BYOD & company owned comparison
•Download as PPTX, PDF•
1 like•393 views
Some thoughts on the ever recurring question BYOD vs Company Owned.
Report
Share
Report
Share
Recommended
Recommended
CompTIA exam study guide presentations by instructor Brian Ferrill, PACE-IT (Progressive, Accelerated Certifications for Employment in Information Technology)
"Funded by the Department of Labor, Employment and Training Administration, Grant #TC-23745-12-60-A-53"
Learn more about the PACE-IT Online program: www.edcc.edu/pace-it
PACE-IT, Security+ 4.2: Mobile Security Concepts and Technologies (part 2)

PACE-IT, Security+ 4.2: Mobile Security Concepts and Technologies (part 2)Pace IT at Edmonds Community College
More Related Content
Viewers also liked
Viewers also liked (12)
Google at London Tech Week- Connectivity at the Core

Google at London Tech Week- Connectivity at the Core
See How You Measure Up With MaaS360 Mobile Metrics

See How You Measure Up With MaaS360 Mobile Metrics
Similar to BYOD & company owned comparison
CompTIA exam study guide presentations by instructor Brian Ferrill, PACE-IT (Progressive, Accelerated Certifications for Employment in Information Technology)
"Funded by the Department of Labor, Employment and Training Administration, Grant #TC-23745-12-60-A-53"
Learn more about the PACE-IT Online program: www.edcc.edu/pace-it
PACE-IT, Security+ 4.2: Mobile Security Concepts and Technologies (part 2)

PACE-IT, Security+ 4.2: Mobile Security Concepts and Technologies (part 2)Pace IT at Edmonds Community College
Similar to BYOD & company owned comparison (20)
Bring Your Own Device is a disruptive phenomenon that is a significant IT trend

Bring Your Own Device is a disruptive phenomenon that is a significant IT trend
PACE-IT, Security+ 4.2: Mobile Security Concepts and Technologies (part 2)

PACE-IT, Security+ 4.2: Mobile Security Concepts and Technologies (part 2)
2014 - Mobile device management - mdm - case study - news agency

2014 - Mobile device management - mdm - case study - news agency
Three Keys to Building a Secure Mobile Infrastructure in Government Environments

Three Keys to Building a Secure Mobile Infrastructure in Government Environments
IRJET- Li-Fi Based Interactive Intelligent Shopping System with Auto Paym...

IRJET- Li-Fi Based Interactive Intelligent Shopping System with Auto Paym...
Mobile device management and BYOD – simple changes, big benefits

Mobile device management and BYOD – simple changes, big benefits
Securing Internal Applications with Cloudflare Access - April 2018

Securing Internal Applications with Cloudflare Access - April 2018
Securing Internal Applications with Cloudflare Access

Securing Internal Applications with Cloudflare Access
VMworld 2013: Android in the enterprise: Understand the challenges and how to...

VMworld 2013: Android in the enterprise: Understand the challenges and how to...
More from Peter Hewer
More from Peter Hewer (11)
3 data leak possibilities that are easy to overlook

3 data leak possibilities that are easy to overlook
Recently uploaded
PEMESANAN OBAT ASLI : +6287776558899
Cara Menggugurkan Kandungan usia 1 , 2 , bulan - obat penggugur janin - cara aborsi kandungan - obat penggugur kandungan 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 bulan - bagaimana cara menggugurkan kandungan - tips Cara aborsi kandungan - trik Cara menggugurkan janin - Cara aman bagi ibu menyusui menggugurkan kandungan - klinik apotek jual obat penggugur kandungan - jamu PENGGUGUR KANDUNGAN - WAJIB TAU CARA ABORSI JANIN - GUGURKAN KANDUNGAN AMAN TANPA KURET - CARA Menggugurkan Kandungan tanpa efek samping - rekomendasi dokter obat herbal penggugur kandungan - ABORSI JANIN - aborsi kandungan - jamu herbal Penggugur kandungan - cara Menggugurkan Kandungan yang cacat - tata cara Menggugurkan Kandungan - obat penggugur kandungan di apotik kimia Farma - obat telat datang bulan - obat penggugur kandungan tuntas - obat penggugur kandungan alami - klinik aborsi janin gugurkan kandungan - ©Cytotec ™misoprostol BPOM - OBAT PENGGUGUR KANDUNGAN ®CYTOTEC - aborsi janin dengan pil ©Cytotec - ®Cytotec misoprostol® BPOM 100% - penjual obat penggugur kandungan asli - klinik jual obat aborsi janin - obat penggugur kandungan di klinik k-24 || obat penggugur ™Cytotec di apotek umum || ®CYTOTEC ASLI || obat ©Cytotec yang asli 200mcg || obat penggugur ASLI || pil Cytotec© tablet || cara gugurin kandungan || jual ®Cytotec 200mcg || dokter gugurkan kandungan || cara menggugurkan kandungan dengan cepat selesai dalam 24 jam secara alami buah buahan || usia kandungan 1_2 3_4 5_6 7_8 bulan masih bisa di gugurkan || obat penggugur kandungan ®cytotec dan gastrul || cara gugurkan pembuahan janin secara alami dan cepat || gugurkan kandungan || gugurin janin || cara Menggugurkan janin di luar nikah || contoh aborsi janin yang benar || contoh obat penggugur kandungan asli || contoh cara Menggugurkan Kandungan yang benar || telat haid || obat telat haid || Cara Alami gugurkan kehamilan || obat telat menstruasi || cara Menggugurkan janin anak haram || cara aborsi menggugurkan janin yang tidak berkembang || gugurkan kandungan dengan obat ©Cytotec || obat penggugur kandungan ™Cytotec 100% original || HARGA obat penggugur kandungan || obat telat haid 1 bulan || obat telat menstruasi 1-2 3-4 5-6 7-8 BULAN || obat telat datang bulan || cara Menggugurkan janin 1 bulan || cara Menggugurkan Kandungan yang masih 2 bulan || cara Menggugurkan Kandungan yang masih hitungan Minggu || cara Menggugurkan Kandungan yang masih usia 3 bulan || cara Menggugurkan usia kandungan 4 bulan || cara Menggugurkan janin usia 5 bulan || cara Menggugurkan kehamilan 6 Bulan
________&&&_________&&&_____________&&&_________&&&&____________
Cara Menggugurkan Kandungan Usia Janin 1 | 7 | 8 Bulan Dengan Cepat Dalam Hitungan Jam Secara Alami, Kami Siap Meneriman Pesanan Ke Seluruh Indonesia, Melputi: Ambon, Banda Aceh, Bandung, Banjarbaru, Batam, Bau-Bau, Bengkulu, Binjai, Blitar, Bontang, Cilegon, Cirebon, Depok, Gorontalo, Jakarta, Jayapura, Kendari, Kota Mobagu, Kupang, LhokseumaweObat Penggugur Kandungan Di Apotik Kimia Farma (087776558899)

