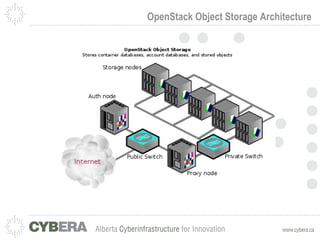
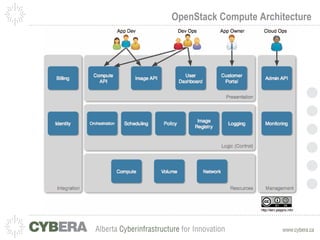
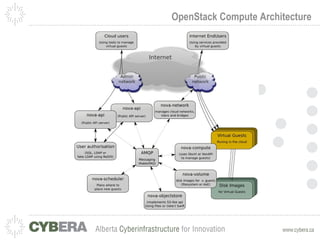
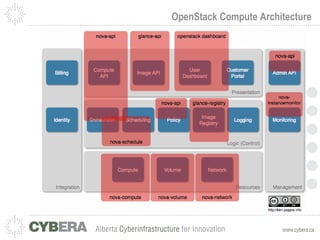
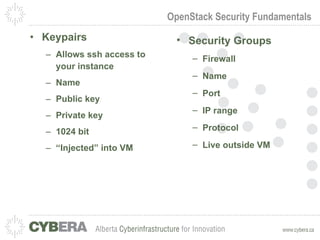
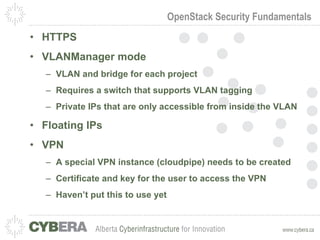
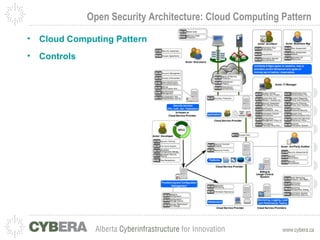
This document provides an introduction to OpenStack and discusses infrastructure as a service (IaaS). It outlines the OpenStack architecture including object storage, image service, and compute components. It also covers OpenStack security fundamentals like keypairs, security groups, and floating IPs. The document discusses IaaS security best practices and OpenStack vulnerability management. It lists some OpenStack projects and other related technologies.