Honeynet architecture
•
1 like•847 views
Honeynets are networks designed to be hacked so that attacker activities and methods can be studied. They are placed behind a reverse firewall to limit outgoing traffic. Honeynets provide valuable data but require significant resources and pose risks; they offer a narrow view of attacks but can help detect new threats. Overall, Honeynets help prepare for attacks by providing deep information about hacking techniques.
Report
Share
Report
Share
Download to read offline
Recommended
Tools and methods used in cybercrime

The document discusses various tools and methods used in cybercrime, including proxy servers, anonymizers, phishing, password cracking, keyloggers, viruses, worms, Trojan horses, backdoors, steganography, denial of service attacks, SQL injection, and buffer overflows. It provides details on how each method works and how attackers use them to launch cyber attacks. The document also outlines the basic stages of a cyber attack, from initial reconnaissance to covering tracks.
Chapter 7 Presentation

This document summarizes key elements from a chapter about network security fundamentals. It describes how standard networking devices like switches, routers, load balancers and proxies can provide basic security features. It also explains how network security hardware devices like firewalls, spam filters, VPNs, intrusion detection/prevention systems and unified threat management appliances provide enhanced security. Finally, it discusses how network technologies like NAT, PAT and NAC can be used to enhance security. The overall goal is to illustrate how layered network security can be achieved through the use of both standard networking devices and specialized security hardware.
CYBER SECURITY.pdf

Cyber security is about protecting information systems from cyber threats through people, processes, and technologies. It ensures the confidentiality, integrity, and availability of data and systems. Cyber attacks can be extremely costly for businesses due to financial losses and reputational damage. Common cyber attacks include injection attacks, DNS spoofing, session hijacking, and phishing on websites. Proper cyber security is crucial in today's digital world to defend against various cyber threats.
Ch 10: Hacking Web Servers

Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Cybersecurity 2 cyber attacks

Cyber attacks can take several forms, including cyber fraud aimed at monetary gain, cyber spying to obtain private information, cyber stalking and bullying to frighten or intimidate individuals, cyber assault to cause damage through malware or denial of service attacks, and cyber warfare between nation states seeking to disrupt critical infrastructure through digital means.
Firewall & its configurations

Firewalls are systems designed to prevent unauthorized access to private networks. There are several types of firewalls, including packet-filtering routers, stateful inspection firewalls, application proxies, and circuit-level gateways. Firewalls can be configured in different ways, such as using a single bastion host with a packet-filtering router, a dual-homed bastion host, or a screened subnet configuration with two routers and a bastion host subnet for the highest level of security.
Cyber crime and cyber laws

This document discusses cyber crimes and cyber laws in India. It defines cyber crime as criminal activities conducted online or using the internet. It outlines various types of cyber crimes like credit card fraud, software piracy, and cyber terrorism. It also discusses statistics on common types of cyber attacks. The document then examines India's Information Technology Act 2000 which defines cyber crimes and assigns investigation of such crimes to authorized police officers. It analyzes sections 65, 66, and 67 which pertains to tampering with computer source documents, hacking, and publishing obscene content online. It notes challenges faced by law enforcement in dealing with cyber crimes and provides tips to enhance cyber safety.
Recommended
Tools and methods used in cybercrime

The document discusses various tools and methods used in cybercrime, including proxy servers, anonymizers, phishing, password cracking, keyloggers, viruses, worms, Trojan horses, backdoors, steganography, denial of service attacks, SQL injection, and buffer overflows. It provides details on how each method works and how attackers use them to launch cyber attacks. The document also outlines the basic stages of a cyber attack, from initial reconnaissance to covering tracks.
Chapter 7 Presentation

This document summarizes key elements from a chapter about network security fundamentals. It describes how standard networking devices like switches, routers, load balancers and proxies can provide basic security features. It also explains how network security hardware devices like firewalls, spam filters, VPNs, intrusion detection/prevention systems and unified threat management appliances provide enhanced security. Finally, it discusses how network technologies like NAT, PAT and NAC can be used to enhance security. The overall goal is to illustrate how layered network security can be achieved through the use of both standard networking devices and specialized security hardware.
CYBER SECURITY.pdf

Cyber security is about protecting information systems from cyber threats through people, processes, and technologies. It ensures the confidentiality, integrity, and availability of data and systems. Cyber attacks can be extremely costly for businesses due to financial losses and reputational damage. Common cyber attacks include injection attacks, DNS spoofing, session hijacking, and phishing on websites. Proper cyber security is crucial in today's digital world to defend against various cyber threats.
Ch 10: Hacking Web Servers

Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Cybersecurity 2 cyber attacks

Cyber attacks can take several forms, including cyber fraud aimed at monetary gain, cyber spying to obtain private information, cyber stalking and bullying to frighten or intimidate individuals, cyber assault to cause damage through malware or denial of service attacks, and cyber warfare between nation states seeking to disrupt critical infrastructure through digital means.
Firewall & its configurations

Firewalls are systems designed to prevent unauthorized access to private networks. There are several types of firewalls, including packet-filtering routers, stateful inspection firewalls, application proxies, and circuit-level gateways. Firewalls can be configured in different ways, such as using a single bastion host with a packet-filtering router, a dual-homed bastion host, or a screened subnet configuration with two routers and a bastion host subnet for the highest level of security.
Cyber crime and cyber laws

This document discusses cyber crimes and cyber laws in India. It defines cyber crime as criminal activities conducted online or using the internet. It outlines various types of cyber crimes like credit card fraud, software piracy, and cyber terrorism. It also discusses statistics on common types of cyber attacks. The document then examines India's Information Technology Act 2000 which defines cyber crimes and assigns investigation of such crimes to authorized police officers. It analyzes sections 65, 66, and 67 which pertains to tampering with computer source documents, hacking, and publishing obscene content online. It notes challenges faced by law enforcement in dealing with cyber crimes and provides tips to enhance cyber safety.
Security and management

security concepts ,goals of computer security , problem and requirements ,identifying the assets ,identifying the threats, identifying the impacts, vulnerability ,user authentication ,security system and facilities ,system access control , password management ,privileged user management ,user account management ,data resource protection, sensitive system protection ,cryptography ,intrusion detection ,computer-security classification
1. introduction to cyber security

