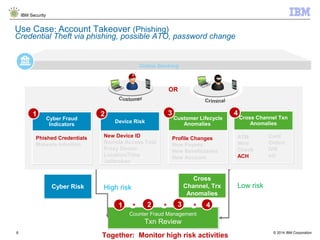
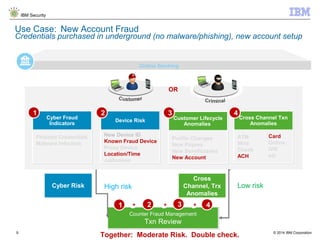
The document discusses IBM's Trusteer solutions for combating advanced threats in online and mobile banking, focusing on a comprehensive counter fraud management system. It highlights various fraud detection techniques, such as geospatial and predictive analytics, and emphasizes the need for integrating multiple data sources to effectively identify and mitigate risks. Additionally, it presents use cases demonstrating how to approach different types of fraud, including malware detection and account takeover scenarios.