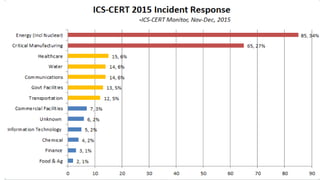
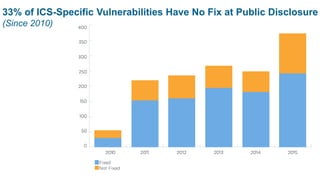
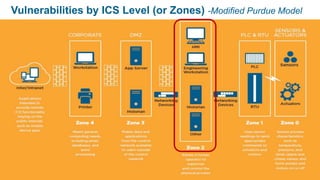
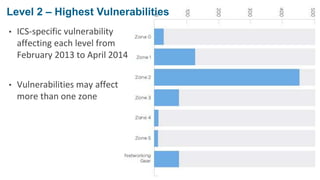
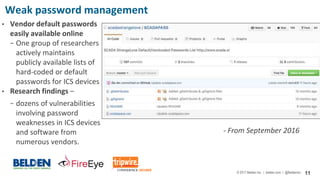
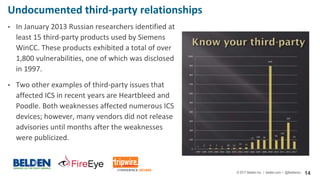
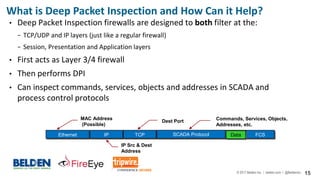
The document discusses cybersecurity risks in industrial control systems (ICS), identifying six major vulnerabilities termed the 'subversive six' including outdated hardware and weak password management. It emphasizes the need for improved security measures like deep packet inspection to mitigate these risks effectively. The presentation concludes with recommendations for assessing and enhancing ICS security, promoting holistic governance and infrastructure management.