Cyber security refers to protecting networks, devices, programs and data from unauthorized access or cyber attacks. It involves technologies and practices to ensure security, availability and integrity of information systems. Without proper cyber security measures like risk assessments, organizations risk exposing sensitive data like intellectual property, financial information and personal data. The top five cyber risks are ransomware, phishing, data leakage from mobile devices, hacking, and insider threats from employees. Organizations should implement security best practices like access controls, malware protection, software updates, data backups and employee training to mitigate these risks.
Network security (syed azam)

:- Network security is protection of the access to files and directories in a computer network against hacking, misuse and unauthorised changes to the system.
Cyber Crime And Security 

Short Presentation On Cyber Crime And Security which includes Cyber crime introduction and types , Hacking and its types, different Threats , and in last Prevention for Hacks and Threats.
Nikto

Nikto is a free and open source web server scanner used to identify vulnerabilities and help secure servers. It tests servers for over 6,500 dangerous files and scripts, outdated versions of software, and misconfigurations. Nikto scans target servers and outputs results that can help identify security problems. It has advantages like being fast, versatile, and open source, while its only disadvantage is needing to run via the command line.
Chapter 9 Client and application Security

The document discusses various methods for securing client devices and applications. It describes securing the client by using hardware system security, securing the operating system software, and protecting peripheral devices. Specific techniques discussed include secure booting using UEFI and secure boot standards, establishing a hardware root of trust, preventing electromagnetic spying, and addressing risks from supply chain infections. The document also covers securing the operating system through configuration, patch management, and using antimalware software like antivirus, antispam, and antispyware programs.
Cyber crime and Security

This document discusses cyber crime and cyber security. It begins with an introduction and overview of the history and categories of cyber crime. Some key types of cyber crime discussed include hacking, denial of service attacks, and child pornography. The document then covers advantages of cyber security like privacy policies and keeping software updated. It concludes by noting that cyber crime involves both traditional crimes and new crimes addressed by cyber law, and that cyber security is needed to help combat cyber criminals.
Ethical hacking

Ethical hacking involves using the same techniques as malicious hackers but in a lawful and legitimate way to test an organization's security and help improve it. An ethical hacker obtains permission, then attempts to find and report on vulnerabilities to help organizations fix security issues before criminals can exploit them. The goal is to maintain authorized access, avoid damaging systems, and respect confidentiality and privacy. Ethical hacking follows steps like reconnaissance, scanning, access, reporting results and recommending solutions. It helps balance security, functionality and ease of use.
Vulnerability assessment and penetration testing

This document discusses vulnerability assessment and penetration testing. It defines them as two types of vulnerability testing that search for known vulnerabilities and attempt to exploit vulnerabilities, respectively. Vulnerability assessment uses automated tools to detect known issues, while penetration testing employs hacking techniques to demonstrate how deeply vulnerabilities could be exploited like an actual attacker. Both are important security practices for identifying weaknesses and reducing risks, but require different skills and have different strengths, weaknesses, frequencies, and report outputs. Reasons for vulnerabilities include insecure coding, limited testing, and misconfigurations. The document outlines common vulnerability and attack types as well as how vulnerability assessment and penetration testing are typically conducted.
Advanced persistent threats(APT)

Advanced Persistent Threats (APTs) are a serious concern as they represent a threat to an organization’s intellectual property, financial assets and reputation. In some cases, these threats target critical infrastructure and government institutions, thereby threatening the country’s national security itself.
Vulnerabilities in modern web applications

Microsoft powerpoint presentation for BTech academic seminar.This seminar discuses about penetration testing, penetration testing tools, web application vulnerabilities, impact of vulnerabilities and security recommendations.
Ethical Hacking PPT (CEH)

The document discusses Certified Ethical Hacking (CEH). It defines CEH as a course focused on offensive network security techniques. It contrasts ethical hacking with malicious hacking, noting ethical hacking involves identifying vulnerabilities with permission to help strengthen security. It outlines the hacking process and differences between white hat, black hat, and grey hat hackers. Finally, it provides tips for system protection and advantages of ethical hacking over traditional security approaches.
Cybercrime

Cyberwarfare, also known as cyberterrorism, refers to politically motivated attacks on computer systems and networks. The document discusses various methods of cyberwarfare such as espionage, sabotage, and attacks on critical infrastructure networks. Specific examples of cyberattacks between nations are provided, such as attacks from Russia on Estonia in 2007 and cyber operations between the US and Iran in 2012. The document also examines cybercrime trends in Greece and strategies for improving cybersecurity defenses.
Cyber Law And Ethics

Cyber law deals with legal issues related to the internet, computers, and technology. It aims to prevent cybercrimes like hacking and protect privacy and intellectual property online. Laws regulating cyber activities vary by jurisdiction and can be challenging to enforce. The Information Technology Act of 2000 in India recognizes electronic transactions and digital signatures to facilitate e-governance and commerce while also addressing cybercrime. It was later amended in 2008 to address new issues and security concerns as technology advanced.
Chapter 2 Presentation

This document discusses malware and social engineering attacks. It defines malware and lists common types, including viruses, worms, Trojans, spyware, and ransomware. It describes how malware can spread, hide, and carry out harmful payloads like collecting sensitive data, deleting files, modifying security settings, and launching attacks. The document also outlines psychological and physical social engineering techniques used to trick users into revealing confidential information.
Brute force attack

A Brute Force Attack is the simplest method to gain access to a site or server (or anything that is password protected). It tries various combinations of usernames and passwords until it gets in. This repetitive action is like an army attacking a fort.
Cyber Space

Cyberspace is a domain characterized by the use of electronics and the electromagnetic spectrum to store, modify, and exchange data via networked systems and associated physical infrastructures.
CyberSecurity

Cybersecurity involves protecting computers, networks, programs, and data from digital attacks. It includes topics like hacking, denial of service attacks, cyber terrorism, and software piracy. Some key aspects of cybersecurity are using antivirus software, anti-spyware, firewalls, secure passwords, and maintaining regular backups to protect private information and systems from viruses, malware, and unauthorized access. Understanding different types of hackers like white hat, grey hat, and black hat is also important for cybersecurity.
Pranavi verma-cyber-security-ppt

This document discusses various techniques used in cyber security, including malware protection programs, internet gateways and firewalls, secure configurations, patch management, and user access control. It also describes common types of malicious attacks like spyware and viruses, as well as password attacks. Cyber security aims to analyze attack codes, block malicious software from entering secure networks, limit user privileges, and keep software updated to prevent infections. The document also briefly outlines types of cyber attacks like cyber war and cybercrime, as well as cyber threats from criminals, spies, and terrorists. Finally, it mentions that cyber security projects use the "9D's concept" to avoid distributed denial of service attacks, which involves deterring, detecting, driving up difficulty, and
Building An Information Security Awareness Program

Most organization’s Security Awareness Programs suck. They involved ‘canned’ video presentations or someone is HR explaining computer use policies. Others are extremely expensive and beyond the reach of the budgets of smaller organizations. This talk will show you how to build a Security Awareness Program from scratch for little or no money, and how to engage your users so that they get the most out of the program.
Lessons Learned from Building and Running MHN, the World's Largest Crowdsourc...