Obat Penggugur Kandungan Di Apotik Kimia Farma (087776558899)Cara Menggugurkan Kandungan 087776558899
Recently uploaded (6)
Leading Mobile App Development Companies in India (2).pdf

Leading Mobile App Development Companies in India (2).pdf
Obat Penggugur Kandungan Di Apotik Kimia Farma (087776558899)

Obat Penggugur Kandungan Di Apotik Kimia Farma (087776558899)
Powerful Love Spells in Arkansas, AR (310) 882-6330 Bring Back Lost Lover

Powerful Love Spells in Arkansas, AR (310) 882-6330 Bring Back Lost Lover
9999266834 Call Girls In Noida Sector 52 (Delhi) Call Girl Service

9999266834 Call Girls In Noida Sector 52 (Delhi) Call Girl Service
BDSM⚡Call Girls in Sector 71 Noida Escorts >༒8448380779 Escort Service

BDSM⚡Call Girls in Sector 71 Noida Escorts >༒8448380779 Escort Service
FULL ENJOY - 9999218229 Call Girls in {Mahipalpur}| Delhi NCR

FULL ENJOY - 9999218229 Call Girls in {Mahipalpur}| Delhi NCR
BYOD & company owned comparison
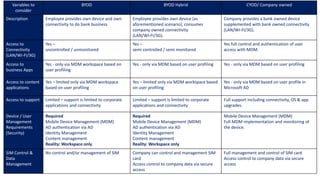
- 1. Variables to consider BYOD BYOD Hybrid CYOD/ Company owned Description Employee provides own device and own connectivity to do bank business Employee provides own device (as aforementioned scenario), consumes company owned connectivity (LAN/WI-FI/3G). Company provides a bank owned device supplemented with bank owned connectivity (LAN/WI-FI/3G). Access to Connectivity (LAN/Wi-Fi/3G) Yes – uncontrolled / unmonitored Yes – semi controlled / semi monitored Yes full control and authentication of user access with MDM. Access to business Apps Yes - only via MDM workspace based on user profiling Yes - only via MDM based on user profiling Yes - only via MDM based on user profiling Access to content applications Yes – limited only via MDM workspace based on user profiling Yes – limited only via MDM workspace based on user profiling Yes - only via MDM based on user profile in Microsoft AD Access to support Limited – support is limited to corporate applications and connectivity Limited – support is limited to corporate applications and connectivity Full support including connectivity, OS & app upgrades. Device / User Management Requirements (Security) Required Mobile Device Management (MDM) AD authentication via AD Identity Management Content management Reality: Workspace only Required Mobile Device Management (MDM) AD authentication via AD Identity Management Content management Reality: Workspace only Mobile Device Management (MDM) Full MDM implementation and monitoring of the device. SIM Control & Data Management No control and/or management of SIM Company can control and management SIM card Access control to company data via secure access Full management and control of SIM card Access control to company data via secure access
- 2. Variables to consider BYOD BYOD Hybrid CYOD/ Company owned Cost Management None – Uses can claim unlimited data costs for business use. Users can have access to company Wi-FI User is not refunded for monthly contract costs (incl. device). Yes – Connectivity costs controlled via company Wi-Fi and a secure 3G APN. Excessive data usage monitored and managed. User is not refunded for monthly contract costs (incl. device). Yes – Monthly contract costs include: Connectivity costs controlled via bank Wi-Fi and a secure 3G APN. Excessive data usage monitored and managed. User acceptance and satisfaction Low - Users reluctant to use own devices due to upfront costs. Limited to claim categories (business only) High - Users know their devices and don’t have to adjust to another Medium - Users reluctant to use own devices due to upfront hardware costs; happy with sponsored connectivity. High - Users know their devices and don’t have to adjust to another; happy with sponsored connectivity Medium – Some users may not like the company sponsored device High - Most user satisfaction because they are not liable for contracts and costs Support and loan stock Loss of device results in loss of productivity. No loan stock available. Loss of device results in loss of productivity. No loan stock available. Loss of device results in loss of productivity until loan unit is made available via internal process. Risks User is responsible for securing device (OS & apps) Access to network without proper security Claims are not business defined / justified Users will not load any security protocols on own device User resists encryption and remote wipe policy OS upgrades and corporate apps aren’t in sync User expectations for support on personal devices User is responsible for securing device (OS & apps) Access to network without security Users will not load any security protocols on own device User resists encryption and remote wipe policy OS upgrades and corporate apps aren’t in sync User expectations for support on personal devices None