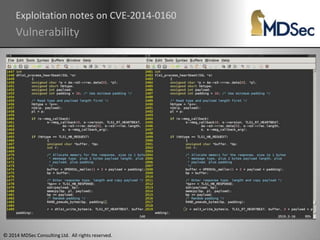
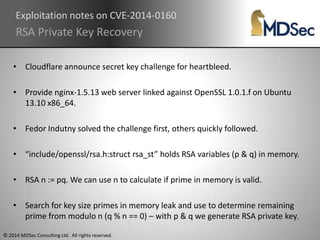
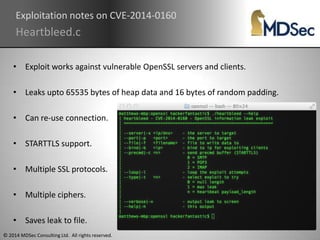
The document discusses the Heartbleed vulnerability (CVE-2014-0160) in OpenSSL, including its discovery and exploitation. It was introduced in 2011 during implementation of RFC-6520 and enabled by default in OpenSSL 1.0.1. Exploits were quickly developed to extract private keys and memory contents from vulnerable servers. The vulnerability remained an issue as affected systems were considered compromised. It highlighted the importance of enabling perfect forward secrecy and two-factor authentication to mitigate risks.