Honeypots are really useful for collecting security data for research, especially around botnets, scanning hosts, password brute forcers, and other misbehaving systems. They are also the cheapest way collect this data at scale. Deploying many types of honeypots across geo-diverse locations of the Internet improves the aggregate data quality and provides a holistic view. This provides insight into both global trends of attacks and network activity as well as the behaviors of individual malicious systems. For these reasons, we started the Modern Honey Network, which is both an open source (GPLv3) project and a community of hundreds of MHN servers that manage and aggregate data from thousands of heterogeneous honeypots (Dionaea, Kippo, Amun, Conpot, Wordpot, Shockpot, and Glastopf) and network sensors (Snort, Suricata, p0f) deployed by different individuals and organizations as a distributed sensor network. The project has turned into the largest crowdsourced honeynet in the world consisting of thousands of diverse sensors deployed across 35 countries and 5 continents worldwide. Sensors are operated by all sorts of people from hobbyists, to academic researchers, to Fortune 1000 companies. In this talk we will discuss our experience in starting this project, analyzing the data, and building a crowdsourced global sensor network for tracking security threats and gathering interesting data for research. We've found that lots of people like honeypots, especially if you give them a cool realtime visualization of their data and make it easy to setup; lots of organizations will share their data with you if it is part of a community; and lots of companies will deploy honeypots as additional network sensors, especially if you make it easy to deploy/manage/integrate with their existing security tools.
SANS CTI Summit 2016 Borderless Threat Intelligence

This past year was the year of the data breach. Large and small organizations across every industry vertical were impacted by compromises that ranged from theft of PII, intellectual property, and financial information to publication of entire backend databases and email spools. The data from these breaches often wound up being exposed publicly, exchanged or sold on underground markets, or simply leveraged to breach other organizations. Many of these breaches have cascading effects due to the transitive nature of security that exists across many companies. Many companies rely on critical business partners, subsidiaries, and other organizations whose services are trusted. Also, due to password reuse customers accounts included in a 3rd party data dump could enable unauthorized access to another business's assets.
In this talk we outline through case studies several ways that Threat Intelligence is being used today to improve the security and awareness of organizations by monitoring "supply chain" partners, customers, and trusted 3rd parties. Specifically we will discuss brand monitoring, mass credential compromises, signs of infection/compromise, and signs of targeting and social networking data-mining. We will outline how organizations can effectively integrate this practice into their existing security programs.
More Related Content
What's hot
Security and management

security concepts ,goals of computer security , problem and requirements ,identifying the assets ,identifying the threats, identifying the impacts, vulnerability ,user authentication ,security system and facilities ,system access control , password management ,privileged user management ,user account management ,data resource protection, sensitive system protection ,cryptography ,intrusion detection ,computer-security classification
1. introduction to cyber security

Cyber security refers to protecting networks, devices, programs and data from unauthorized access or cyber attacks. It involves technologies and practices to ensure security, availability and integrity of information systems. Without proper cyber security measures like risk assessments, organizations risk exposing sensitive data like intellectual property, financial information and personal data. The top five cyber risks are ransomware, phishing, data leakage from mobile devices, hacking, and insider threats from employees. Organizations should implement security best practices like access controls, malware protection, software updates, data backups and employee training to mitigate these risks.
Network security (syed azam)

:- Network security is protection of the access to files and directories in a computer network against hacking, misuse and unauthorised changes to the system.
Cyber Crime And Security 

Short Presentation On Cyber Crime And Security which includes Cyber crime introduction and types , Hacking and its types, different Threats , and in last Prevention for Hacks and Threats.
Nikto

Nikto is a free and open source web server scanner used to identify vulnerabilities and help secure servers. It tests servers for over 6,500 dangerous files and scripts, outdated versions of software, and misconfigurations. Nikto scans target servers and outputs results that can help identify security problems. It has advantages like being fast, versatile, and open source, while its only disadvantage is needing to run via the command line.
Chapter 9 Client and application Security

The document discusses various methods for securing client devices and applications. It describes securing the client by using hardware system security, securing the operating system software, and protecting peripheral devices. Specific techniques discussed include secure booting using UEFI and secure boot standards, establishing a hardware root of trust, preventing electromagnetic spying, and addressing risks from supply chain infections. The document also covers securing the operating system through configuration, patch management, and using antimalware software like antivirus, antispam, and antispyware programs.
Cyber crime and Security

This document discusses cyber crime and cyber security. It begins with an introduction and overview of the history and categories of cyber crime. Some key types of cyber crime discussed include hacking, denial of service attacks, and child pornography. The document then covers advantages of cyber security like privacy policies and keeping software updated. It concludes by noting that cyber crime involves both traditional crimes and new crimes addressed by cyber law, and that cyber security is needed to help combat cyber criminals.
Ethical hacking

Ethical hacking involves using the same techniques as malicious hackers but in a lawful and legitimate way to test an organization's security and help improve it. An ethical hacker obtains permission, then attempts to find and report on vulnerabilities to help organizations fix security issues before criminals can exploit them. The goal is to maintain authorized access, avoid damaging systems, and respect confidentiality and privacy. Ethical hacking follows steps like reconnaissance, scanning, access, reporting results and recommending solutions. It helps balance security, functionality and ease of use.
Vulnerability assessment and penetration testing

