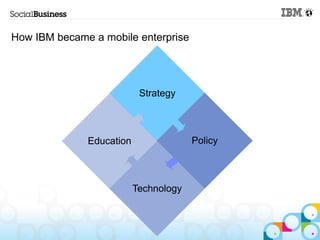
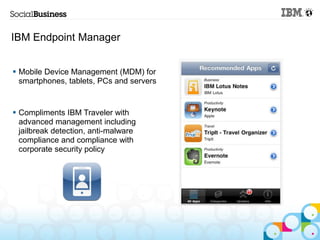
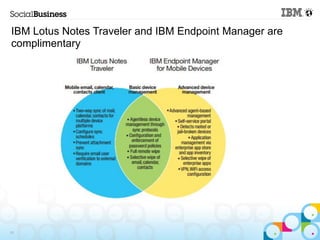
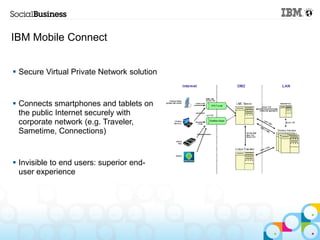
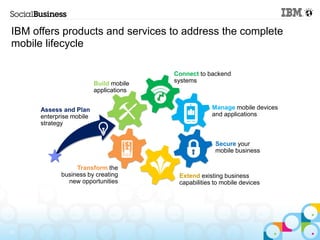
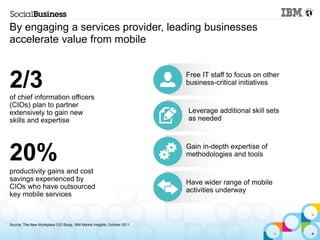
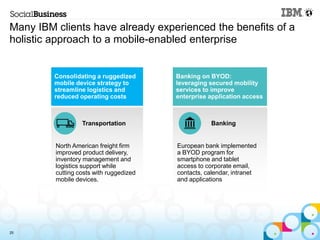
This document summarizes IBM's experience implementing a Bring Your Own Device (BYOD) program. It discusses how IBM developed a mobile strategy and policy, educated employees, and implemented technology like Lotus Notes Traveler and Endpoint Manager to manage devices while allowing flexibility. The next steps are to increase infrastructure for more devices, develop more apps, and enhance network access. Lessons included not trying to do too much at once and getting help from mobile experts.