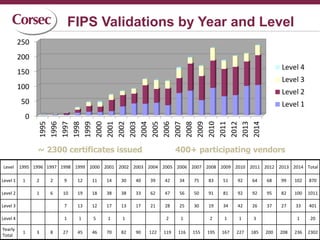
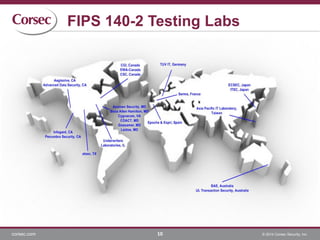
The document discusses the complexities and challenges of navigating cryptographic certifications that product vendors must obtain to sell in various countries, which leads to increased costs and effort. It highlights the need for common standards, suggesting improvements like an international standard based on existing frameworks such as FIPS 140-2 and ISO 19790. The final thoughts emphasize that while FIPS 140-2 has become a standard, there are gaps in the ISO 19790 standard regarding authority and economic motivation, pointing to the advantages of a unified cryptographic evaluation process.