This document discusses vulnerability assessment and penetration testing. It defines them as two types of vulnerability testing that search for known vulnerabilities and attempt to exploit vulnerabilities, respectively. Vulnerability assessment uses automated tools to detect known issues, while penetration testing employs hacking techniques to demonstrate how deeply vulnerabilities could be exploited like an actual attacker. Both are important security practices for identifying weaknesses and reducing risks, but require different skills and have different strengths, weaknesses, frequencies, and report outputs. Reasons for vulnerabilities include insecure coding, limited testing, and misconfigurations. The document outlines common vulnerability and attack types as well as how vulnerability assessment and penetration testing are typically conducted.
Advanced persistent threats(APT)

Advanced Persistent Threats (APTs) are a serious concern as they represent a threat to an organization’s intellectual property, financial assets and reputation. In some cases, these threats target critical infrastructure and government institutions, thereby threatening the country’s national security itself.
Vulnerabilities in modern web applications

Microsoft powerpoint presentation for BTech academic seminar.This seminar discuses about penetration testing, penetration testing tools, web application vulnerabilities, impact of vulnerabilities and security recommendations.
Ethical Hacking PPT (CEH)

The document discusses Certified Ethical Hacking (CEH). It defines CEH as a course focused on offensive network security techniques. It contrasts ethical hacking with malicious hacking, noting ethical hacking involves identifying vulnerabilities with permission to help strengthen security. It outlines the hacking process and differences between white hat, black hat, and grey hat hackers. Finally, it provides tips for system protection and advantages of ethical hacking over traditional security approaches.
Cybercrime

Cyberwarfare, also known as cyberterrorism, refers to politically motivated attacks on computer systems and networks. The document discusses various methods of cyberwarfare such as espionage, sabotage, and attacks on critical infrastructure networks. Specific examples of cyberattacks between nations are provided, such as attacks from Russia on Estonia in 2007 and cyber operations between the US and Iran in 2012. The document also examines cybercrime trends in Greece and strategies for improving cybersecurity defenses.
Cyber Law And Ethics

Cyber law deals with legal issues related to the internet, computers, and technology. It aims to prevent cybercrimes like hacking and protect privacy and intellectual property online. Laws regulating cyber activities vary by jurisdiction and can be challenging to enforce. The Information Technology Act of 2000 in India recognizes electronic transactions and digital signatures to facilitate e-governance and commerce while also addressing cybercrime. It was later amended in 2008 to address new issues and security concerns as technology advanced.
Chapter 2 Presentation

This document discusses malware and social engineering attacks. It defines malware and lists common types, including viruses, worms, Trojans, spyware, and ransomware. It describes how malware can spread, hide, and carry out harmful payloads like collecting sensitive data, deleting files, modifying security settings, and launching attacks. The document also outlines psychological and physical social engineering techniques used to trick users into revealing confidential information.
Brute force attack

A Brute Force Attack is the simplest method to gain access to a site or server (or anything that is password protected). It tries various combinations of usernames and passwords until it gets in. This repetitive action is like an army attacking a fort.
Cyber Space

Cyberspace is a domain characterized by the use of electronics and the electromagnetic spectrum to store, modify, and exchange data via networked systems and associated physical infrastructures.
CyberSecurity

Cybersecurity involves protecting computers, networks, programs, and data from digital attacks. It includes topics like hacking, denial of service attacks, cyber terrorism, and software piracy. Some key aspects of cybersecurity are using antivirus software, anti-spyware, firewalls, secure passwords, and maintaining regular backups to protect private information and systems from viruses, malware, and unauthorized access. Understanding different types of hackers like white hat, grey hat, and black hat is also important for cybersecurity.
Pranavi verma-cyber-security-ppt

This document discusses various techniques used in cyber security, including malware protection programs, internet gateways and firewalls, secure configurations, patch management, and user access control. It also describes common types of malicious attacks like spyware and viruses, as well as password attacks. Cyber security aims to analyze attack codes, block malicious software from entering secure networks, limit user privileges, and keep software updated to prevent infections. The document also briefly outlines types of cyber attacks like cyber war and cybercrime, as well as cyber threats from criminals, spies, and terrorists. Finally, it mentions that cyber security projects use the "9D's concept" to avoid distributed denial of service attacks, which involves deterring, detecting, driving up difficulty, and
Building An Information Security Awareness Program

Most organization’s Security Awareness Programs suck. They involved ‘canned’ video presentations or someone is HR explaining computer use policies. Others are extremely expensive and beyond the reach of the budgets of smaller organizations. This talk will show you how to build a Security Awareness Program from scratch for little or no money, and how to engage your users so that they get the most out of the program.
What's hot (20)
Building An Information Security Awareness Program

Building An Information Security Awareness Program
Viewers also liked
Lessons Learned from Building and Running MHN, the World's Largest Crowdsourc...

Honeypots are really useful for collecting security data for research, especially around botnets, scanning hosts, password brute forcers, and other misbehaving systems. They are also the cheapest way collect this data at scale. Deploying many types of honeypots across geo-diverse locations of the Internet improves the aggregate data quality and provides a holistic view. This provides insight into both global trends of attacks and network activity as well as the behaviors of individual malicious systems. For these reasons, we started the Modern Honey Network, which is both an open source (GPLv3) project and a community of hundreds of MHN servers that manage and aggregate data from thousands of heterogeneous honeypots (Dionaea, Kippo, Amun, Conpot, Wordpot, Shockpot, and Glastopf) and network sensors (Snort, Suricata, p0f) deployed by different individuals and organizations as a distributed sensor network. The project has turned into the largest crowdsourced honeynet in the world consisting of thousands of diverse sensors deployed across 35 countries and 5 continents worldwide. Sensors are operated by all sorts of people from hobbyists, to academic researchers, to Fortune 1000 companies. In this talk we will discuss our experience in starting this project, analyzing the data, and building a crowdsourced global sensor network for tracking security threats and gathering interesting data for research. We've found that lots of people like honeypots, especially if you give them a cool realtime visualization of their data and make it easy to setup; lots of organizations will share their data with you if it is part of a community; and lots of companies will deploy honeypots as additional network sensors, especially if you make it easy to deploy/manage/integrate with their existing security tools.
SANS CTI Summit 2016 Borderless Threat Intelligence

