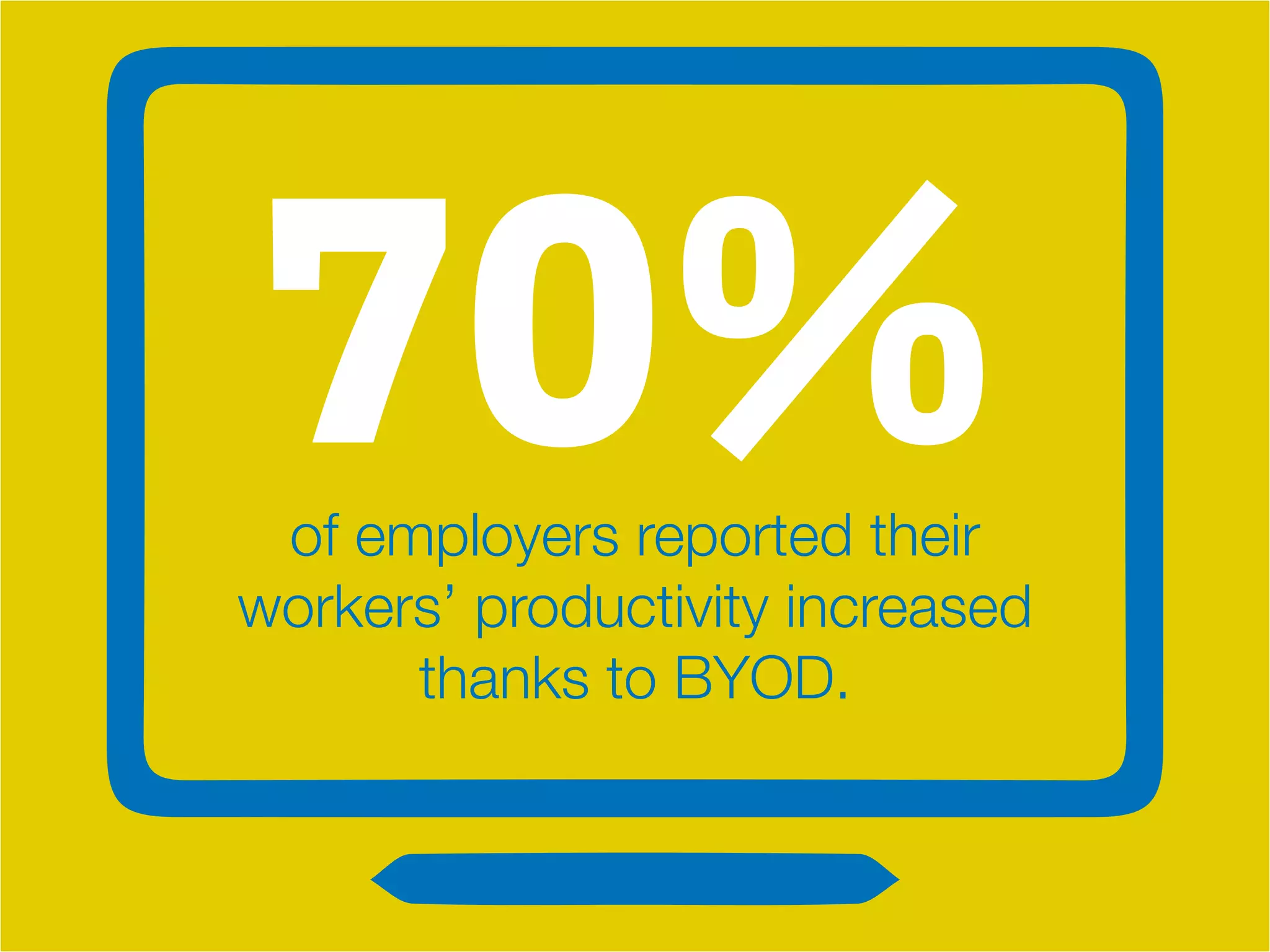
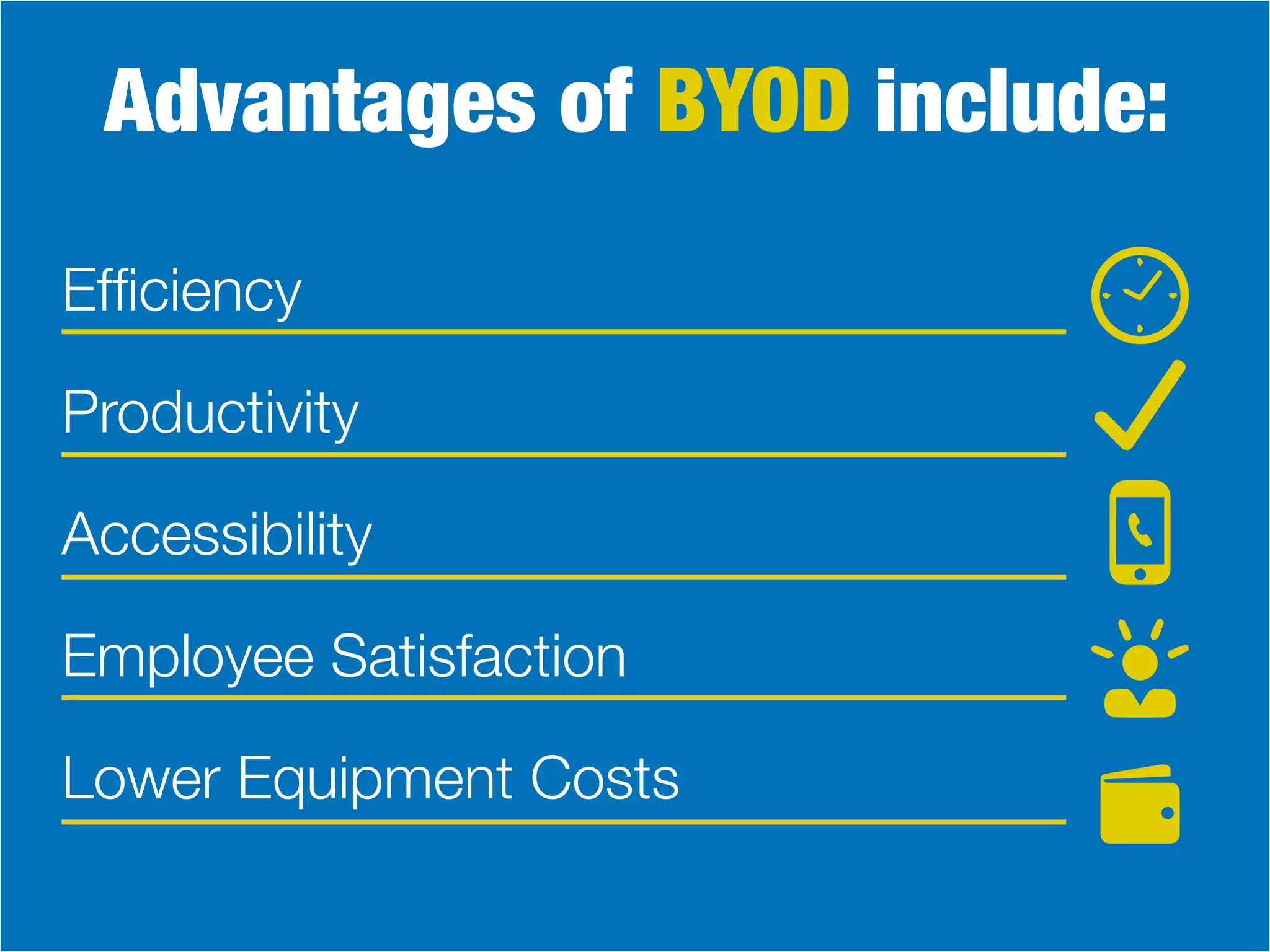
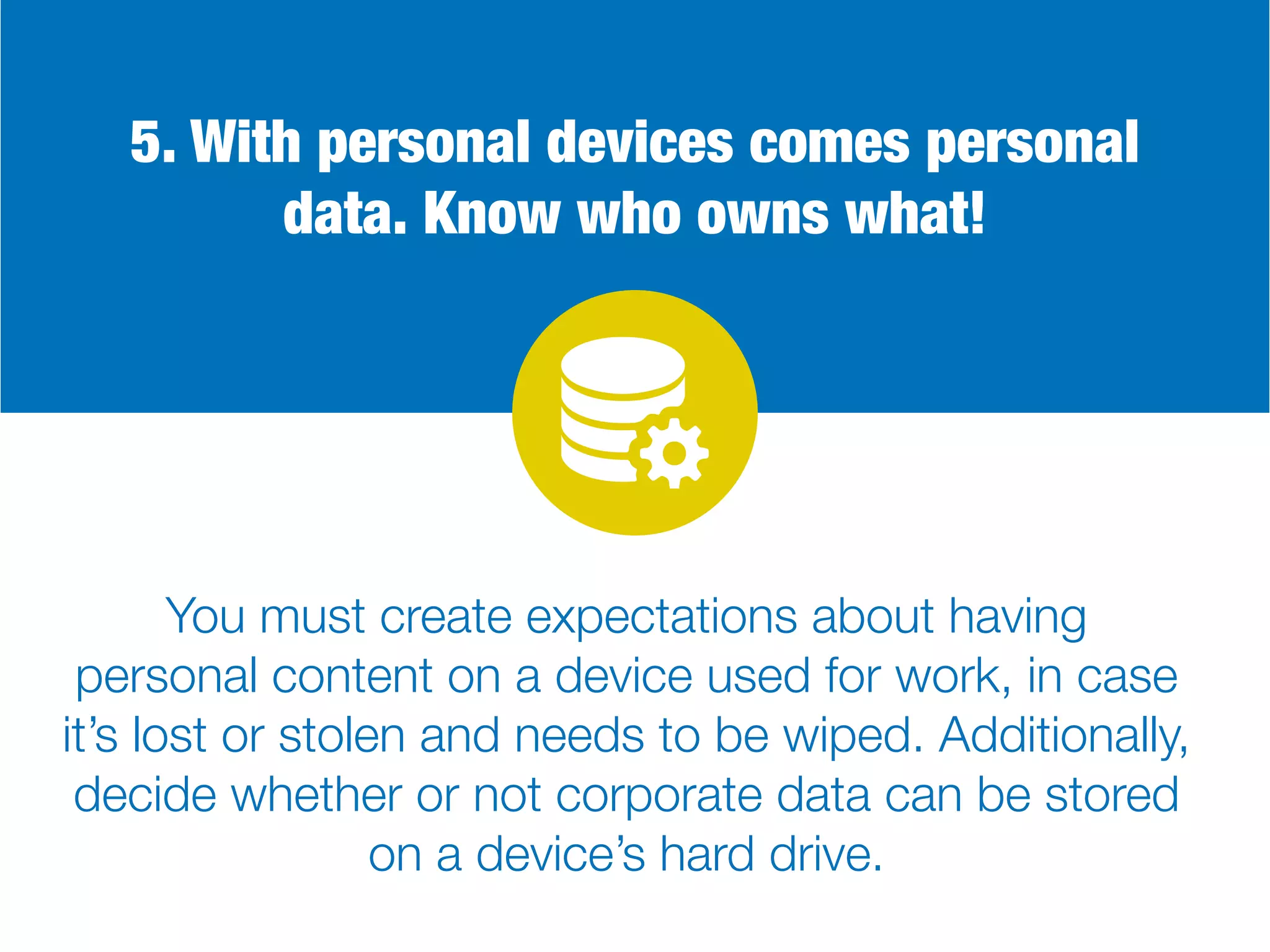
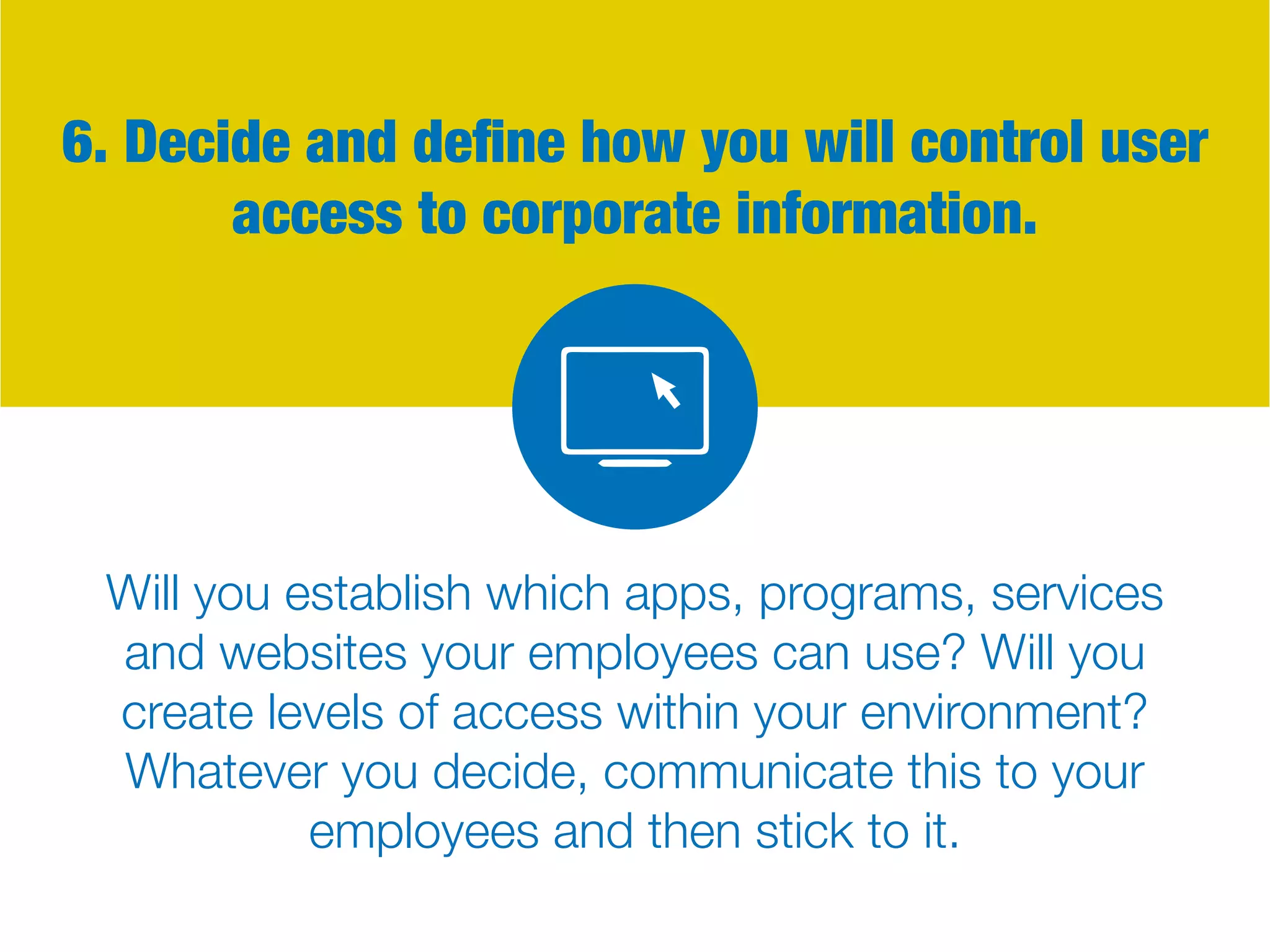
The document discusses the Bring Your Own Device (BYOD) trend, highlighting its advantages such as increased productivity and employee satisfaction, but also addressing significant security risks. It provides a comprehensive guide on creating effective BYOD policies, focusing on training, device restrictions, access controls, and consequences for policy violations. Overall, a well-implemented BYOD strategy can enhance employee mobility while ensuring corporate data security.