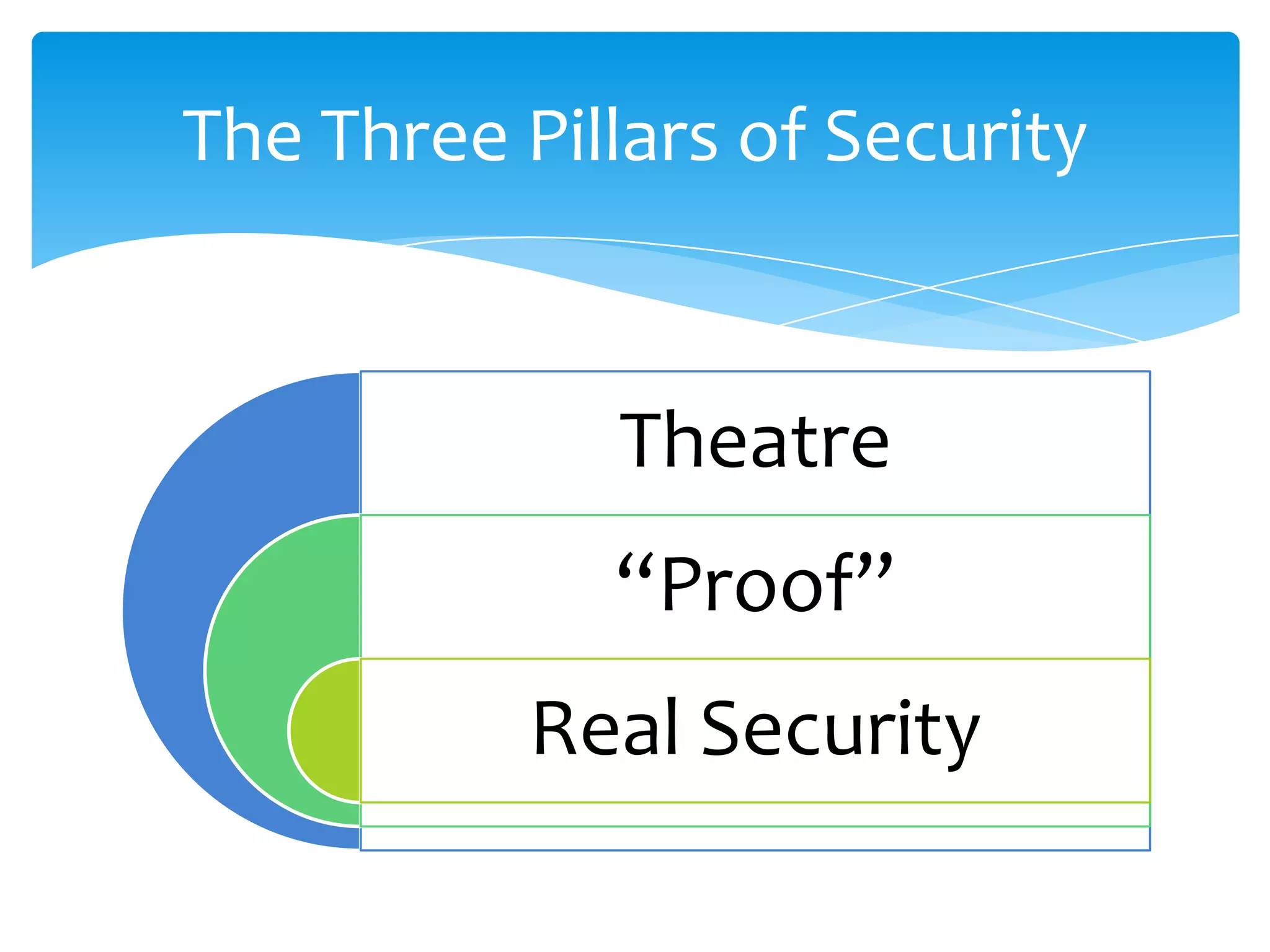
This document provides an overview of OpenStack security best practices. It discusses the three pillars of security - confidentiality, integrity, and availability. It emphasizes building security using a "defense in depth" approach across all layers of the OSI model from physical to application. Specific recommendations include controlling system access, continuous monitoring, logging, and assuming breaches will occur so systems can be forensically analyzed without impacting other users. Automation and "chaos monkey" testing are presented as ways to strengthen security.