This past year was the year of the data breach. Large and small organizations across every industry vertical were impacted by compromises that ranged from theft of PII, intellectual property, and financial information to publication of entire backend databases and email spools. The data from these breaches often wound up being exposed publicly, exchanged or sold on underground markets, or simply leveraged to breach other organizations. Many of these breaches have cascading effects due to the transitive nature of security that exists across many companies. Many companies rely on critical business partners, subsidiaries, and other organizations whose services are trusted. Also, due to password reuse customers accounts included in a 3rd party data dump could enable unauthorized access to another business's assets.
In this talk we outline through case studies several ways that Threat Intelligence is being used today to improve the security and awareness of organizations by monitoring "supply chain" partners, customers, and trusted 3rd parties. Specifically we will discuss brand monitoring, mass credential compromises, signs of infection/compromise, and signs of targeting and social networking data-mining. We will outline how organizations can effectively integrate this practice into their existing security programs.
Modern Honey Network (MHN)

Open source platform for deploying/managing Honeypots & using their data http://threatstream.github.io/mhn/
Anomali Detect 2016 - Borderless Threat Intelligence

The document discusses using external threat intelligence to monitor brands and supply chains. It recommends inventorying important external assets and integrating threat intelligence data sources. Specific sources discussed include suspicious domain registrations, network cleanliness data, social media/dark web monitoring, credential exposures, and phishing campaigns. Case studies show how these sources uncovered fraudulent procurement attempts, risky vendors, leaked credentials, and brand-targeting attacks. The document emphasizes that organizations must monitor beyond their own networks to identify supply chain threats.
Mirai botnet

1) The document discusses the Mirai botnet, which infects internet-of-things devices like IP cameras through factory default credentials and spreads by scanning for other vulnerable devices to recruit into the botnet.
2) It describes how exposing a camera directly to the internet resulted in it being compromised by Mirai within minutes, as the malware used telnet to upload itself and then contacted command-and-control servers.
3) The presenter argues that insecure IoT supply chain practices that prioritize low cost over security have contributed to the proliferation of botnets like Mirai, and advocates for improving security of IoT devices.
MIRAI: What is It, How Does it Work and Why Should I Care?

Cyber Security in 2017! What can Smart Buildings expect?.
These are the slides from a conversation with Billy Rios, Founder of WhiteScope LLC. We take a deep dive into the Mirai DDoS Attacks from last year and try to understand what lessons can be learnt going forward.
Honeycon2016-honeypot updates for public

This slide is related to honeypot tools. Also introduce what kinds of attacks collecting by honeypots
R-CISC Summit 2016 Borderless Threat Intelligence

Self and supply chain monitoring using External Threat Intelligence. Presented at R-CISC Summit 2016.
Honeypot honeynet

Honeypots are information systems designed to detect attacks by capturing unauthorized access. A honeypot mimics real systems to attract hackers while logging their activities without exposing real systems to harm. Honeynets are networks of high-interaction honeypots that provide whole systems for hackers to interact with and reveal their tactics. While helpful for research, honeypots require careful control and monitoring to prevent real damage while gathering forensic data on intrusions and attacks.
Viewers also liked (9)
Lessons Learned from Building and Running MHN, the World's Largest Crowdsourc...

Lessons Learned from Building and Running MHN, the World's Largest Crowdsourc...
SANS CTI Summit 2016 Borderless Threat Intelligence

SANS CTI Summit 2016 Borderless Threat Intelligence
Anomali Detect 2016 - Borderless Threat Intelligence

Anomali Detect 2016 - Borderless Threat Intelligence
MIRAI: What is It, How Does it Work and Why Should I Care?

MIRAI: What is It, How Does it Work and Why Should I Care?
Similar to Honeynet architecture
The use of honeynet to detect exploited systems (basic version)

This document discusses the use of honeynets to detect exploited systems and hackers. It begins with an abstract and introduction on the topic. It then provides definitions of key terms like honeynet and honeypot. It describes the principles of data capture and data control that honeynets rely on. It discusses the differences between first (GEN I) and second (GEN II) generation honeynets. It outlines the typical honeynet architecture including honeypots and honeywalls. It explains how honeynets work to study attacker activities and methods. Finally, it discusses some advantages like high value data and simplicity, and disadvantages like narrow field of view of using honeynets.
Basics of Cyber Security

This document provides an overview of cyber security and discusses recent issues in India. It begins with definitions of cyberspace and discusses the rapid growth of internet connectivity globally and in India. It then covers cyber security challenges, the evolution of threats, and recent cyber attacks impacting India. The document concludes with 10 steps for organizations to improve cyber security, such as network security, malware protection, user education, and information risk management.
2014-09-03 Cybersecurity and Computer Crimes

This document discusses computer crimes and cybersecurity issues, with a focus on the human element. It provides definitions and examples of various computer crimes like computer fraud, internet fraud, and modernizing traditional crimes using computers. It also discusses social engineering frauds like pretexting and phishing. For cybersecurity, it covers topics such as firewalls, intrusion detection, denial of service attacks, malware, ransomware, and how to protect against threats. The overall message is that while technology plays a role, human behaviors and decisions are often the weak link exploited in crimes and attacks.
2014-09-03 Cybersecurity and Computer Crimes

This document summarizes common computer crimes and cybersecurity issues. It discusses how computer crimes are defined and prosecuted, as well as types of computer-aided fraud such as manipulating computer inputs, programs, and outputs. Cybersecurity topics covered include firewalls, intrusion detection, denial of service attacks, dictionary attacks, and different types of malware like viruses, worms, Trojan horses, rootkits, botnets, and ransomware. The document also discusses social engineering frauds like pretexting and various forms of phishing.
Honeypot

Honeypots are systems designed to detect attacks by simulating vulnerable systems and monitoring interactions. There are three main types - low-interaction honeypots like Honeyd that simulate services, and high-interaction Gen I and Gen II Honeynets that provide whole system emulations. Honeypots provide prevention by wasting attackers' time, detection of attacks, and research opportunities to understand attack techniques. While they add complexity, honeypots also help with incident response and protecting real systems from learned attacks. Future work may include easier administration, closer integration with other security tools, and more targeted uses.
Staying Safe and Secure Online

