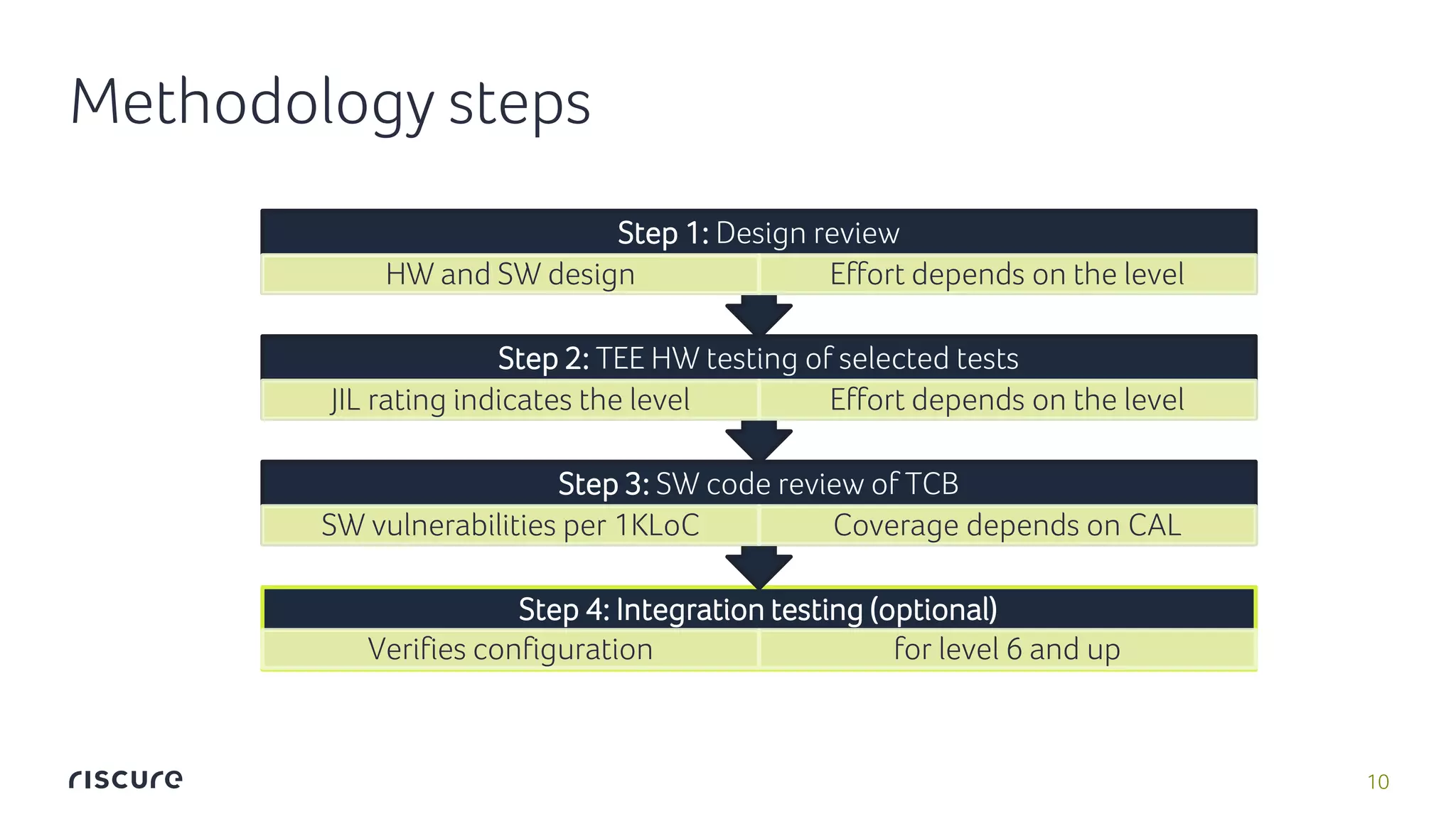
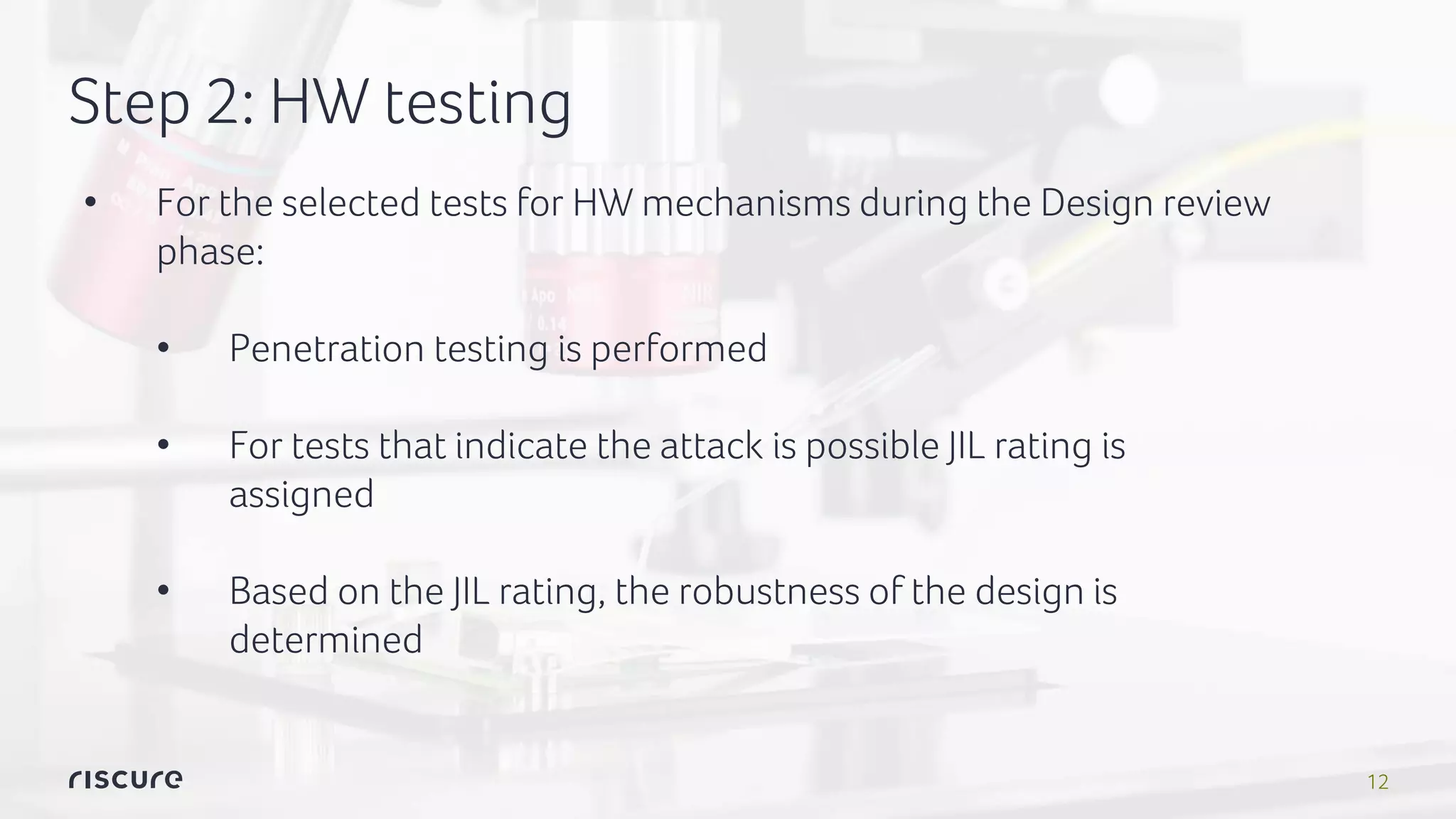
The document discusses Riscure assurance for premium content, focusing on Trusted Execution Environment (TEE) security and its mechanisms for protecting assets. It outlines challenges, issues with existing standards like Global Platform and Common Criteria, and proposes a methodology for component evaluations to enhance security assurance. The document also mentions compliance with MovieLabs specifications for enhanced content protection and the benefits of Riscure assurance screening.