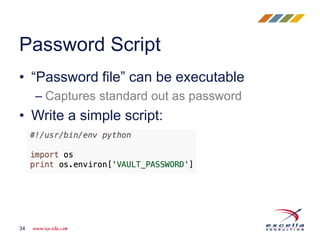
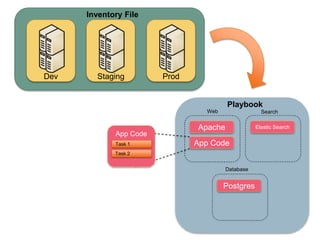
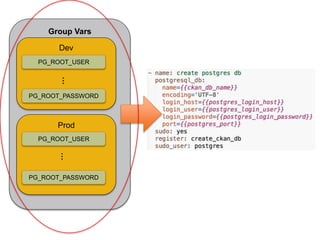
This document discusses how Ansible Vault can be used to encrypt sensitive data like passwords and private keys to protect secrets when committing infrastructure as code to source control on GitHub. It recommends encrypting only sensitive information, not all files, and splitting encrypted variable files into directories. It also provides tips for using a password script and Jenkins to automate running plays with encrypted data without exposing passwords in plain text. The document aims to help balance the security of encrypting secrets with the usability of infrastructure as code workflows.

















![• ansible-vault encrypt [filename]
How do I encrypt?
21](https://image.slidesharecdn.com/usingansiblevaulttoprotectyoursecrets-150624215058-lva1-app6891/85/Using-ansible-vault-to-protect-your-secrets-21-320.jpg)
![• ansible-playbook –i [inventory-file]
[playbook-name] --ask-vault-pass
Running w/ encrypted data
22](https://image.slidesharecdn.com/usingansiblevaulttoprotectyoursecrets-150624215058-lva1-app6891/85/Using-ansible-vault-to-protect-your-secrets-22-320.jpg)
![• ansible-vault decrypt [filename]
• ansible-vault edit [filename]
• ansible-vault rekey [filename]
Other Commands
23](https://image.slidesharecdn.com/usingansiblevaulttoprotectyoursecrets-150624215058-lva1-app6891/85/Using-ansible-vault-to-protect-your-secrets-23-320.jpg)