Have you ever been infected by a computer virus or experienced online fraud? Our electronic world poses diverse threats to our online security that have very real financial and personal consequences. Viruses and other malware, identity theft, credit card fraud, social media threats, cyber stalking – are all among the supernumerary risks that we face in our electronic world. Come learn what you can do in very practical terms to protect and secure your digital life. By the end of this course you will have a tool to arm yourself and shield your digital world. Join us for a down to earth, jargon free and fun exploration and learn the practical ways you can safeguard your identity, reputation and financial health.
Honeypots and honeynets

This document discusses honeypots and honeynets. It begins by explaining that honeypots are fake vulnerable systems used to collect information from attackers without being harmed. There are two main types - low interaction honeypots that emulate services and high interaction honeypots that use real systems. Honeynets are networks of high interaction honeypots used to capture in-depth information on attacks. The document outlines the benefits of honeypots for gathering threat intelligence and tracking attackers. It also discusses some popular honeypot tools and the growing cybersecurity market.
NETWORK SECURITY

This document discusses network security and various cyber attacks. It defines network security and lists common security devices. It outlines different types of hackers and cyber attacks such as hacking, DDoS attacks, malware, Trojan horses, spam, phishing, and packet sniffers. The document also discusses worms, viruses, botnets, and how to protect critical information infrastructure. It provides examples of security software and firewall types. Finally, it discusses challenges in network security and provides references for further information.
Client Honeypot Based Drive by Download Exploit Detection and their Categoriz...

Client side attacks are those which exploits the vulnerabilities in client side applications such as browsers, plug-ins etc. The remote attackers execute the malicious code in end user’s system without his knowledge. Here in this research, we propose to detect and measure the drive by download class of malware which infect the end user’s system through HTTP based propagation mechanism. The purpose of this research is to introduce a class of technology known as client honeypot through which we execute the domains in a virtual machine in more optimized manner. Those virtual machines are the controlled environment for the execution of those URLs. During the execution of the websites, the PE files dropped into the system are logged and further analyzed for categorization of malware. Further the critical analysis has been performed by applying some reverse engineering techniques to categories the class of malware and source of infections performed by the malware.
Cyber security

This document discusses cyber security and cyber crimes related to banking. It defines cyber security as the protection of internet-connected systems, including hardware, software and data, from cyber attacks. It then discusses examples of major cyber security threats to the banking sector like unencrypted data, unprotected third party services, and an constantly changing threat landscape. The document also defines different types of cyber crimes like hacking, phishing, and ransomware and explains how hackers managed to steal over Rs. 94 crore from an attack on Pune-based Cosmos Bank's server in 2018.
Information Security

Cyber security involves protecting data, systems, and infrastructure from digital threats. It includes classifying data based on sensitivity, applying principles of confidentiality, integrity and availability to protect data, and using authentication, authorization and accountability to control access. Common cyber crimes include hacking, denial of service attacks, identity theft, and software piracy. Organizations must implement appropriate security measures and policies to defend against cyber threats.
Insider Threat Solution from GTRI

Insider threats come in a variety of forms and may be malicious or simply the result of negligence. Insider attacks can cause more damage than outsider threats, so it is important that organizations understand how to protect against and remedy insider threats. Learn more about insider threats and GTRI's Insider Threat Security Solution in this presentation. (Source: GTRI)
This presentation includes information about Cisco Stealthwatch, which goes beyond conventional threat detection and harnesses the power of NetFlow. With it, you get advanced network visibility, analytics, and protection. You see everything happening across your network and data center. And you can uncover attacks that bypass the perimeter and infiltrate your internal environment. (Source: Cisco)
MULTI-LEVEL PARSING BASED APPROACH AGAINST PHISHING ATTACKS WITH THE HELP OF ...

The increasing use of internet all over the world, be it in households or in corporate firms, has led to an unprecedented rise in cyber-crimes. Amongst these the major chunk consists of Internet attacks which are the most popular and common attacks are carried over the internet. Generally phishing attacks, SSL attacks and some other hacking attacks are kept into this category. Security against these attacks is the major issue of internet security in today’s scenario where internet has very deep penetration. Internet has no doubt made our lives very convenient. It has provided many facilities to us at penny’s cost. For instance it has made communication lightning fast and that too at a very cheap cost. But internet can pose added threats for those users who are not well versed in the ways of internet and unaware of the security risks attached with it. Phishing Attacks, Nigerian Scam, Spam attacks, SSL attacks and other hacking attacks are some of the most common and recent attacks to compromise the privacy of the internet users. Many a times if the user isn’t careful, then these attacks are able to steal the confidential information of user (or unauthorized access). Generally these attacks are carried out with the help of social networking sites, popular mail server sites, online chatting sites etc. Nowadays, Facebook.com, gmail.com, orkut.com and many other social networking sites are facing these security attack problems.
This paper discusses a Knowledge Base Compound approach which is based on query operations and parsing techniques to counter these internet attacks using the web browser itself. In this approach we propose to analyze the web URLs before visiting the actual site, so as to provide security against web attacks mentioned above. This approach employs various parsing operations and query processing which use many techniques to detect the phishing attacks as well as other web attacks. The aforementioned approach is completely based on operation through the browser and hence only affects the speed of browsing. This approach also includes Crawling operation to detect the URL details to further enhance the precision of detection of a compromised site. Using the proposed methodology, a new browser can easily detects the phishing attacks, SSL attacks, and other hacking attacks. With the use of this browser approach, we can easily achieve 96.94% security against phishing as well as other web based attacks.
Cybersecurity.pptx

Cybersecurity involves protecting important data, networks, and computer systems from unauthorized access or criminal activity. The demand for cybersecurity professionals is growing rapidly due to increased internet usage and cybercrime. Some key areas of study to work in cybersecurity include information security analysis, coordination, engineering, software security specialization, and cryptography. Effective cybersecurity requires protecting all aspects of an organization's people, processes, technology, computers and networks.
Good Guys vs Bad Guys: Using Big Data to Counteract Advanced Threats

The document discusses using big data analytics to counter advanced cyber threats. It notes that traditional security information and event management (SIEM) systems have limitations in detecting advanced threats due to incomplete data collection and inflexible analytics. A big data solution collects data from all possible sources, including network, endpoint, mobile and cloud systems. It then applies analytics to identify anomalous patterns that may indicate advanced threat activity based on factors like unusual user behavior, network connections, or changes from normal baselines. This helps security teams more effectively detect threats that can evade traditional defenses and are difficult to identify with signature-based tools alone.
Internal host-reputation-webinar

With so many new threat actors out there, IP reputation is becoming increasingly critical for effectively combating attacks. Under today’s security paradigm, administrators need to know not only about the bad guys lurking on the Internet, but also about the ones operating inside the network perimeter.
Lancope uniquely provides both internal and external host reputation, better preparing organizations to: combat APTs and insider threats, address BYOD challenges, and deliver actionable information for security teams.
Learn how to leverage internal host reputation to uncover a wide range of suspicious user behaviors such as:
* Sending out an unusual amount of traffic
* Communicating with known, bad external hosts
* Accessing restricted areas of the network
* Spreading malware
Cyber Security

The team aims to detect phishing links using machine learning and natural language processing techniques. They will mark phishing links as spam or harmful and prevent users from clicking on them. Their proposed solution is to create a system that can detect and warn users about phishing links. They will analyze URLs, domain information, page content, and other features to classify domains as phishing or legitimate using a trained machine learning model. Their goal is to increase awareness and provide security by preventing users from interacting with harmful sites.
Cyber crime and security

This document provides an outline on cyber crimes and cyber security. It begins with an introduction on the growth of the internet and the rise of cyber crimes. It then defines cyber crime as unlawful acts using computers as tools or targets. The document categorizes cyber crimes as those using computers as weapons or targets, and lists common types like hacking, viruses, and identity theft. It discusses the history of cyber crimes and reasons they occur like ease of access online and complex networks. The document also defines cyber security, provides advantages like protection from attacks, and offers tips for prevention such as using antivirus software and firewalls. It concludes that cyber security is an ongoing battle and everyone must play a role to be responsible online.
Best_of_Breed_3-24-2015_How_to_Achieve_ABAC_Today copy

This document provides an overview of a workshop on achieving attribute-based access control (ABAC). The workshop featured several presentations on implementing ABAC from industry experts. Topics included the roadmap to implementing ABAC, how to find and use attributes, mobile API management for ABAC, and the ABAC lifecycle. The document also provides a brief summary of each presentation.
Similar to Honeynet architecture (20)
The use of honeynet to detect exploited systems (basic version)

The use of honeynet to detect exploited systems (basic version)
Client Honeypot Based Drive by Download Exploit Detection and their Categoriz...

Client Honeypot Based Drive by Download Exploit Detection and their Categoriz...
MULTI-LEVEL PARSING BASED APPROACH AGAINST PHISHING ATTACKS WITH THE HELP OF ...

MULTI-LEVEL PARSING BASED APPROACH AGAINST PHISHING ATTACKS WITH THE HELP OF ...
Good Guys vs Bad Guys: Using Big Data to Counteract Advanced Threats

Good Guys vs Bad Guys: Using Big Data to Counteract Advanced Threats
Unit 03 Computer and Internet Crime [5 hrs] v1.2.pdf![Unit 03 Computer and Internet Crime [5 hrs] v1.2.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Unit 03 Computer and Internet Crime [5 hrs] v1.2.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Unit 03 Computer and Internet Crime [5 hrs] v1.2.pdf
Best_of_Breed_3-24-2015_How_to_Achieve_ABAC_Today copy

Best_of_Breed_3-24-2015_How_to_Achieve_ABAC_Today copy
Recently uploaded
快速办理(Vic毕业证书)惠灵顿维多利亚大学毕业证完成信一模一样

学校原件一模一样【微信:741003700 】《(Vic毕业证书)惠灵顿维多利亚大学毕业证》【微信:741003700 】学位证,留信认证(真实可查,永久存档)原件一模一样纸张工艺/offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原。
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
【主营项目】
一.毕业证【q微741003700】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【q/微741003700】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
Securing BGP: Operational Strategies and Best Practices for Network Defenders...

Md. Zobair Khan,
Network Analyst and Technical Trainer at APNIC, presented 'Securing BGP: Operational Strategies and Best Practices for Network Defenders' at the Phoenix Summit held in Dhaka, Bangladesh from 23 to 24 May 2024.
HijackLoader Evolution: Interactive Process Hollowing

CrowdStrike researchers have identified a HijackLoader (aka IDAT Loader) sample that employs sophisticated evasion techniques to enhance the complexity of the threat. HijackLoader, an increasingly popular tool among adversaries for deploying additional payloads and tooling, continues to evolve as its developers experiment and enhance its capabilities.
In their analysis of a recent HijackLoader sample, CrowdStrike researchers discovered new techniques designed to increase the defense evasion capabilities of the loader. The malware developer used a standard process hollowing technique coupled with an additional trigger that was activated by the parent process writing to a pipe. This new approach, called "Interactive Process Hollowing", has the potential to make defense evasion stealthier.
一比一原版新西兰林肯大学毕业证(Lincoln毕业证书)学历如何办理

原版办【微信号:95270640】【新西兰林肯大学毕业证(Lincoln毕业证书)】【微信号:95270640】《成绩单、外壳、雅思、offer、真实留信官方学历认证(永久存档/真实可查)》采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路)我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信号95270640】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信号95270640】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
一比一原版(USYD毕业证)悉尼大学毕业证如何办理

USYD硕士毕业证成绩单【微信95270640】《如何办理悉尼大学毕业证认证》【办证Q微信95270640】《悉尼大学文凭毕业证制作》《USYD学历学位证书哪里买》办理悉尼大学学位证书扫描件、办理悉尼大学雅思证书!
国际留学归国服务中心《如何办悉尼大学毕业证认证》《USYD学位证书扫描件哪里买》实体公司,注册经营,行业标杆,精益求精!
如果您是以下情况,我们都能竭诚为您解决实际问题:【公司采用定金+余款的付款流程,以最大化保障您的利益,让您放心无忧】
1、在校期间,因各种原因未能顺利毕业,拿不到官方毕业证+微信95270640
2、面对父母的压力,希望尽快拿到悉尼大学悉尼大学毕业证offer;
3、不清楚流程以及材料该如何准备悉尼大学悉尼大学毕业证offer;
4、回国时间很长,忘记办理;
5、回国马上就要找工作,办给用人单位看;
6、企事业单位必须要求办理的;
面向美国乔治城大学毕业留学生提供以下服务:
【★悉尼大学悉尼大学毕业证offer毕业证、成绩单等全套材料,从防伪到印刷,从水印到钢印烫金,与学校100%相同】
【★真实使馆认证(留学人员回国证明),使馆存档可通过大使馆查询确认】
【★真实教育部认证,教育部存档,教育部留服网站可查】
【★真实留信认证,留信网入库存档,可查悉尼大学悉尼大学毕业证offer】
我们从事工作十余年的有着丰富经验的业务顾问,熟悉海外各国大学的学制及教育体系,并且以挂科生解决毕业材料不全问题为基础,为客户量身定制1对1方案,未能毕业的回国留学生成功搭建回国顺利发展所需的桥梁。我们一直努力以高品质的教育为起点,以诚信、专业、高效、创新作为一切的行动宗旨,始终把“诚信为主、质量为本、客户第一”作为我们全部工作的出发点和归宿点。同时为海内外留学生提供大学毕业证购买、补办成绩单及各类分数修改等服务;归国认证方面,提供《留信网入库》申请、《国外学历学位认证》申请以及真实学籍办理等服务,帮助众多莘莘学子实现了一个又一个梦想。
专业服务,请勿犹豫联系我
如果您真实毕业回国,对于学历认证无从下手,请联系我,我们免费帮您递交
诚招代理:本公司诚聘当地代理人员,如果你有业余时间,或者你有同学朋友需要,有兴趣就请联系我
你赢我赢,共创双赢
你做代理,可以帮助悉尼大学同学朋友
你做代理,可以拯救悉尼大学失足青年
你做代理,可以挽救悉尼大学一个个人才
你做代理,你将是别人人生悉尼大学的转折点
你做代理,可以改变自己,改变他人,给他人和自己一个机会过暑假的小学生快乐的日子总是过得飞快山娃尚未完全认清那几位小朋友时他们却一个接一个地回家了山娃这时才恍然发现二个月的暑假已转到了尽头他的城市生活也将划上一个不很圆满的句号了值得庆幸的是山娃早记下了他们的学校和联系方式说也奇怪在山娃离城的头一天父亲居然请假陪山娃耍了一天那一天父亲陪着山娃辗转长隆水上乐园疯了一整天水上漂流高空冲浪看大马戏大凡里面有的父亲都带着他去疯一把山娃算了算这一次足足花了老爸元很
快速办理(新加坡SMU毕业证书)新加坡管理大学毕业证文凭证书一模一样

学校原件一模一样【微信:741003700 】《(新加坡SMU毕业证书)新加坡管理大学毕业证文凭证书》【微信:741003700 】学位证,留信认证(真实可查,永久存档)原件一模一样纸张工艺/offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原。
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
【主营项目】
一.毕业证【q微741003700】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【q/微741003700】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
办理新西兰奥克兰大学毕业证学位证书范本原版一模一样

原版一模一样【微信:741003700 】【新西兰奥克兰大学毕业证学位证书】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
Should Repositories Participate in the Fediverse?

Presentation for OR2024 making the case that repositories could play a part in the "fediverse" of distributed social applications
Bengaluru Dreamin' 24 - Personal Branding

Session on Personal Branding presented at Bengaluru Dreamin
Honeypots Unveiled: Proactive Defense Tactics for Cyber Security, Phoenix Sum...

Adli Wahid, Senior Internet Security Specialist at APNIC, delivered a presentation titled 'Honeypots Unveiled: Proactive Defense Tactics for Cyber Security' at the Phoenix Summit held in Dhaka, Bangladesh from 23 to 24 May 2024.
怎么办理(umiami毕业证书)美国迈阿密大学毕业证文凭证书实拍图原版一模一样

原版定制【微信:bwp0011】《(umiami毕业证书)美国迈阿密大学毕业证文凭证书》【微信:bwp0011】成绩单 、雅思、外壳、留信学历认证永久存档查询,采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信bwp0011】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信bwp0011】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
Discover the benefits of outsourcing SEO to India

"Discover the benefits of outsourcing SEO to India! From cost-effective services and expert professionals to round-the-clock work advantages, learn how your business can achieve digital success with Indian SEO solutions.
Recently uploaded (12)
Securing BGP: Operational Strategies and Best Practices for Network Defenders...

Securing BGP: Operational Strategies and Best Practices for Network Defenders...
HijackLoader Evolution: Interactive Process Hollowing

HijackLoader Evolution: Interactive Process Hollowing
Honeypots Unveiled: Proactive Defense Tactics for Cyber Security, Phoenix Sum...

Honeypots Unveiled: Proactive Defense Tactics for Cyber Security, Phoenix Sum...
Honeynet architecture
- 1. The Use of Honeynet to Detect Exploited Systems
- 2. INTRODUCTION ● One of the most active threats we face today on the Internet is cyber-crime. ● Hackers are constantly developing more sophisticated means of profiting from online criminal activity. It’s become very hard to track these hackers.
- 3. ● All your personal files,password of online accounts and other stuff which you don’t want others to have access to. ● Then….How to save your password? ● So to answer this question a group of people came forward with a network setup called “Honeynet”.
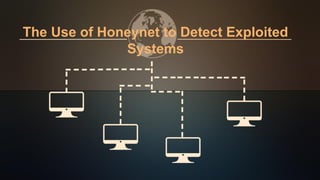
- 4. What Is Honeynet? ● A Honeynet is a network that is intended to be compromised, its purpose is to get attacked, so that an attacker’s activities and methods can be studied and this information can be used to increase the network security. ● A Honeynet is placed behind a reverse firewall. ● The reverse firewall limits the amount of malicious traffic that can leave the Honeynet. ● There are two critical principles concerning the successful operation of a Honeynet. These two principles are the
- 7. Most Targeted Operating Systems in 2013
- 8. Advantages and Disadvantages ● Data Value ● Resources ● Simplicity ● Narrow Field of View ● Risk
- 9. CONCLUSION ● Risks are part of Honeynet research and we have to manage it ● Honeynets are used to be better prepared to information system attacks. ● Honeynets can early detect new threats and issues. ● Honeynets are a source of in-depth information that classical information security system can't easily provide.
- 10. THANK YOU